Why Endpoint Security Needs a Rethink: From Reactive to Preemptive Defense
In today’s threat landscape, the endpoint is under siege—and the traditional playbook for securing it is falling short.
The 2025 Verizon Data Breach Investigations Report (DBIR) paints a stark picture: nearly half of all breaches now involve ransomware, and endpoint compromise via stolen credentials, phishing, and unpatched vulnerabilities remains rampant. The complexity and frequency of these attacks make one thing abundantly clear—reactive endpoint detection and response (EDR) alone is no longer enough.
The Changing Face of Endpoint Risk
Modern endpoint risk doesn’t stem from one factor—it’s the result of a perfect storm of attacker sophistication, sprawling device footprints, and overwhelmed security teams. According to DBIR findings:
- Stolen credentials remain the top initial access vector, involved in 22% of all breaches—despite increased MFA adoption.
- Vulnerability exploitation is now the second most common attack vector, present in 20% of breaches, with edge devices and VPNs becoming primary targets.
- Infostealers are targeting both managed and unmanaged endpoints, often harvesting credentials from personal-use devices with weak governance policies.
Despite growing investments in EDR and extended detection and response (XDR), these technologies are fundamentally reactive. They work after an attack begins, relying on behavioral signatures, alerts, and human intervention to contain the damage. The result? Slower time to mitigation, higher breach costs, and greater operational risk.
Ransomware: Weaponizing the Endpoint
The resurgence of ransomware attacks underscores just how central endpoint compromise has become in modern cybercrime.
The DBIR reveals that ransomware was present in 44% of breaches, up from 32% the year before—a staggering 37% year-over-year increase. These attacks are no longer limited to data encryption. Today’s ransomware campaigns often involve double or triple extortion tactics, combining encryption with data exfiltration and public leak threats to maximize pressure on victims.
Endpoints are the initial—and often only—entry point required for ransomware operators to succeed. Once compromised, attackers can:
- Deploy ransomware and encryption payloads directly on the endpoint.
- Access sensitive files and map shared drives.
- Exfiltrate corporate data to use as leverage in ransom demands.
Small and midsize organizations are especially vulnerable: the report found that 88% of ransomware-related breaches affected SMBs, compared to 39% in larger enterprises. For under-resourced security teams, it’s not just about detecting ransomware—it’s about stopping it before it executes.
Traditional endpoint solutions fall short here. EDR tools may detect anomalous behavior, but often after encryption has already begun. At that point, the damage is done—and recovery hinges on the availability and integrity of backups, which attackers increasingly target or circumvent.
Preemptive technologies like Morphisec’s Anti-Ransomware Assurance Suite, powered by Automated Moving Target Defense (AMTD), neutralize ransomware payloads at the endpoint before they can execute, exfiltrate, or encrypt—offering true resilience in the face of a ransomware-laden threat landscape.
Why Reactive Defense Isn’t Enough Anymore
The DBIR reinforces that defenders are too often caught flat-footed:
- Attackers are exploiting known vulnerabilities faster than organizations can patch them, with a median remediation time of 32 days for edge device flaws.
- Credential exposure timelines are even worse—publicly exposed secrets like JWT tokens and API keys can sit unremediated for over 90 days.
- Unmanaged or BYOD endpoints are rife with risk—housing both personal and business credentials, these devices fly under the radar of traditional endpoint controls.
This gap between detection and action is where breaches take root. And as ransomware tactics evolve to include data exfiltration and extortion—even when backups are available—organizations face a new wave of extortion risk that reactive tools can’t preemptively stop.
