Identity Risk Visibility: The Next Frontier in Preemptive Cyber Defense
In today’s threat landscape, identity has become the new perimeter.
Adversaries no longer rely on brute force to gain entry — they exploit credentials, permissions, and trust. From stolen admin passwords to overprivileged accounts and insecure Active Directory settings, attackers move silently through identity blind spots that most organizations can’t see.
The result? Ransomware and data exfiltration campaigns that bypass traditional detection layers entirely.
Morphisec’s latest innovation changes that equation. With the introduction of Identity Risk Visibility capabilities, organizations can now uncover and proactively mitigate the identity weaknesses that attackers exploit — before they’re used against them.
You Can’t Protect What You Can’t See
Most organizations struggle to answer a critical question: Which accounts in my environment pose the greatest risk?
Without visibility into the identities that have excessive privileges, stale configurations, or exposure to attack paths, the identity perimeter remains porous. Orphaned accounts, misconfigured service identities, and privilege creep give attackers easy lateral movement opportunities once they compromise a single endpoint.
Identity-centric attacks now account for the majority of breaches — yet many security teams still lack a clear view of who has access to what, and why.
That’s where identity risk visibility becomes essential.
Why Identity Risk Visibility Matters More Than Ever
The rise of hybrid environments, remote work, and cloud services has multiplied both human and machine identities. Each represents a potential access point.
If you can’t visualize or measure identity risk, you can’t enforce least privilege or detect anomalous access early enough to stop an intrusion.
Visibility delivers:
- Faster prioritization: Pinpoint high-risk accounts before attackers do.
- Stronger prevention: Harden identity posture by addressing privilege misuse and insecure configurations.
- Simpler compliance: Maintain auditable records of user access and identity hygiene.
- Smarter defense: Empower your security team to act with context — not guesswork.
Identity visibility isn’t a nice-to-have. It’s a foundational layer of Zero Trust — and now, a cornerstone of preemptive cyber defense.
Introducing Morphisec Identity Risk Visibility
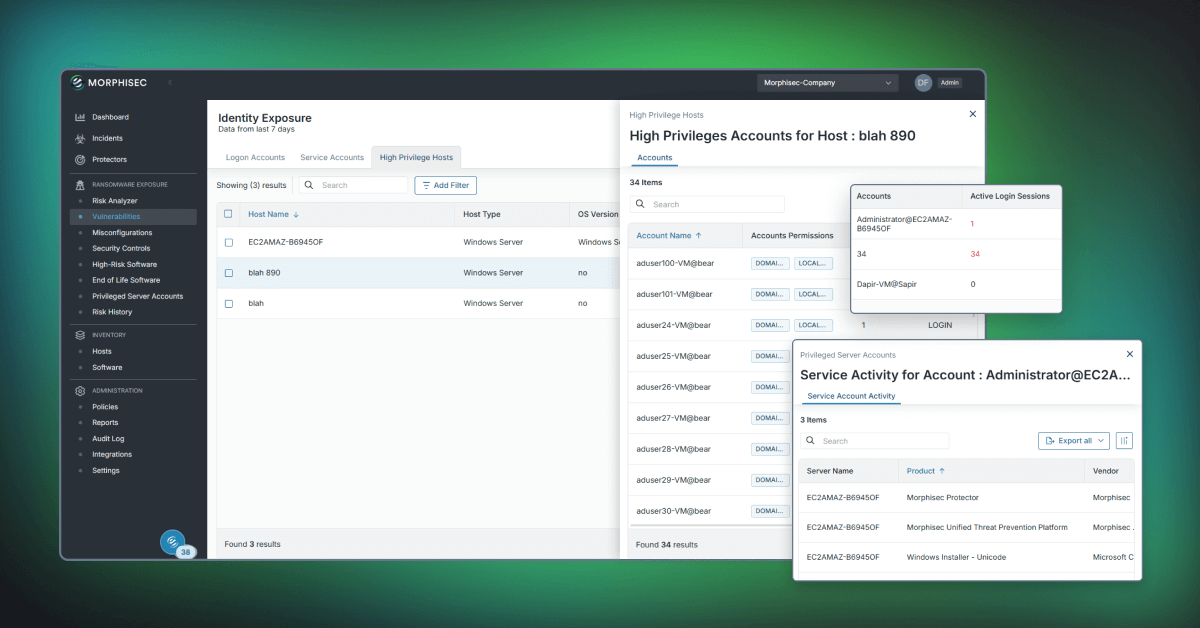
Morphisec’s new Identity Risk Visibility feature provides crucial insight into the user accounts that pose the greatest risk to your organization, allowing you to proactively harden your identity perimeter against attack.
Here’s how:
- Identify Your Most Targeted and Vulnerable Accounts
Gain a new dimension of visibility by automatically pinpointing which user accounts are most likely to be targeted or compromised.
Morphisec identifies accounts with excessive privileges, insecure configurations, and other weaknesses that attackers actively seek to exploit for credential theft and lateral movement.
This real-time visibility helps defenders see what attackers see — and act before exploitation occurs. - Proactively Harden Your Defenses to Prevent Breaches
Move beyond reactive credential response. Morphisec provides actionable guidance to fix the root causes of identity risk — from stale accounts to over-privileged users — so you can remediate issues before attackers weaponize them.
The result is a hardened identity environment where ransomware campaigns struggle to gain traction. - Accelerate Your Zero Trust Journey with Actionable Guidance
Zero Trust begins with least privilege — and least privilege begins with visibility.
Morphisec delivers prioritized recommendations that empower your IT and Security teams to:- Enforce least privilege policies
- Improve Active Directory hygiene
- Strengthen authentication controls
- Take foundational steps toward a Zero Trust architecture
With Morphisec, identity defense becomes both visible and actionable.
Extending Preemptive Defense to the Identity Layer
Morphisec’s platform already stops advanced threats and fileless attacks at the endpoint.
Now, with identity risk visibility, preemptive defense extends to the human layer — the most frequently exploited vector in the enterprise.
By integrating identity insights into the same prevention-first framework, Morphisec gives security leaders the clarity to:
- Expose identity risks before they’re exploited
- Strengthen posture across hybrid and cloud environments
- Reduce time to harden identity controls from weeks to hours
It’s a natural evolution of preemptive cyber defense: stopping attackers whether they try to breach your system or compromise your identity.
See. Act. Prevent.
Identity risk visibility delivers what every CISO needs most — speed, clarity, and confidence.
With Morphisec, you gain the visibility to see your riskiest accounts, the insight to act decisively, and the power to prevent breaches before they start.
Because preemptive defense starts with knowing where you’re most exposed — and eliminating that exposure before attackers can exploit it.
Book a personalized demo to see Morphisec Identity Risk Visibility in action and learn how you can harden your identity perimeter and accelerate your Zero Trust journey.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.