How to Protect Against Modern Ransomware:
Morphisec’s New Prevention Capabilities
Ransomware isn’t what it used to be.
Today’s adversaries are faster, smarter, and more creative; they’re exploiting identity, fileless execution, and novel delivery routes to bypass traditional detection.
That’s why prevention-first cybersecurity is no longer optional. With the latest enhancements to Morphisec’s platform (including protections for network shares, identity-risk mitigation, and tamper-resistant EDR) we’ve raised the bar across the entire attack kill chain.
In parallel, recent threat research from Morphisec Labs underscores how real-world attackers are pivoting to new techniques that evade legacy defenses. This isn’t theoretical. It’s happening now.
The Threat Has Changed: From Files to Identities, In-Memory, and Shared Data
- Creative Malware Delivery — In one of the latest campaigns, attackers weaponized 3D-model files (.blend) for the open-source 3D tool Blender, embedding malicious Python scripts that auto-execute upon opening. The payload: StealC V2, an advanced info-stealer targeting browsers, crypto-wallets, chat apps, and more.
- In-Memory & Fileless Attacks — These attacks don’t drop executables on disk, avoiding static analysis and many detection signatures. Instead, they execute directly in memory or leverage scripting to stay stealthy.
- C2 Frameworks & AI-Assisted Threats — Another recent example: a cyber-attack against a U.S. real-estate firm using the emerging Tuoni C2 framework. The loader exhibited signs of AI-generated code and advanced modular structure. Thanks to Morphisec’s preemptive platform, the attack was stopped before any data theft or lateral movement could occur.
These developments show the speed and ingenuity of modern adversaries and why prevention must be proactive and holistic.
What’s New in Morphisec’s Expanded Protection Stack
Morphisec’s new release isn’t just incremental. It reflects a shift into a more complete, defense-in-depth posture:
- Preemptive Network Share Protection
Attackers are increasingly targeting shared drives and network storage to maximize impact. The new controls prevent ransomware and malware from touching shared data — before execution, before encryption, before exfiltration. - Identity Risk Visibility & Abuse Prevention
Identity-driven attacks (privilege escalation, token theft, credential abuse) are among the fastest-growing attack vectors. The new identity-risk protections in Morphisec stop abuse attempts before they escalate — bridging the gap traditional identity/IAM tools leave open. - EDR Tampering & Resilience Enhancements
As threat actors lean on anti-forensic, EDR-tampering, and in-memory attack methods, detection-only tools struggle to keep up. Morphisec’s updated protections harden endpoints and security tooling against disabling, service-killing, and memory manipulation — ensuring defenses remain active when they’re needed most.
Combined, these updates form a more comprehensive “prevention stack,” addressing the modern attack kill-chain earlier than ever.
Why This Matters: Prevention Isn’t Just Better — It’s Critical
Modern ransomware campaigns aren’t just faster. They’re intentionally engineered to bypass the very detection tools organizations rely on.
Attackers are chaining identity abuse, stealthy in-memory techniques, and direct network-share encryption to maximize impact before a security alert ever fires. That’s why Morphisec’s newest protections aren’t simply “feature updates”. They represent a necessary shift toward stopping threats before they execute, not after indicators appear.
In a landscape where minutes matter and lateral movement can happen in seconds, prevention isn’t just an improvement. It’s the only reliable path to resilience. Here’s why:
- Avoid Dwell Time Pressure — By stopping attacks before they execute, Morphisec eliminates dwell time concerns and reduces reliance on detection, investigation, and response cycles.
- Lower Operational Complexity — Security teams can reduce alert fatigue and lower SOC overhead without sacrificing coverage.
- Protect Across Attack Vectors — From credential abuse to shared-drive encryption to in-memory tampering — the new capabilities cover the broad, evolving spectrum of modern threats.
- Enable Resilience & Business Continuity — Shared data, identity systems, and endpoints are often critical business infrastructure. Preemptive protection ensures ransomware attempts fail before they impact operations.
In short: detection reacts. Preemption prevents. With today’s threat sophistication, only preemptive defense offers real assurance.
