How Exposure Management Powers Preemptive Cyber Defense
In today’s volatile cyber threat landscape, organizations must move beyond reactive security models and traditional detection-based tools. Threat actors are evolving faster than ever, launching attacks that are increasingly automated, stealthy, and adaptive. In response, cybersecurity strategies must evolve from proactive to preemptive—a distinction that exposure management is uniquely positioned to support.
This blog explores the shift from proactive to preemptive cybersecurity, explains how exposure management enables this shift, and highlights how Morphisec’s adaptive exposure management is designed to accelerate breach prevention.
Proactive vs. Preemptive Security: What’s the Difference?
Many security programs identify as proactive, meaning they prioritize threat anticipation, planning, and early detection. Proactive security is a step ahead of reactive security—but in the age of polymorphic malware, fileless attacks, and zero-day exploitation, being early isn’t early enough.
That’s where preemptive security comes in. A preemptive approach doesn’t just anticipate attacks; it works to eliminate the opportunity for them to succeed altogether. It’s not just about spotting risks—it’s about removing them before threat actors can exploit them.
Where proactive security is often aligned with prevention and detection, preemptive security prioritizes elimination and disruption at the earliest stage possible—even before a compromise attempt is made.
Aligning Security Strategies: Prevention vs. Detection and Response
Detection and response tools like EDRs, SIEMs, and XDR platforms are still important. They help investigate and respond to breaches once anomalies are detected. But by that point, the attacker may already be inside your environment.
On the other hand, preventative controls aim to reduce the likelihood of compromise. These include vulnerability management, application controls, segmentation, and user access policies.
Preemptive cyber defense takes prevention further. It seeks to close exposure gaps before they become attack vectors, shielding vulnerable systems from exploitation—even against unknown threats. This shift is crucial for securing today’s dynamic IT environments, where cloud workloads, remote endpoints, and third-party integrations expand the attack surface beyond traditional boundaries.
Gartner’s Perspective: Exposure Management as a Preemptive Enabler
According to Gartner, “Exposure management supports a proactive approach to cybersecurity for the modern attack surface.”1 However, Gartner goes a step further to say that as threats become more sophisticated, exposure management must accelerate the preattack cycle to effectively become preemptive.
This means exposure management must:
- Continuously discover and map the attack surface
- Identify and prioritize exposures based on real-world risk
- Accelerate mitigation actions to reduce attacker dwell time
- Automate and orchestrate remediation wherever possible
In Gartner’s words, “Preemptive exposure management is not a new technology category; rather, it represents progressive techniques for executing exposure management activities.”1 By operationalizing these techniques, security teams can transition from passive risk visibility to active risk reduction, minimizing the window of opportunity for attackers.
Gartner also notes the pace of attacker innovation: “The threat landscape is also constantly evolving… cybercriminals develop more advanced methods and technologies to automate and enhance their attacks.”1 The only viable defense is to reduce the time between exposure identification and remediation—ideally to zero.
