Ransomware in Healthcare: A Life-Critical Business Priority for 2026
Healthcare organizations measure risk differently than most industries.
When a manufacturer suffers a ransomware incident, the result is lost productivity. When a bank is breached, the outcome is financial loss. But when a hospital, clinic network, or medical services provider is hit by ransomware, the impact can be immediate and life-threatening.
Electronic health records go offline, diagnostic systems become unavailable, and critical care workflows grind to a halt. Surgeries and procedures get postponed, ambulances are diverted, prescriptions are delayed, and patients are left waiting while clinicians scramble to work on paper.
What begins as a cyberattack quickly escalates into an enterprise-wide crisis that touches every corner of the mission: delivering safe, timely care.
Understanding the True Cost of Ransomware in Human and Financial Terms
For C-level executives planning budgets and strategy for 2026, ransomware can no longer be viewed as just another technology threat.
It is a core operational resilience issue…one that directly affects revenue, regulatory exposure, and organizational trust. Modern ransomware incidents routinely force healthcare providers into difficult decisions about whether to pay escalating extortion demands simply to restore access to patient data and systems.
Even organizations that refuse to pay still face staggering secondary costs: emergency incident response retainers, forensic investigations, system restoration efforts, breach notifications, public relations campaigns, and potential legal action.
Regulators may launch HIPAA or privacy investigations, cyber insurers often raise premiums after a claim, and patients and partners question whether the organization can truly protect the sensitive information in its care.
The total economic damage of ransomware in healthcare is measured not only in dollars, but also in disrupted treatment and compromised safety.
The Shifting Nature of Healthcare-Focused Attacks
The problem is growing more severe as the threat landscape continues to shift.
Industry reporting shows that healthcare ransomware attacks are becoming more targeted and more strategic. In 2025, cybercriminal groups increasingly moved their focus upstream, attacking vendors, service partners, and managed service providers that support hospitals and large provider networks. By compromising one trusted technology supplier, attackers can gain access to dozens of downstream organizations at once.
At the same time, extortion tactics have become more aggressive.
Double and triple extortion (stealing data before encrypting it, then threatening to leak it publicly) is now standard practice. The adoption of AI-enabled tools by cybercriminals is accelerating reconnaissance and exploitation, allowing attacks to unfold at a speed no human security team can easily match.
These trends point to a difficult reality: the adversary ecosystem has recognized that healthcare downtime creates maximum leverage, and they are innovating specifically to exploit that fact.
Why Traditional Security Approaches Are No Longer Enough
Unfortunately, many of the security strategies healthcare organizations rely on were built for an earlier era.
Traditional defenses such as antivirus tools, endpoint detection and response platforms, and SOC monitoring services are fundamentally reactive. They are designed to identify suspicious activity after it begins and trigger alerts for analysts to investigate.
That model worked reasonably well when malware was simple and predictable. Today’s threats are neither. New attack frameworks are engineered to be stealthy, fileless, and highly customized. Droppers and loaders are routinely tweaked to appear legitimate. Command-and-control traffic is disguised to look like normal administration. And ransomware payloads are modified in real time to avoid known signatures.
Healthcare leaders are facing a generation of complex and undetectable threats that were created with one explicit objective: evade the very tools meant to stop them.
A Real-World Example: What ResolverRAT Taught the Market
Last year, Morphisec Threat Labs released research detailing exactly this kind of challenge.
Threat researchers identified a sophisticated malware variant called ResolverRAT that had begun targeting healthcare, pharmaceutical, and life sciences organizations worldwide. Unlike older commodity malware, ResolverRAT was purpose-built for infiltration. It abused trusted processes, established hidden persistence, and successfully bypassed multiple leading EDR and antivirus platforms during testing.
The threat was not theoretical. It was a real-world example of how attackers are developing customized implants to live quietly inside healthcare environments until the moment they choose to strike.
News outlets covering the Davita, Elenor Corp, and other healthcare breaches cited ResolverRAT as part of a broader surge in targeted ransomware activity.
For executives, the lesson was clear: even organizations with modern security stacks are vulnerable when prevention depends solely on detection.
Resilience in 2026 Requires a Preventative Mindset
This is why resilience in 2026 requires a new mindset.
