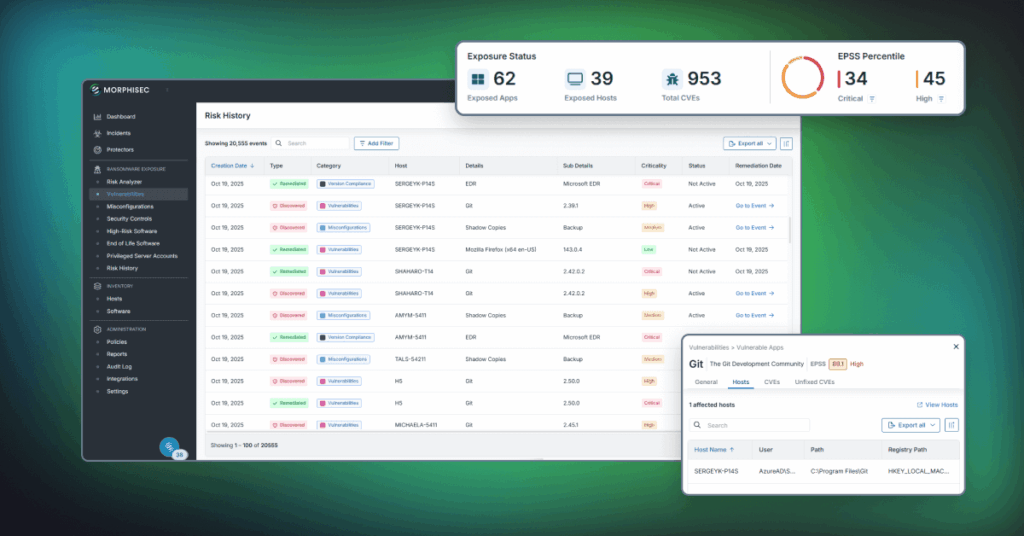
The Most Overlooked Rule in Cyber Survival: Stop Ransomware Before It Starts
Ransomware is no longer just about brute force encryption.
According to the 2025 Verizon Data Breach Investigations Report (DBIR), malware and ransomware families are evolving into masters of disguise. They now rely on stealth, obfuscation, and deception to infiltrate networks, evade defenses and execute attacks before defenders can react.
From infostealers quietly harvesting credentials to ransomware loaders hiding inside legitimate traffic channels, attackers are innovating faster than traditional security controls can adapt.
For organizations, the reality is clear: ransomware has become a silent intruder rather than a noisy disruptor. Detection alone is no longer enough—you need to stop ransomware before it starts.
Deceptive Malware Tactics: Insights from the DBIR
The DBIR outlines several disturbing trends showing how ransomware and malware increasingly lean on deception:
- Stealthy Command-and-Control: Ransomware families like Black Basta are linked to loaders such as Zloader that now use DNS tunneling to mask their command-and-control activity, blending malicious traffic with normal DNS lookups to remain invisible.
- Advanced Evasion in Commodity Malware: Variants like Nova Snake Keylogger employ sophisticated evasion tactics that allow them to slip past endpoint detection tools and operate undetected.
- Credential Laundering via Infostealers: DBIR analysis shows that compromised enterprise logins often come from infostealer malware, which mixes corporate and personal credentials on unmanaged devices. Attackers then sell these access points, creating a deceptive appearance of “legitimate” logins before launching ransomware campaigns.
- Living-off-the-Land & Rogue Infrastructure: Adversaries are leveraging trusted tools (like PowerShell) and even spinning up rogue virtual machines directly on hypervisors—a tactic designed to operate beneath the visibility of security monitoring.
Together, these tactics create a fog of war where attackers conceal malicious activity within legitimate processes, networks, and credentials. The outcome? Security teams face longer dwell times, higher detection complexity and an increased likelihood of ransomware “detonation” before discovery.
Real-World Breaches Driven by Deception
Recent incidents illustrate just how central deception has become to modern malware and ransomware campaigns.
Take the Zloader example, a long-running malware family recently linked to Black Basta ransomware operations. Its newest variants have introduced custom DNS tunneling to disguise command-and-control traffic as ordinary DNS lookups. To the untrained eye—and even to many security tools—this traffic looks benign, allowing attackers to quietly establish persistence and prepare the ground for ransomware deployment without detection.