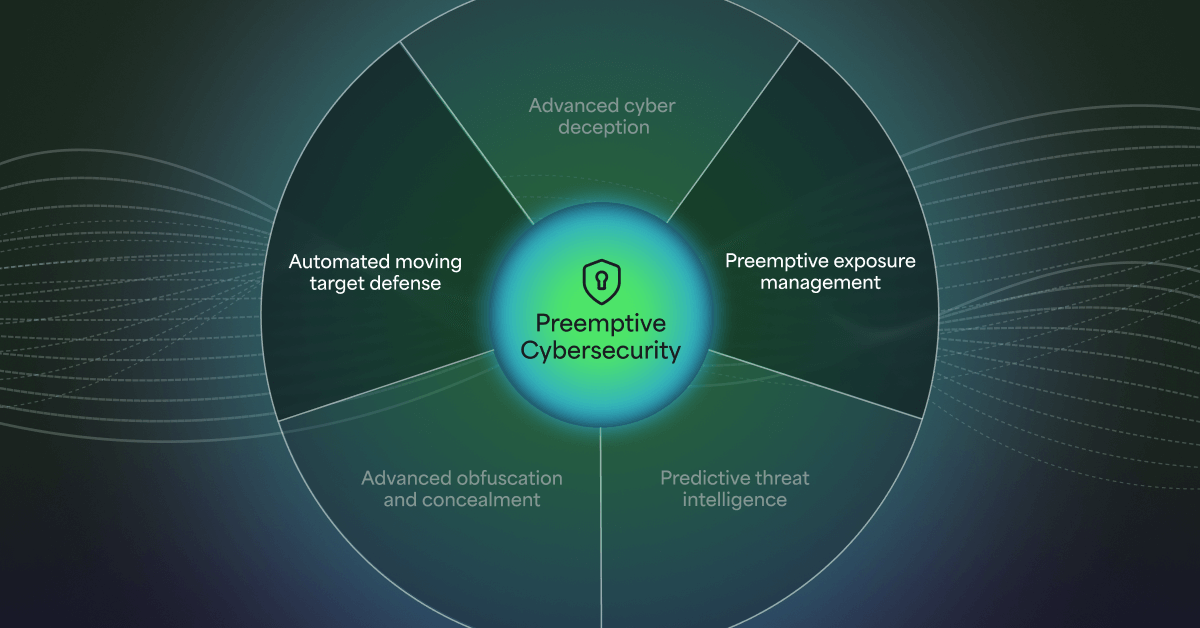
Morphisec’s Approach: Adaptive Exposure Management for Preemptive Defense
Morphisec has taken this insight to heart with its Adaptive Exposure Management capabilities, which are purpose-built to strengthen Continuous Threat Exposure Management (CTEM) programs and enable preemptive cyber defense.
Unlike traditional exposure management tools that focus only on vulnerability scanning and patch prioritization, Morphisec’s approach dynamically adjusts to real-world threat conditions, environmental context, and system behavior. It helps security teams answer the question: What are the exposures that matter most right now—and how can we neutralize them before they’re exploited?
Key capabilities include:
- Exposure-Driven Prioritization — Morphisec identifies exposures that adversaries are most likely to target, based on threat intelligence, attack paths, and exploitability. This allows security teams to focus resources on high-impact exposures rather than chasing every CVE.
- Real-Time Threat Suppression — When exposures can’t be immediately remediated, Morphisec neutralizes risk at runtime through its patented Automated Moving Target Defense (AMTD) technology. It prevents threats from executing in memory, even if they bypass traditional controls or exploit unknown vulnerabilities.
- Deception-Based Threat Visibility —By deploying decoys in vulnerable environments, Morphisec exposes attacker behavior early in the intrusion lifecycle—before data exfiltration or lateral movement. This enables faster and more informed mitigation actions.
- Automated Mitigation and Orchestration — Morphisec accelerates the exposure-to-remediation cycle by integrating with EDRs, SIEMs, and ticketing systems to automate alerts, policy enforcement, and incident response actions—reducing manual effort and response time.
From Exposure Visibility to Exposure Elimination
To achieve a preemptive cybersecurity posture, organizations need to evolve their exposure management practices beyond visibility. They must actively reduce the attack surface, harden high-risk assets, and block exploitation paths, before adversaries strike.
Morphisec’s adaptive approach delivers exactly that: accelerated, contextual, and automated exposure management that aligns with Gartner’s vision of preemptive defense.
In a world where threats mutate in real time, static visibility is no longer enough. The future of cyber defense belongs to platforms that can see exposures in motion, anticipate how they’ll be exploited, and prevent them from becoming breaches.
Preemptive cybersecurity isn’t about reacting faster—it’s about eliminating the need to react at all. Exposure management plays a critical role in that mission, but only if it evolves to meet the speed and sophistication of today’s attackers.
By reducing the time from exposure identification to mitigation, and by shielding systems from exploitation even in the presence of known or unknown vulnerabilities, Morphisec’s Adaptive Exposure Management helps organizations close the gap between visibility and action.
It’s time to stop playing catch-up with attackers. With preemptive cyber defense powered by adaptive exposure management, you can get ahead—and stay there. Check out this demo video to see Morphisec Adaptive Exposure Management in action.
1 Gartner, Quick Answer: How Does Exposure Management Support Preemptive Cybersecurity?, Luis Castillo, 25 November 2024
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.