Breaking Down Ransomware Encryption: Key Strategies, Algorithms and Implementation Trends

Ransomware relies on strong encryption to lock victims out of their data – but not all ransomware encrypts files the same way. In this technical deep dive, we showcase our analysis team’s findings on how six major ransomware families implement encryption.
This post outlines how ransomware uses symmetric and asymmetric cryptography, presents typical encryption workflows, and compares implementations across families that include LockBit, Conti, Babuk, RansomHub, Clop, and Akira. We’ll also break down each family’s unique methods – from choice of ciphers, and performance optimizations including multithreading and intermittent encryption.
Ransomware Common Practices
For ransomware operators, the integrity of their cryptographic implementation is crucial. A flawed use of encryption — such as reusing IVs or exposing keys in memory — can lead to decryptable payloads or irreversibly damaged files. In some cases, these weaknesses allow researchers to recover data without paying or even derive keys from predictable values.
By analyzing the encryption implementations across multiple ransomware samples, we observed that despite differences in families and codebases, most share consistent behaviors across several key areas:
File Encryption
Ransomware often employs a combination of symmetric and asymmetric encryption techniques, where each file is encrypted with a unique symmetric key, which is then encrypted with the attacker’s public key to prevent recovery without access to the corresponding private key.
Files and Directories Enumeration
Ransomware typically scans the system to identify files and directories to encrypt. This includes both local file systems and remote or shared network resources.
Encryption Parallelization
All ransomware samples we analyzed implement multithreading to speed up encryption and minimize detection time. This technique allows parallel file processing across CPU cores and is preferred over multiprocessing due to lower noise and resource usage.
Encryption Optimization
To ensure maximum file coverage during encryption, ransomware often terminates a predefined list of processes and services, commonly those tied to databases, backup systems, and endpoint protection. By killing processes that hold locks on files (SQL Server, Exchange, VSS, etc.) the ransomware ensures it can encrypt as many files as possible without access restrictions.
Symmetric vs. Asymmetric Encryption in Ransomware
Modern ransomware almost always uses a hybrid of symmetric and asymmetric encryption. Symmetric algorithms (AES, ChaCha20, RC4) efficiently encrypt large data, while asymmetric algorithms (RSA, ECC) securely protect the keys.
Here’s how they both work in a typical ransomware encryption scenario.
The attacker begins by generating an asymmetric key pair unique to the victim. The public key is embedded into the ransomware executable. When the malware runs on the victim’s system, it generates a random symmetric key for each file, which is then used to encrypt the file content. The symmetric key is subsequently encrypted with the public key and appended to the end of an encrypted file, ensuring that only the attacker – who holds the private key – can decrypt the file.
Symmetric Encryption
Ransomware uses symmetric encryption to efficiently encrypt large volumes of data. For each file, it generates a unique file encryption key, often 256 bits in length, using a cryptographically secure random byte array. These per-file keys may incorporate additional components such as initialization vectors (IVs) or entropy sources like elliptic curve parameters, depending on the encryption scheme.
This key is then used with a fast symmetric cipher, such as AES or ChaCha20, to encrypt the file contents. Per-file key generation not only improves encryption reliability but also significantly increases cryptographic complexity, making brute-force recovery of the original data practically infeasible. Symmetric encryption is favored here because it is computationally efficient — a critical property when encrypting thousands of files in a short time.
Asymmetric Encryption (Secure Key Protection)
Asymmetric encryption is used to prevent victims from recovering files through key interception, since the attacker’s private key never lands on the infected system. However, because asymmetric algorithms are slow and more likely to trigger detection or disruption, attackers typically use them only to encrypt the per-file symmetric keys. These symmetric keys—often AES—are generated per file and used for actual data encryption due to their speed. By encrypting them with the attacker’s public key, only the attacker can decrypt them.
This hybrid model means that if a security solution can intercept the symmetric key before it is encrypted asymmetrically, there is a theoretical window to recover files. The critical question becomes: at what stage can defenders intercept or extract these per-file keys before they are irreversibly encrypted or erased?