Similar stealth tactics were on display in the ArcaneDoor campaign, where state-sponsored actors planted custom implants on Cisco ASA and Firepower firewalls. By targeting security appliances themselves, the attackers effectively operated from a blind spot—an area where endpoint and network monitoring solutions often have little visibility. This use of compromised edge devices demonstrates how attackers deliberately hide in plain sight, exploiting the very tools designed to defend the enterprise.
The Volt Typhoon campaign targeting U.S. critical infrastructure followed this same playbook, leaning heavily on legitimate system utilities and administrator credentials to move quietly through victim environments. This approach allowed attackers to maintain long-term access while avoiding the kinds of red flags that detection-based tools typically rely on.
Similarly, the SocGholish malware campaign has continued to wreak havoc by luring victims with convincing fake browser-update prompts. Once inside, the malware adapts to the environment and can deliver ransomware payloads like RansomHub while evading traditional antivirus and email filters.
Across all of these cases, the common theme is not brute force but stealth. Attackers are mastering the art of looking legitimate, embedding themselves into environments where they appear to belong and using deceptive tactics to delay detection until it is too late.
For defenders, these examples make one point clear: organizations cannot rely solely on detection. They need preemptive capabilities that neutralize ransomware and malware before these deceptive tactics ever have a chance to succeed.
Gartner’s Take: Cyber Deception as a Countermeasure
Gartner consistently points to Advanced Ccyber Ddeception (ACD) as a critical technology for turning the tables on attackers.
Instead of waiting for malware to reveal itself, ACD solutions create a cyber minefield of fake assets—servers, networks, data repositories, and accounts—that mimic real systems. Attackers are drawn into these decoys, where their actions trigger early alerts and expose their tactics in real time.
According to Gartner1:
- Adaptive decoys can change appearance based on attacker behavior, making it nearly impossible for adversaries to distinguish real from fake.
- High-fidelity threat intelligence is generated by observing attackers in the decoys, giving defenders valuable insights while eliminating false positives.
- Operational resilience improves because defenders gain back critical time, reduce overall costs, and strengthen their defenses with immediate, actionable intelligence.
The technology is maturing quickly, with adoption accelerating in sectors like financial services, healthcare, energy, and government—industries where operational disruptions can cause catastrophic consequences.
Morphisec: Preempting Ransomware with Deception
This is where Morphisec’s Automated Moving Target Defense (AMTD) technology provides a decisive advantage. Unlike traditional deception tools that rely solely on decoys, Morphisec shifts the attack surface itself, preventing attackers from gaining an initial foothold.
By constantly morphing the memory and runtime environment, AMTD ensures that malicious code, no matter how stealthy or deceptive, cannot execute as intended.
Through its Anti-Ransomware Assurance Suite, Morphisec provides a comprehensive platform that preemptively blocks ransomware before it can encrypt files, exfiltrate data, or disrupt operations.
The platform features:
- Automated Moving Target Defense to deny attackers any stable ground.
- High-fidelity, zero false positive prevention that stops threats without creating alert fatigue.
- Protection against fileless malware, zero-days, and advanced ransomware families that evade detection-based solutions.
For enterprises under pressure from stealthy ransomware, this approach delivers what detection alone cannot: certainty that ransomware is stopped before it starts.
Don’t Play the Attacker’s Game
Attackers are mastering deception.
The DBIR shows that stealth is now central to the ransomware playbook, while Gartner highlights deception as the most effective countermeasure. Organizations that continue to rely only on detection are playing catch-up against adversaries who are already inside.
With Morphisec, you flip the equation—deception becomes your defense, and ransomware has nowhere left to hide.
Get a complimentary copy of the Gartner® Hype Cycle for Workspace Security, 2025 report to learn more about emerging deception technologies like AMTD and steps your team can take to stop threats from taking root.
1Gartner. Emerging Tech: Tech Innovators in Preemptive Cybersecurity. Luis Castillo, Isy Bangurah. 8 January 2025.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.