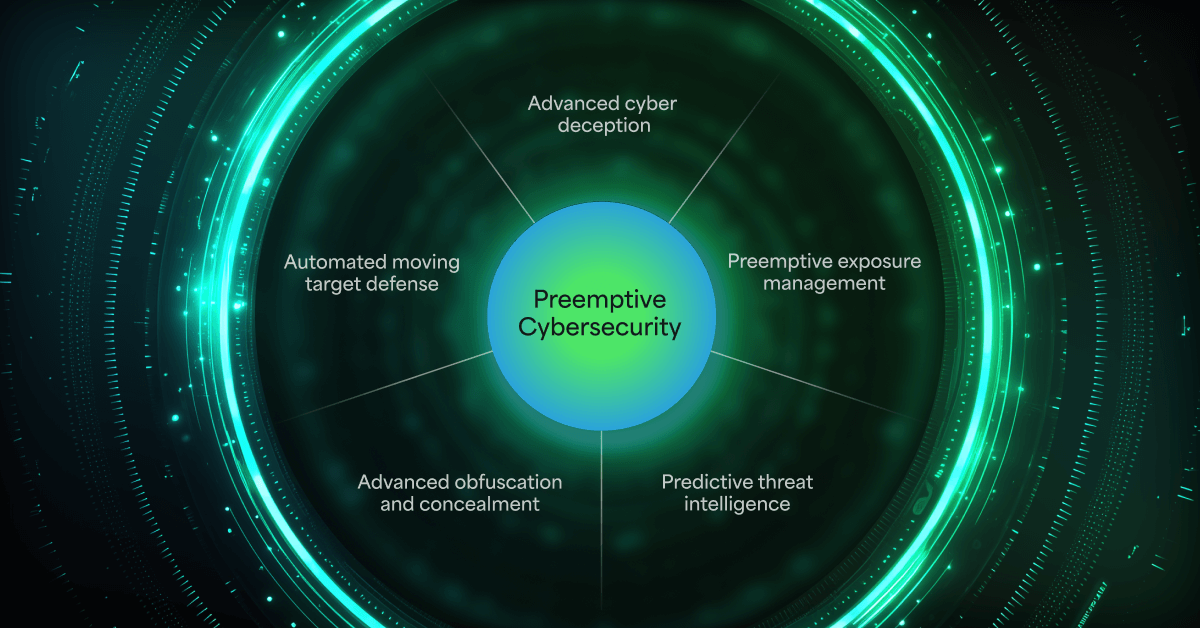
How Morphisec’s Architecture Makes It Possible
At the core: Automated Moving Target Defense (AMTD).
Rather than waiting for a known signature or behavior, AMTD continuously morphs memory and execution surfaces, disrupting attacker techniques like in-memory exploits, fileless execution, credential theft, and lateral movement in real time.
That means even novel, never-seen malware (like StealC V2 via Blender, or AI-assisted loading via Tuoni C2) is neutralized before it can touch critical systems.
Real-world examples show the difference:
- StealC V2 via Blender .blend Files — A campaign targeting 3D-artists, animators, game developers: malicious 3D models — common in marketplaces — distributed malware via embedded Python scripts. Morphisec prevented the campaign before credential theft could occur.
- Tuoni C2 Attack on a U.S. Real-Estate Firm — An advanced, in-memory C2-based attack using modular, AI-assisted loader code. Morphisec’s platform stopped it pre-execution — preventing data exfiltration, lateral movement, and potential ransomware deployment.
- General Ransomware and Fileless Attack Trends — Across the industry, adversaries are shifting to living-off-the-land, script-based, in-memory, and identity-first attacks, making reactive detection increasingly ineffective.
These are not fringe threats. They’re real, active, and evolving.
Prevention-First Security Is the Only Way Forward
If ransomware defenders are still relying on detection, signatures, or forensic response they’re already behind. The threat landscape evolves too quickly for reactive models. With this latest release, Morphisec delivers a transformed defense posture, one that stays ahead.
For security leaders, SOC teams, and CISOs asking “Is our protection future-proof?” — the answer is yes, if you adopt a prevention-first architecture that protects identity, data, endpoints, and execution surfaces — not just detect threats after they land.
Check out the full press release to learn more about Morphisec’s latest capabilities, and schedule a demo to see them in action.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.