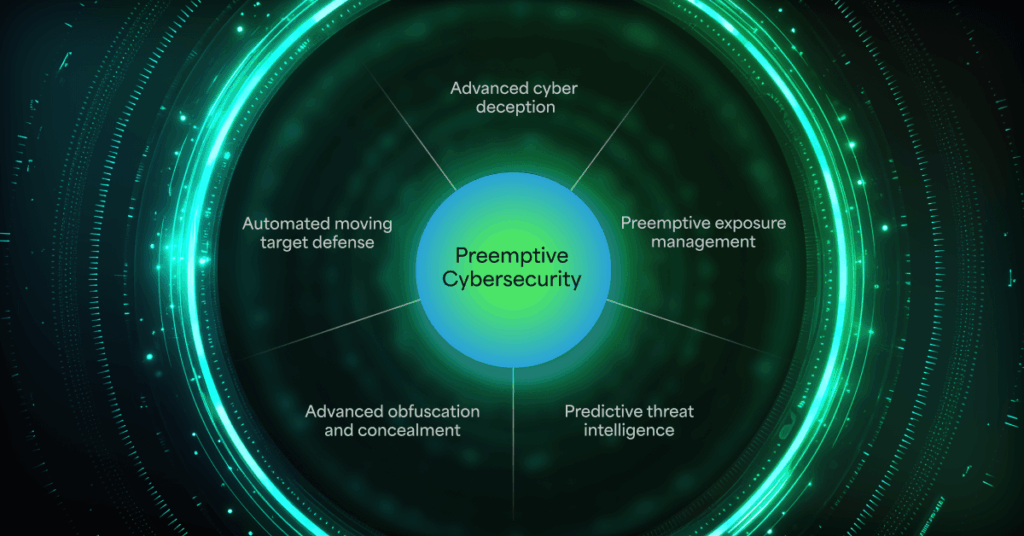
Cybersecurity in healthcare must start to look more like preventative medicine than emergency surgery. Leaders need to assume that some attacks will inevitably find a way in, and design their defenses around that assumption.
Deception platforms and technologies like Automated Moving Target Defense (AMTD) change the economics in favor of the defender by making endpoints and servers unpredictable to malware. Execution-level prevention focuses on stopping malicious code before it can encrypt files or disrupt systems, rather than hoping a SOC team notices it in time.
Continuous risk visibility helps organizations understand which identities, devices, and vendor connections represent the greatest exposure, so they can prioritize remediation efforts that actually reduce the likelihood of clinical downtime.
In practical terms, proactive security means investing in controls that keep care running even during an attempted breach.
Moving from Alerts to Assurance
Healthcare executives don’t need more alerts in 2026.
They need assurance. They need to know that ransomware protection is aligned with patient safety, revenue continuity, and regulatory compliance. That includes formal incident planning, regular tabletop exercises, and a commitment to technologies that prevent ransomware impact at the earliest possible stage.
It also requires realistic conversations about vendor risk and partner access, because that is where attackers are concentrating their efforts. The goal is not simply to pass an annual compliance audit. It is to build operational resilience that can be measured and validated over time.
How Morphisec Helps Protect the Mission
Morphisec is on a mission to address precisely these challenges.
Powered by patented AMTD technology, Morphisec prevents sophisticated malware and ransomware from executing, even when those threats evade traditional detection-based tools.
The Morphisec Anti-Ransomware Assurance Suite protects endpoints, servers, and network shares with proactive mechanisms that stop encryption attempts before they can disrupt clinical operations.
Importantly, this approach is designed to strengthen and complement existing healthcare security investments rather than replace them, adding a layer of resilience that scales across complex enterprise environments.
By focusing on prevention and impact protection, Morphisec helps organizations maintain uptime and protect patient care, revenue streams, and trust.
Preparing Preemptively for the Year Ahead
The coming year will bring continued pressure from ransomware groups targeting hospitals and the technology ecosystem that supports them. But 2026 planning gives healthcare leaders an opportunity to get ahead of that risk instead of reacting to it.
Organizations that translate cybersecurity spend into measurable mission assurance will be far better positioned to deny, deceive, and disrupt attackers before they threaten patient safety. Ransomware is not going away in 2026. The difference will be which healthcare organizations choose to prepare preemptively.
Morphisec has developed a comprehensive Healthcare Cybersecurity Checklist designed specifically for hospitals, provider networks, and healthcare technology partners. This concise, business-friendly guide helps executives and their teams evaluate readiness across critical areas including endpoint protection, identity risk, vendor access, backup resilience, and incident response planning.
It offers a clear framework to translate cybersecurity investments into measurable reductions in clinical and operational exposure. If you want to begin the new year on the right foot, download a copy of the Morphisec Healthcare Cybersecurity Checklist and use it to guide your security priorities, strengthen organizational resilience, and better protect patients and the mission you serve.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.