The Top Exploited Vulnerabilities Leading to Ransomware in 2025 — and How to Stay Ahead
The attack surface isn’t shrinking — it’s exploding.
In the first half of 2025 alone, more than 23,600 vulnerabilities were published, a 16% increase over 2024. That averages nearly 130 CVEs a day. At the same time, attackers are moving faster: almost 30% of Known Exploited Vulnerabilities (KEVs) were weaponized within 24 hours of disclosure, and for high-profile edge devices the median time to exploitation was zero days.
In other words, attackers were already in before patches were available.
This relentless growth is straining even the most mature IT and security teams. Legacy patch management cycles cannot keep up with the velocity of disclosure, while overworked defenders must triage which fixes to prioritize.
The result? A widening window of exposure that ransomware actors are exploiting with ruthless efficiency.
Top Exploited Vulnerabilities in 2025
According to the 2025 Verizon Data Breach Investigations Report (DBIR), exploitation of vulnerabilities now accounts for 20% of all breaches, up 34% year-over-year. The surge is driven primarily by edge and VPN device flaws, which jumped from just 3% of exploitation cases in 2023 to 22% in 2024.
Among the most abused vulnerabilities this year:
- CVE-2024-3400 (firewalls)
- CVE-2024-21887 / 21893 (VPN appliances)
- CVE-2024-21762 (edge devices)
- CVE-2023-6548 / 6549 and CVE-2023-36844+ (Microsoft and third-party apps)
These vulnerabilities have been repeatedly weaponized in the wild—acting as gateways for ransomware groups and state-linked threat actors. For example, CVE-2024-3400 enabled remote code execution on Palo Alto firewalls (via GlobalProtect) in Operation MidnightEclipse, including use by China-nexus APTs to deploy stealthy backdoors and configuration exfiltration.
Ivanti VPN flaws (CVE-2023-46805 & 2024-21887) have been chained by espionage-linked actors like UNC5221 to push credential harvesters, backdoors, and droppers in enterprise networks. More recently, CVE-2025-22457 in Ivanti ICS was exploited to install in-memory malware and passive backdoors (TRAILBLAZE, BRUSHFIRE, SPAWN), bypassing detection entirely.
These real-world exploits illustrate how internet-facing devices remain the soft underbelly of enterprise defenses—often compromised before defenders even know there’s a threat.
Vulnerabilities as the On-Ramp to Ransomware
The correlation between vulnerability exploitation and ransomware has never been stronger.
The DBIR reports ransomware present in 44% of breaches in 2024, a 37% year-over-year jump. And in many of those cases, ransomware operators gained initial access not through phishing or stolen credentials — but through freshly weaponized vulnerabilities.
Recent high-profile incidents confirm the trend:
- Microsoft SharePoint vulnerabilities (multiple CVEs) have been exploited by Chinese-affiliated actors to deploy Warlock ransomware. More than 400 organizations, including a U.S. nuclear agency, were impacted.
- A UK telecom provider (Colt Technology Services) was compromised through CVE-2025-53770, leading to ransomware deployment and the sale of hundreds of gigabytes of stolen data.
- SonicWall SSL VPN zero-day exploitation has been linked to the Akira ransomware gang, with rapid ransomware deployments even against patched environments.
These cases show that ransomware groups increasingly prefer exploit-based access. It is faster, more scalable, and harder to detect than social engineering.
Why These Attacks Succeed
Ransomware delivered through vulnerability exploitation is especially dangerous for several reasons:
- No human error required: Unlike phishing, exploitation doesn’t rely on tricking users.
- Instant, privileged access: Exploits often deliver system- or domain-level privileges.
- Broader blast radius: One exploited zero-day can impact entire fleets of edge devices.
- Harder to detect: Exploits often drop fileless or in-memory payloads, bypassing traditional defenses.
- Patch lag: Even when fixes exist, organizations take a median of 32 days to fully remediate edge vulnerabilities — far longer than the minutes or hours attackers need.