Below is a snippet of the CLOP ransomware encryption routine:
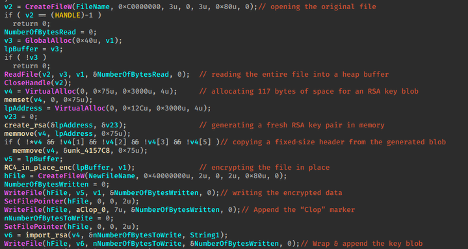
Let’s break down this ransomware hybrid‐encryption routine:
First, it opens the target file for reading and writing, then allocates a heap buffer large enough to hold the entire file and reads its contents into memory.
Next, it allocates two small in‐memory regions – one to receive a freshly generated RSA key blob (or, if that fails, a built‑in static blob) and another to hold the blob itself—and invokes a helper (create_rsa) to generate an RSA key pair and export its public‐key structure.
The file buffer is then passed through a symmetric encryption routine (RC4_in_place_enc) before being written out to a new file.
Afterwards, the code appends a “Clop” marker string and then calls import_rsa to encrypt the symmetric key with the RSA public key and appends that encrypted key blob as well.
Finally, it cleans up all allocated memory, closes handles, and deletes the original plaintext file, leaving behind only the encrypted payload, a ransomware marker, and an RSA‑protected key that only the private key holder can decrypt.
Encryption Features Analysis
The main objective of the analysis is to identify all encryption-related operations within the ransomware. One of the key sections to examine is the program’s initialization phase, where it may load a public key or generate an asymmetric key pair.
The second point of interest is the core encryption routine — typically a loop that processes and encrypts files matching specific extensions. This part of the code often reveals the chosen encryption algorithm, mode of operation, and how encryption keys are generated or derived.
The table below compares key encryption characteristics across the ransomware families we analyzed. This highlights both the common approaches and the unique innovations of each:
| Ransomware | Symmetric Algorithm | Asymmetric Key Exchange | File Encryption Strategy |
|---|---|---|---|
| LockBit 3.0 | AES-256 | RSA-2048 | Partial. Encrypt 16 bytes every 512 bytes (configurable) |
| Conti | ChaCha20 | RSA-4096 | Full encryption |
| Babuk | HC-128 | Curve25519 | Full encryption |
| RansomHub | AES-256 | Curve25519 | Partial. Encrypt 1 MB, skip 2 MB |
| Clop | RC4 | RSA-1024 | Full encryption |
| Akira | AES-256 | RSA-4096 | Configurable. Can encrypt only X% of each file |
Key Interception Evasion Techniques
Ransomware developers often implement advanced techniques to evade key interception during the encryption process. Using non-standard, non-monitored, and frequently non-documented APIs — This is the most common way to evade key interception.
- Encryption from safe mode — most solutions do not operate in safe mode.
- Encrypting from access point — a dedicated appliance or non-monitored or exploited perimeter device
- Hypervisor encryption — the most common is encryption of the ESXi hypervisor file system.
- Wipers — even if the keys are intercepted, the files cannot be recovered.
Potential Risks with Recovery Technology
While recovery technologies can assist in responding to ransomware, they also introduce several security and operational risks that must be considered.
- Will the keys be exported? – GDPR and PII exposure risk
- Will the keys be encrypted by the ransomware?
- Can all processes be monitored without impacting performance?
Summary
Morphisec is preparing to launch a new recovery capability within the next two months. While acknowledging that not all encrypted files can always be recovered, Morphisec’s deterministic prevention approach—driven by its Automated Moving Target Defense (AMTD) technology—is purpose-built to stop ransomware before damage occurs. In rare cases where limited file encryption does take place, Morphisec will equip organizations with the necessary tools to minimize risk and support recovery.
Ultimately, effective ransomware defense must prioritize prevention as a core part of both containment and eradication strategies. Book a personalized demo to learn more about Morphisec’s Anti-Ransomware Assurance Suite and see it in action.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.




















