The Evolution of Cybersecurity: From Zero Trust to Preemptive Cyber Defense
Since its inception in 2009, Zero Trust Architecture (ZTA) has become a cornerstone of modern cybersecurity. Its core principle—”never trust, always verify”—has led organizations to implement strict access controls, continuous authentication, and segmentation strategies.
However, as cyber threats have grown more sophisticated, traditional security solutions have proven insufficient against advanced attack techniques like zero-day exploits, fileless malware, and ransomware.
To truly safeguard critical systems and data, organizations must embrace a more dynamic, proactive approach—Preemptive Cyber Defense powered by Automated Moving Target Defense (AMTD). This next-generation security model not only aligns with zero trust but also extends its effectiveness by neutralizing threats before they can take hold.
Why Traditional Solutions Fall Short Against Modern Threats
While traditional solutions like endpoint detection and response (EDR) play essential roles in cybersecurity, they are primarily reactive. These solutions rely on identifying known attack patterns, behavioral analysis, and historical data to detect malicious activity. The problem? Threat actors have evolved their tactics to bypass these defenses, leveraging:
- Zero-day vulnerabilities that exploit unknown software flaws
- Fileless malware that operates directly in memory to evade detection
- Evasive techniques that manipulate user credentials and exploit legitimate processes
Detection-based security solutions may miss these advanced threats, leaving organizations exposed to devastating breaches. This is where AMTD comes into play.
Introducing Automated Moving Target Defense (AMTD)
AMTD disrupts attackers by continuously altering an organization’s attack surface, making it nearly impossible for threats to land, exploit, or execute. The fundamental principle is simple: a moving target is harder to hit than a stationary one.
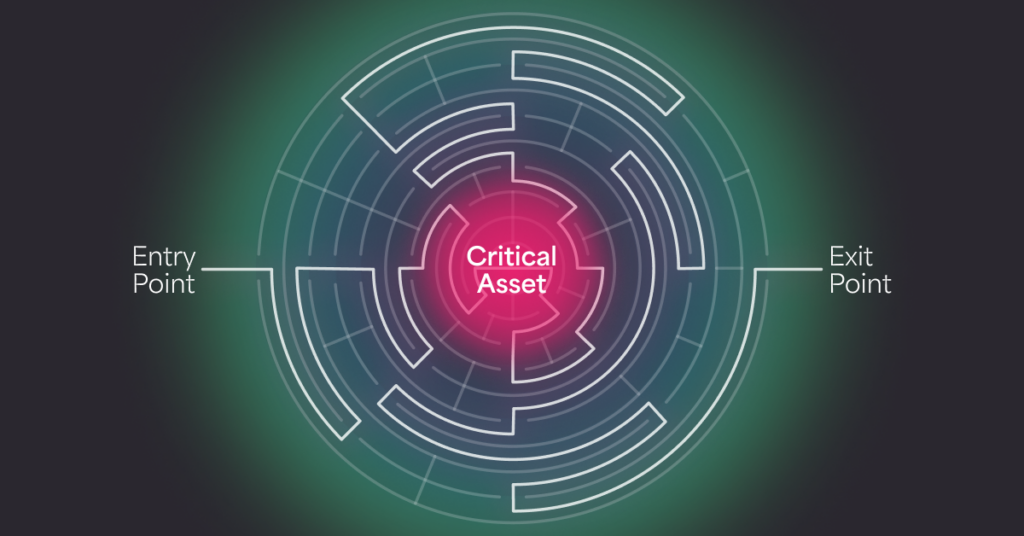
In practical terms, AMTD dynamically shifts system configurations, memory locations, and network pathways, ensuring that attackers cannot rely on static vulnerabilities to execute their attacks. Unlike traditional security measures that attempt to detect and respond to threats, AMTD prevents attacks altogether by making targets inaccessible.
AMTD vs. Traditional Security Controls
| Security Approach | Detection-Based (NGAV, EDR) | Prevention-Based (AMTD) |
|---|---|---|
| Primary Defense Mechanism | Recognizing attack patterns | Constantly changing attack surfaces |
| Effectiveness Against Zero-Day Attacks | Limited | High |
| Resource Efficiency | High CPU/memory usage | Lightweight, low overhead |
| Dependency on Threat Intelligence | Yes | No |
| Human Intervention Required | Yes (alerts, investigations) | No (fully automated) |
By incorporating AMTD into their security strategies, organizations can significantly reduce their attack surface while minimizing reliance on manual threat analysis and incident response.
How AMTD Strengthens Zero Trust Security
Zero trust establishes strict access controls, but it does not inherently prevent exploitation once attackers gain initial access. AMTD complements zero trust by:
- Preventing credential theft: If attackers breach initial authentication layers, AMTD disrupts their ability to escalate privileges or move laterally within a network.
- Neutralizing zero-day threats: AMTD dynamically morphs memory structures and application runtime environments, rendering exploits ineffective.
- Reducing attack dwell time: Instead of detecting and responding to breaches after they occur, AMTD ensures that attacks fail in real-time, preventing damage altogether.
The Future of Cyber Defense: Preemptive, Automated, and Resilient
Cybersecurity leaders must recognize that relying solely on detection-based defenses is no longer viable in today’s rapidly evolving threat landscape. Preemptive Cyber Defense—powered by AMTD—represents the next frontier in cybersecurity, shifting the focus from responding to breaches to preventing them entirely.
By integrating AMTD with a zero trust framework, organizations can achieve a truly resilient security posture that:
- Stop ransomware, fileless malware, and zero-day exploits before execution
- Reduces the need for constant security updates and patches
- Lowers operational costs by decreasing the burden on security teams
- Enhances overall cybersecurity resilience with minimal performance impact
The Time for Preemptive Cyber Defense is Now
The threat landscape is evolving, and attackers are leveraging increasingly sophisticated techniques to bypass traditional security measures. While zero trust provides an essential framework for securing access, it must be reinforced with proactive defenses like AMTD to ensure true cyber resilience.
Organizations that adopt AMTD alongside zero trust will not only stay ahead of attackers but also simplify security operations, reduce costs, and maintain business continuity in an increasingly hostile digital world. The future of cybersecurity isn’t just about detecting threats—it’s about making sure they never land in the first place.
Download the Zero Trust + Automated Moving Target Defense white paper to learn more about the evolution of zero trust, and how your organization can enhance zero trust with a preemptive approach.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.