Preemptive Cyber Defense Platform
Morphisec’s Anti-Ransomware Assurances Suite provides multi-layered protection for endpoints to proactively prevent ransomware and advanced cyber attacks.
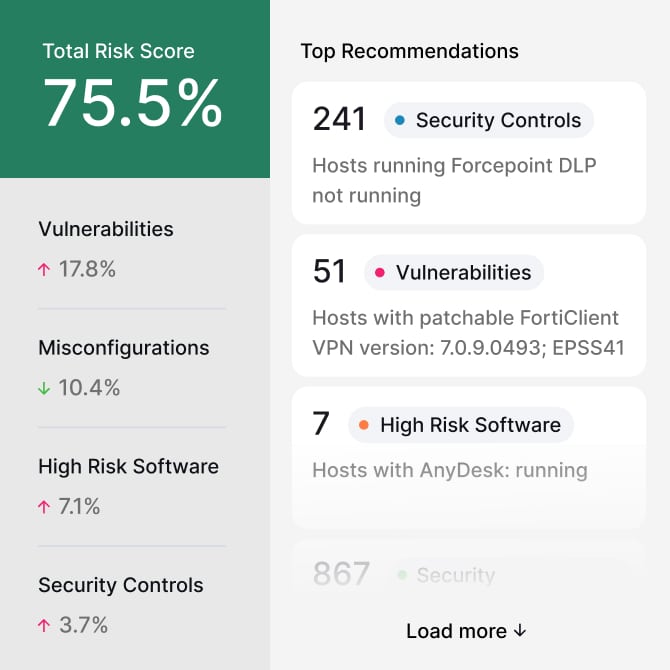
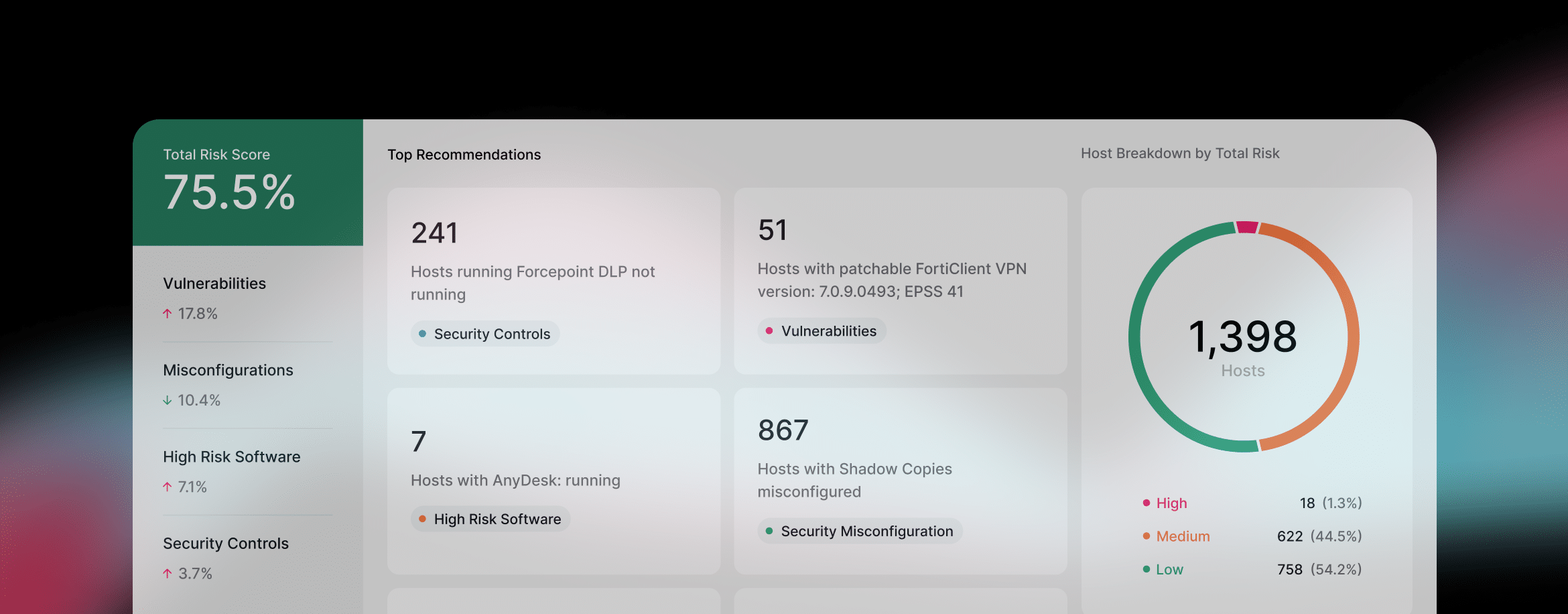
Identify your risks
Adaptive Exposure Management elevates your security posture by prioritizing vulnerabilities, automating the assessment of your security controls, identifying high-risk software and addressing security misconfigurations.
