Reduce Risk with Smarter Software Lifecycle Management
Security teams face a constant battle to maintain visibility into the vast array of software applications running across their endpoints. While organizations often have a clear understanding of where and why they are using legacy operating systems—which is typically due to business-critical dependencies or compatibility constraints—tracking the full software lifecycle of installed applications is a far more complex challenge.
The Visibility Gap: Shadow IT and Unmanaged Software
One of the biggest hurdles in software lifecycle management is the issue of shadow IT. Employees and departments often install software independently to meet immediate needs, bypassing official procurement and security vetting processes. This results in a growing number of unmanaged applications running on company devices, many of which security teams are unaware of.
The consequences of this lack of visibility are significant. Unknown or unauthorized applications can introduce security vulnerabilities, misconfigurations, or even compliance risks. Without a clear inventory of installed software, organizations struggle to detect outdated, unsupported, or potentially malicious applications that may be running on their networks. In many cases, IT and security teams only become aware of these risks when a vulnerability is exploited, or an incident occurs.
This challenge is further compounded in hybrid and remote work environments, where employees may be using personal or company-issued devices outside of traditional corporate networks. The traditional security perimeter has expanded, making it even more difficult to track software installations and ensure that only approved, up-to-date applications are in use.
The Hidden Risk of End-of-Life (EOL) Applications
Unlike operating systems, which are typically monitored for end-of-life (EOL) status due to their critical role in IT infrastructure, individual applications often fly under the radar. Software vendors regularly discontinue support for older versions of their products, meaning they no longer receive security patches or updates. Attackers actively exploit these outdated applications, knowing they represent easy entry points into corporate networks.
The challenge for security teams is twofold: identifying which applications have reached EOL and determining where they are installed. Organizations often have dozens or even hundreds of different applications deployed across their endpoints, and keeping track of their lifecycle status manually is an overwhelming task.
When unsupported software remains in use, organizations face heightened security risks, including unpatched vulnerabilities that can be leveraged in ransomware attacks, data breaches, or privilege escalation exploits. Additionally, compliance frameworks such as NIST, ISO 27001, and PCI DSS emphasize the importance of maintaining up-to-date software, meaning that EOL applications can also lead to regulatory penalties or audit failures.
Proactively Managing Software Lifecycles with Adaptive Exposure Management
For security teams, this presents a significant challenge: how can you ensure full visibility into the software running across your endpoints, identify high-risk applications, and take action to mitigate these risks?
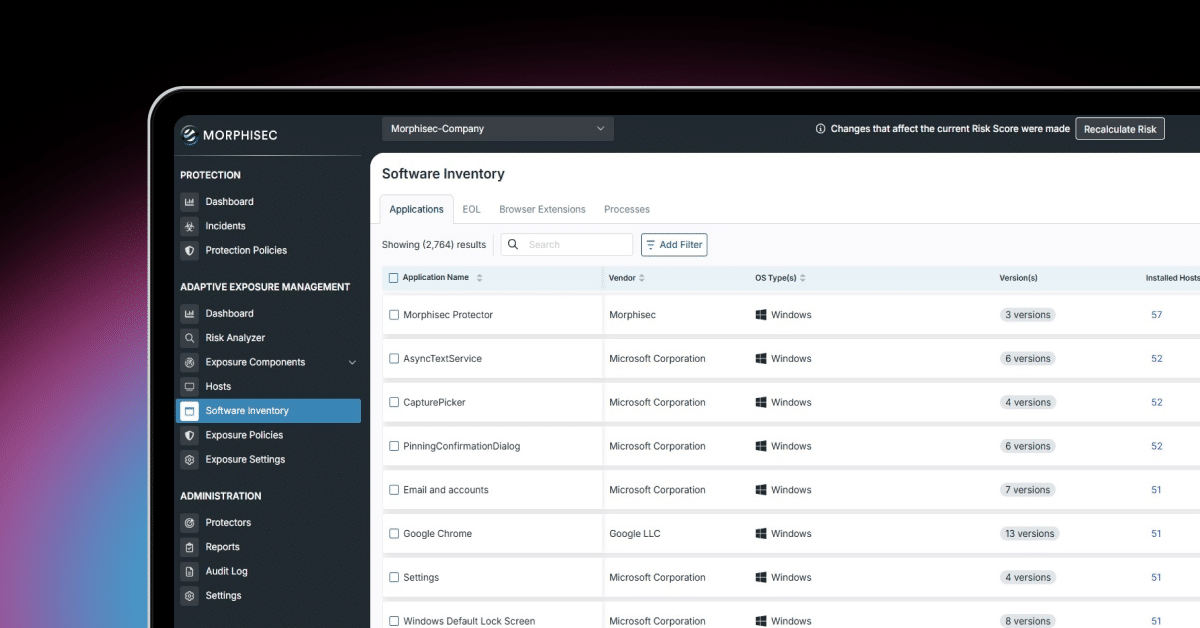
That’s where our Software Inventory feature, part of the Adaptive Exposure Management solution, comes in.
Failing to manage software lifecycles exposes organizations to:
- Increased Vulnerabilities: EOL/EOS software creates exploitable gaps in your defenses, providing attackers with easy entry points.
- Regulatory Non-Compliance: Many frameworks, including CIS Control 2, emphasize the need to actively inventory and manage software to ensure security and compliance.
- Operational Disruption: Unsupported software can cause compatibility issues, leading to downtime and inefficiencies.
For security teams, the lack of visibility into software lifecycle status can mean missed opportunities to prevent breaches and ensure compliance.
How Our Software Inventory Feature Solves These Challenges
Our Software Inventory feature provides security teams with a proactive approach to managing EOL/EOS risks.
Here’s how it works:
- Comprehensive Visibility: Automatically gather a complete inventory of software from endpoints protected by our solution, providing a centralized view of your organization’s application landscape.
- Lifecycle Tracking: Identify applications nearing or past EOL/EOS, leveraging our extensive catalogue of lifecycle data to prioritize mitigation efforts.
- Compliance Alignment: Simplify adherence to CIS Control 2 by ensuring all software is accounted for and supported, reducing audit-related headaches.
- Proactive Risk Reduction: Highlight high-risk applications and enable your team to take timely action, minimizing vulnerabilities before attackers can exploit them.
- Operational Efficiency: Save time and resources by automating the process of identifying unsupported software, allowing your team to focus on higher-value security tasks.
Staying Ahead with Adaptive Exposure Management
Outdated systems and software don’t just increase your organization’s risk—it also undermines your ability to meet compliance requirements and maintain operational resilience. By integrating our Software Inventory feature into your security processes, you can stay ahead of risks, streamline compliance, and strengthen your organization’s security posture.
Discover how Adaptive Exposure Management from Morphisec helps security teams like yours gain control over software lifecycles and reduce exposure to cyber threats. Schedule a demo today to see it in action.

Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.