See the Whole Story: How Event Analysis Helps You Strengthen Security Posture and Prove ROI
In cybersecurity, visibility is power. Yet most organizations still operate in a reactive cycle — detecting, triaging and remediating threats as they appear, without the historical context to understand why they occurred or how to prevent them from happening again.
This is where Morphisec’s Event Analysis capability changes the game. By connecting every point in the incident lifecycle — from discovery to remediation — it gives defenders the historical insight they need to transform reactive risk management into proactive security posture improvement.
The Challenge: Security Teams Are Drowning in Data but Starved for Context
Modern enterprises generate vast amounts of security telemetry: endpoint alerts, vulnerability findings, threat intelligence feeds, log data and user activity trails. The problem isn’t data scarcity — it’s fragmentation.
Without historical visibility, analysts often investigate each alert in isolation. They can see what happened, but not why.
They patch vulnerabilities but can’t verify whether the fix eliminated the root cause. They respond to incidents but lack the context to recognize recurring patterns.
This creates an operational blind spot — one that attackers exploit. By using stealthy, living-off-the-land techniques and deception of their own, they take advantage of defenders’ short-term memory.
Over time, organizations fall into a cycle of reaction instead of evolution.
The Shift: From Incident Response to Posture Improvement
Industry frameworks like NIST CSF 2.0 and Gartner’s Preemptive Cybersecurity model emphasize one essential truth: security posture improvement is a continuous discipline, not a one-time event.
Every incident offers insight. Every anomaly reveals an opportunity to strengthen defenses. But that’s only possible when teams have the right tools to capture and analyze historical context.
Best practices alone aren’t enough. They must be supported by data that proves progress, validates remediation efforts, and informs the next step forward. That’s where Morphisec’s Event Analysis capabilities deliver exceptional value.
Introducing Morphisec Event Analysis: Turning Data into Defense
Event Analysis equips defenders with the full story behind every event — connecting “before,” “during,” and “after” into a single, auditable timeline. It’s not just about seeing threats; it’s about understanding their lifecycle and impact.
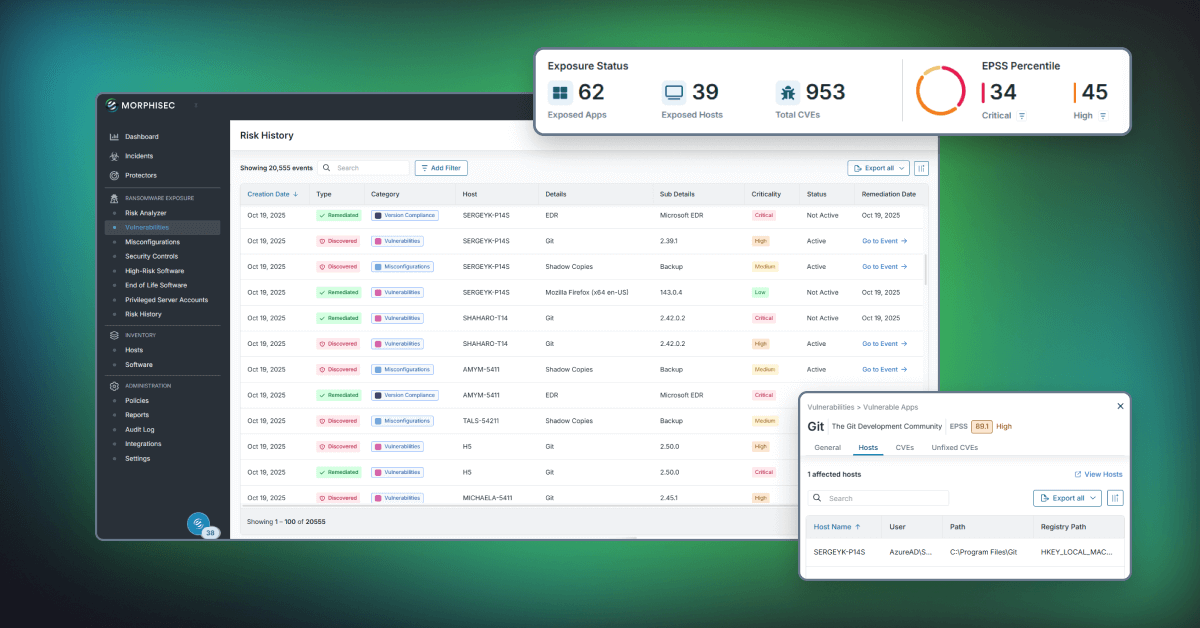
Accelerate Investigations with Historical Context — With Event Analysis, analysts can trace any risk event from discovery through remediation. This end-to-end audit trail allows them to:
- Identify root causes in minutes, not days.
- Detect recurring weaknesses across users, systems, or configurations.
- Validate that corrective actions were effective.
This level of context transforms investigations. It shifts response workflows from guesswork to certainty, shortening Mean Time to Investigate (MTTI) and Mean Time to Respond (MTTR) — and enabling teams to learn faster than adversaries adapt.
Demonstrate Security Program ROI — Security leaders need more than dashboards — they need proof. Event Analysis provides the historical evidence required to demonstrate measurable progress.
The Risk History module captures every risk reduction milestone, giving CISOs and security managers the data-driven narrative they need to:
- Quantify the value of their exposure management strategy.
- Justify future investments in prevention and hardening initiatives.
- Simplify compliance and audit reporting with easy data exports.
This is where operational improvement meets business alignment — where technical teams and executives share a unified, data-backed story of risk reduction.
Why It Matters: Event Analysis Powers Preemptive Cyber Defense
Morphisec’s philosophy has always been built on preemptive cyber defense — preventing attacks before they cause damage. Event Analysis extends that principle into the realm of security posture optimization.
By giving teams the ability to identify patterns and validate improvements over time, Event Analysis helps organizations:
- Predict where future risks are most likely to emerge.
- Prioritize fixes that deliver the highest risk reduction.
- Strengthen systems before attackers can exploit them.
In other words, it enables defenders to act before the next compromise, not after, turning every past event into an opportunity for future prevention.
The Bigger Picture: A Continuous Loop of Learning and Improvement
Security posture improvement isn’t static — it’s cyclical. The organizations that thrive are those that build feedback loops into their security operations: detect, analyze, improve, validate, repeat.
With Morphisec’s Event Analysis, every investigation becomes a learning experience. Every remediation becomes measurable progress. And every audit becomes a story of resilience backed by proof.
Morphisec gives you the visibility to see where you’ve been, the insight to understand why and the control to stay ahead of what’s next. Move beyond reactive incident response. Gain the historical context and data-driven insight to continuously strengthen your defenses.
Book a demo to see how Morphisec’s Event Analysis (as part of the Anti-Ransomware Assurance Suite) can help your team measure, prove, and improve security posture with confidence.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.