- Vulnerability Prioritization
- Security Misconfigurations
- High-Risk Software
- EOL Support
- Privileged Accounts Risk
- Security Controls Validation
- Software Inventory
- Analyze Risk
- Browser Extensions
Prevent attacks early
Infiltration Protection enhances your organization’s cyber resiliency by continually changing the attack surface, rendering the target unpredictable and harder for attackers to exploit.
- Runtime Memory Protection
- Credential Theft Protection
- Exfiltration Protection
- Privilege Escalation Protection
- Hacking Tool Protection
Stop ransomware from executing
Impact Protection proactively defends critical assets and data, minimizing recovery times and strengthening your anti-ransomware stance.
- Tamper Protection
- Wiping Protection
- Data Encryption Protection
Recover with ease
Adaptive Recovery both ensures encrypted files are restored quickly by intercepting encryption keys in real-time and preserves critical forensic data in tamper-proof storage, enabling fast incident investigation and comprehensive recovery.
- Forensic Recovery
- Data Recovery
Achieve Adaptive Cyber Resiliency with Morphisec — ensures that cybersecurity measures evolve in alignment with both technological advancements and emerging threat landscapes, establishing a robust defense mechanism that promotes sustained and continuous security and trust.
Identify your risks
Vulnerability prioritization
Remediation recommendations
Leverage next-generation vulnerability prioritization and streamline patch management efforts.
Data and analytics on your biggest threats
Morphisec goes beyond CVSS to prioritize vulnerabilities and focus resources on the greatest threats, including contextual data of your company’s actual exposure, and analytics including EPSS and CISA KEV listing.
Security controls validation
Continuous monitoring
Continuously monitor endpoint protection solutions to ensure they are operational and functioning as intended.
Security controls assessment
Automated and continuous security controls assessment provides assurance that your security software is deployed, in use, and properly configured to protect your organization.
Security misconfigurations
Identify misconfigurations
Regularly check for misconfiguration within endpoint protection solutions that could lead to vulnerabilities.
Automate and prioritize
Automate the identification and prioritization of configurations not in compliance with your security policies.
Software inventory
Enhance visibility
Track installed software versions and their hosts and identify outdated or unsupported software.
Simplify compliance
Align your software management practices with recognized cybersecurity frameworks, including CIS Control 2.
High-risk software
Identify high-risk software
Identify high-risk software active on endpoints, abuse of which can lead to compromising security.
Score and prioritize
Access cyber risk scores to help security and IT teams prioritize remediation efforts.
Risk analyzer
Understand your risk
Continually and dynamically aggregates a risk score representing the organization’s security exposure, while recommending remediation actions.
Personalized risk score
Risk analyzer provides a single, cyber risk score based upon business context, usage-based insights, and core adaptive exposure management elements.
Remediation recommendations
Leverage next-generation vulnerability prioritization and streamline patch management efforts.
Data and analytics on your biggest threats
Morphisec goes beyond CVSS to prioritize vulnerabilities and focus resources on the greatest threats, including contextual data of your company’s actual exposure, and analytics including EPSS and CISA KEV listing.
Continuous monitoring
Continuously monitor endpoint protection solutions to ensure they are operational and functioning as intended.
Security controls assessment
Automated and continuous security controls assessment provides assurance that your security software is deployed, in use, and properly configured to protect your organization.
Identify misconfigurations
Regularly check for misconfiguration within endpoint protection solutions that could lead to vulnerabilities.
Automate and prioritize
Automate the identification and prioritization of configurations not in compliance with your security policies.
Enhance visibility
Track installed software versions and their hosts and identify outdated or unsupported software.
Simplify compliance
Align your software management practices with recognized cybersecurity frameworks, including CIS Control 2.
Identify high-risk software
Identify high-risk software active on endpoints, abuse of which can lead to compromising security.