The result is a perfect storm: attackers have more opportunities, act faster, and hit harder, while defenders are stuck playing catch-up.
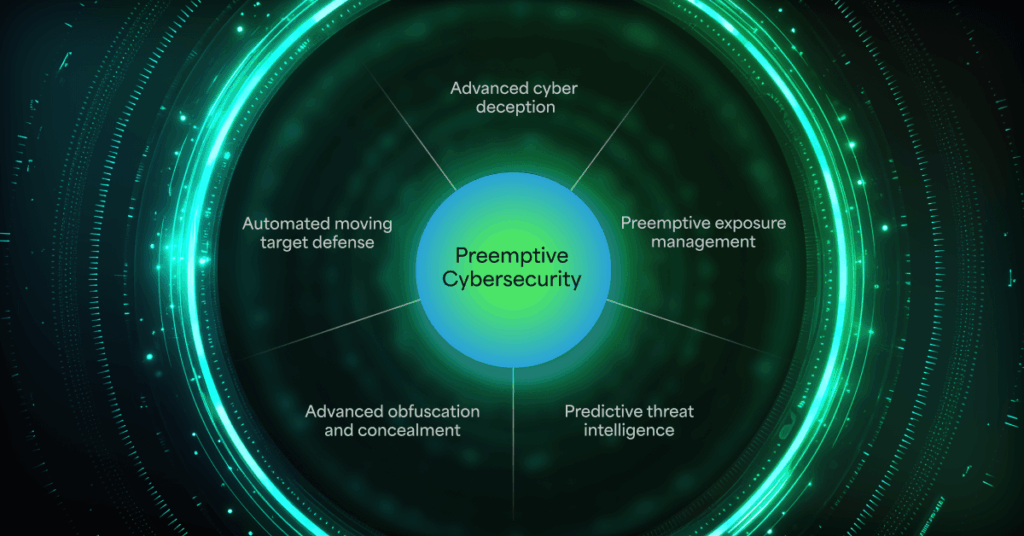
How Preemptive Cyber Defense Breaks the Cycle
Stopping ransomware at the exploit stage requires a preemptive defense, not reactive detection. That’s where Morphisec can help.
- Exploit Neutralization: Morphisec’s pioneering Automated Moving Target Defense (AMTD) technology morphs the memory runtime environment, hiding system assets and replacing them with decoys as well as other deception techniques. Exploits can’t find what they need, so they fail — regardless of signatures or patch status.
- Patchless Control: With attackers exploiting edge CVEs in zero days, AMTD buys critical time by blocking exploitation attempts, providing virtual patching, until patches can be applied.
- In-Memory Shielding: Since most exploit payloads run in memory, Morphisec protects the exact layer where ransomware loaders and shellcode operate.
- Lightweight & Universal: At just 6MB, Morphisec deploys easily across legacy systems, edge devices, and air-gapped environments that can’t run heavier endpoint agents.
- Zero Performance Impact: Fully autonomous, it adds no productivity drag — making broad adoption seamless.
By removing the attack path entirely, Morphisec ensures ransomware never gains the initial foothold that exploitation delivers.
Staying Ahead of Ransomware in 2025 and Beyond
The data is clear: ransomware is surging, and vulnerability exploitation is now its fastest and most destructive weapon.
Attackers are already exploiting zero-days before patches exist, and traditional defenses can’t keep up. Every unpatched system, every exposed edge device is a ticking time bomb. To survive this wave, organizations must act now.
Preemptive cyber defense is no longer optional — it’s the only way to stop ransomware before it detonates. With Morphisec, exploits fail on contact, ransomware never launches, and attackers are cut off before they gain a foothold.
In 2025’s threat landscape, hesitation equals compromise — decisive action is the only defense.
Book a demo to see Morphisec’s Preemptive Cyber Defense platform in action.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.