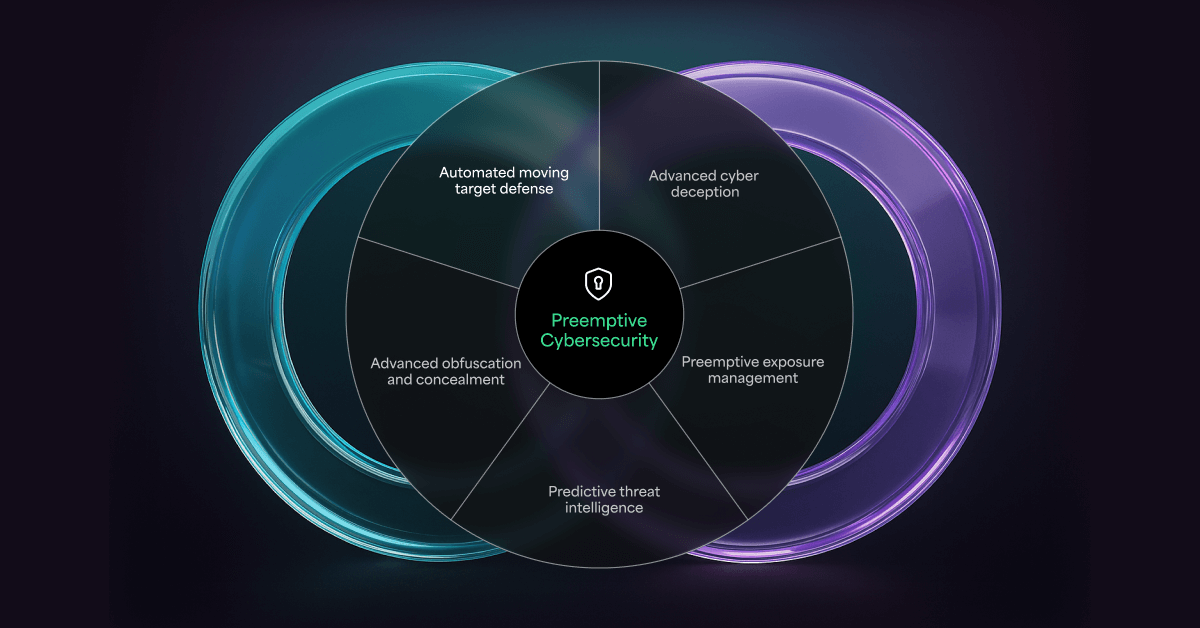
What Is Preemptive Cyber Defense?
As adversaries continue to outpace traditional detection systems, security leaders must shift from “detect-and-react” to “anticipate-and-prevent.” Preemptive cyber defense is precisely that—a prevention-first strategy that stops attacks before they execute.
Preemptive cyber defense proactively neutralizes threats before execution, rather than relying on detection and response. It achieves this through two complementary technologies:
- AMTD, which dynamically morphs runtime memory and attack surfaces to make them unpredictable and unexploitable. Additionally, AMTD blocks memory-based attacks—ransomware, zero-days, fileless threats—before they launch.
- Adaptive Exposure Management (AEM), which continuously discovers and prioritizes vulnerabilities, misconfigurations, and high-risk software. AEM also offers automated remediation guidance, reducing the attack surface in real time.
These capabilities are a departure from traditional endpoint security strategies as it means that Morphisec has:
- No reliance on signatures or behavioral patterns: It stops unknown and evasive threats that slip past EDR/XDR.
- Minimal operational overhead: Lightweight agents eliminate alert fatigue and require no manual triage
- Seamless integration: Designed to augment—not replace—existing tools like EDR, XDR, SIEM
- Clear ROI through risk reduction: Gartner analysts predict that by 2030, three-quarters of legacy detection technologies will integrate preemptive defense
Morphisec’s platform delivers preemptive defense through three tightly integrated tactical layers. First, Adaptive Exposure Management continuously identifies and hardens weak points in the environment, reducing the attack surface in real time. Next, Infiltration Protection dynamically morphs the attack surface, making it unpredictable and unexploitable—so attackers can’t plan or execute static exploits. Finally, Impact Protection neutralizes malicious payloads in memory before they can encrypt data or exfiltrate sensitive information, stopping threats at the earliest possible stage.
The Case for Preemptive Endpoint Security
To get ahead of today’s threats, security leaders must rethink the role of the endpoint—not as a passive threat sensor, but as a front line of active defense. That’s where preemptive endpoint protection comes in.
Our Endpoint Security Capabilities Matrix examines how most traditional EDR and antivirus tools only cover a narrow window in the attack lifecycle—and they do so after an attacker has gained a foothold. In contrast, preemptive technologies like AMTD eliminate the opportunity for exploitation altogether by dynamically morphing application memory and hiding vulnerable assets from attackers in real time.
Preemptive controls offer:
- Attack surface reduction: By preventing exploit execution before it occurs—regardless of patch status or known indicators.
- No reliance on detection or signatures: Blocking fileless and zero-day attacks that bypass reactive controls.
- Operational simplicity: Reduced alert fatigue and reliance on human analysts for triage and response.
- Business continuity assurance: By halting ransomware and exfiltration attempts before data is encrypted or stolen.
Morphisec enhances the capabilities of the EDR and XDR solutions you use today, fortifying your business’s endpoints, preventing attackers from reaching critical assets and protecting endpoints against ransomware.
Rethinking Endpoint Strategy: A Leadership Imperative
For CISOs and security leaders, the message is clear: the era of relying solely on post-breach detection tools is over. Defending endpoints in 2025 and beyond requires a mindset shift toward proactive, preemptive protection that neutralizes threats before damage occurs.
This doesn’t mean abandoning EDR or XDR—but it does mean augmenting them with prevention-first capabilities that close the gaps adversaries are actively exploiting. By integrating deterministic prevention into your endpoint stack, you can shift the balance of power—denying attackers the opportunity to gain access, escalate privileges, or extract data.
It’s time to stop chasing threats and start preventing them.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.