Score and prioritize
Access cyber risk scores to help security and IT teams prioritize remediation efforts.
Understand your risk
Continually and dynamically aggregates a risk score representing the organization’s security exposure, while recommending remediation actions.
Personalized risk score
Risk analyzer provides a single, cyber risk score based upon business context, usage-based insights, and core adaptive exposure management elements.
Prevent attacks early
Prevent ransomware early with Automated Moving Target Defense (AMTD) that makes it harder for attackers to exploit vulnerabilities.
Memory protection
Morphisec alters the memory, providing true proactive prevention against fileless threats that EDR solutions cannot actively stop. AMTD continually changes the attack surface, rendering the target unpredictable, making it harder for attackers to exploit vulnerabilities.
Privilege escalation protection
We thwart attempts to bypass User Account Control (UAC) using registry and Component Object Model (COM) object manipulation, thus stopping attackers from gaining elevated system access.
Credential theft protection
We provide deterministic protection for user credentials stored in Chromium-based browsers and blocks credential dumps from various hashes. Unauthorized processes trying to access system credentials are automatically terminated.
Hacking tool protection
We block tools like PsExec and Mimikatz that are known for aiding attackers in lateral movement and further exploitation after the initial breach. We also neutralize sophisticated backdoors and penetration tools to prevent persistent access and control over compromised systems.
Exfiltration protection
Morphisec neutralizes ransomware payloads, blocks unauthorized access, preserves recovery tools, and disrupts exfiltration via cloud services, scripts, and command-and-control channels to prevent attackers from gaining leverage and exacerbating disruption.
IMPACT PROTECTION
Stop ransomware from executing
Safeguard your systems when ransomware attempts to execute by protecting critical assets and files, minimizing recovery times, and fortifying your anti-ransomware stance.
Attack surface randomization
AMTD dynamically reshapes the attack surface, making critical assets unpredictable and inaccessible to attackers, drastically reducing their ability to exploit vulnerabilities.
In-memory protection
AMTD safeguards runtime memory by preventing unauthorized code injections, blocking advanced threats like ransomware and zero-day attacks before they can execute.
Try Morphisec for yourself
Take a free, self-guided tour of the platform and experience all that Morphisec has to offer.
Preemptive Cyber Defense
Morphisec’s prevention-first approach stops advanced attacks, reduces your attack surface, and ensures adaptive cyber resiliency.
Ransomware Prevention
Prevent ransomware, protect financial assets, and ensure resiliency with proactive prevention and visibility across the MITRE ATT&CK chain.
Efficiency & Cost Savings
Reduce costs by 30% and investigation time by 65% with our lightweight agent, delivering 90% fewer false positives and faster incident mitigation.
ADAPTIVE RECOVERY
Recover encrypted files with ease
Strengthen your incident response. Secure critical forensic data in tamper-proof storage and capture key evidence like logs and attacker footprints in real-time to ensure fast investigation, compliance with industry standards, and improved defenses against future threats.

Forensic Recovery
Strengthen your incident response with Forensic Recovery, which secures critical forensic data in tamper-proof storage. Capture key evidence like logs and attacker footprints in real-time to ensure fast investigations, compliance with industry standards, and improved defenses against future threats.
Data Recovery
Eliminate downtime with Data Recovery, which restores encrypted files instantly by intercepting encryption keys during ransomware execution. No need for backups or ransom payments—just seamless, automated recovery to keep your business running.
Augment your security stack
Morphisec works with any EDR to stop the unknown attacks that bypass your existing security stack.
Purpose-built for your OS
Morphisec delivers advanced ransomware prevention for both Windows and Linux environments. While most solutions focus solely on Windows, our Linux protection is purpose-built to secure critical workloads with the same prevention-first approach—no disruption, just powerful defense where it’s needed most.

INCIDENT RESPONSE SERVICES
Experts Here
for You
The Morphisec Incident Response Team works collaboratively with client organizations to triage critical security incidents and conduct forensic analysis to solve immediate cyberattacks as well as provide recommendations for reducing your organization’s risk exposure.

Our team will help contain in-progress incidents and reduce damage.
We’ll provide recommendations for long-term risk reduction.
We’ll audit critical infrastructure to minimize the risk of cyber attacks.
Featured resources
Adapt, protect, and defend with Anti-Ransomware Assurance
Stop ransomware today with proven Preemptive Cyber Defense by Morphisec.